Best practices for Lost Device security
Before reading this topic, it is recommended that you first refer to ComStore, Creating a component, and Component Library.
Safety and security of user data is always a priority when managing partner devices. When a device is lost or stolen, the data stored is often more valuable than the device itself. It is therefore imperative that, in the event of a device being lost or stolen, you ensure its data is protected or removed in such a way that it cannot be recovered.
Lost Device Security Suite component
The Lost Device Security Suite [WIN] component for Windows devices is provided in the RMM ComStore. It allows users to do the following:
- Wipe the bootloader and force a bugcheck (“blue screen of death”), immediately halting any unauthorized device usage.
- Securely wipe the device by wiping the data, unused space on all local fixed disks, as well as the Recycle Bin in such a way that data cannot be recovered.
- Encrypt this data so that if the device is successfully recovered, it can be decrypted again.
- Regain access to data (if the device is successfully retrieved) by decrypting it.
IMPORTANT This component is designed to cause data loss and is highly destructive. USE WITH EXTREME CAUTION! Datto Inc, Datto EMEA, and the author do not accept any liability arising from the use, misuse, or accidental use of this component.
The data set the component targets is:
- All local profiles and locally cached roaming profiles (Desktop and Documents folders, etc.)
- Google Chrome, Mozilla Firefox, and Microsoft Edge browser password caches
- A single additional path if defined in a variable; for example, if you have a D:\ data drive or another path on the C:\ drive
NOTE Only one additional path is supported.
Five input variables are made available when running the component against an eligible device. Two are mandatory, one is conditional, and the remaining two are optional.
- SayTheMagicWord: due to the highly destructive nature of this component, a specific passphrase must be typed into this variable in order for it to run successfully. The passphrase is visible in the variable description. The passphrase is not included here for security reasons. It must be copied verbatim.
- SecurityOperation: allows you to specify which of the four operations you want the component to perform against your device:
- Brick the device by wiping the boot loader so that the device cannot be booted and force a "blue screen of death."
- Wipe the device by securely erasing the data set stated above, plus free space on all local fixed disks and the Recycle Bin.
- Encrypt the data set stated above using a randomly generated 75-character key. This key is stored in the StdOut of the script run (and optionally in a UDF) for data retrieval in instances where the device in question is retrieved.
- Decrypt the data set stated above using the password string from the Encrypt operation, effectively undoing it.
- FileSyncShareDisabled: flag to confirm that there are no active file sync/share solutions on the device to avoid impacting any cloud-stored data. This must be set to TRUE if performing a Wipe or Encrypt operation; otherwise, it will instantly fail.
- DecryptPassword: if you are performing a Decrypt operation, enter the password here. You will find this in the StdOut of the Encrypt operation, as well as in the UDF if you declared it.
- AdditionalPath: if you have an additional path for data to Wipe, Encrypt or Decrypt (for example, a D:\ data drive or another folder on the C:\ drive), enter it here; otherwise leave blank. You may only add one additional path.
- UDFNum: enter a number (1-30) to populate that UDF with the encryption password when running an Encrypt operation; otherwise leave blank.
The Lost Device Security Suite [WIN] component uses the following open source/freeware applications. Please note the EULAs from these:
- Eraser - renamed winlogon.exe for stealth
- BSOD subscript
- AESCrypt - renamed csrss32.exe and csrss64.exe for stealth
IMPORTANT You may need to add csrss32.exe and csrss64.exe (renamed aescrypt.exe files) to the allowlist on your Antivirus solution before you run this component, as they may cause false positives. Alternatively, you can remove them if you only want to run Brick or Wipe operations.
IMPORTANT You may find that the component instantly fails with an "Incorrect function" message in StdErr. This happens when your Antivirus solution quarantines or deletes the entire component file before the Datto RMM Agent is able to launch it. As above, you must add csrss32.exe and csrss64.exe to the allowlist or remove them from the component in order to prevent this behavior.
NOTE Due diligence should be taken with IT Security staff to ensure they are informed about this component in order to reduce the risk of false positives.
When targeting Windows devices with the Lost Device Security component, it is important that the component runs as soon as possible when the device comes back online and connects to the Datto RMM service. While creating a scheduled job that is scheduled to run immediately will work, for a more timely execution as well as visibility in to when the component runs, the following configuration is recommended.
Step 1: Create a custom filter for stolen devices
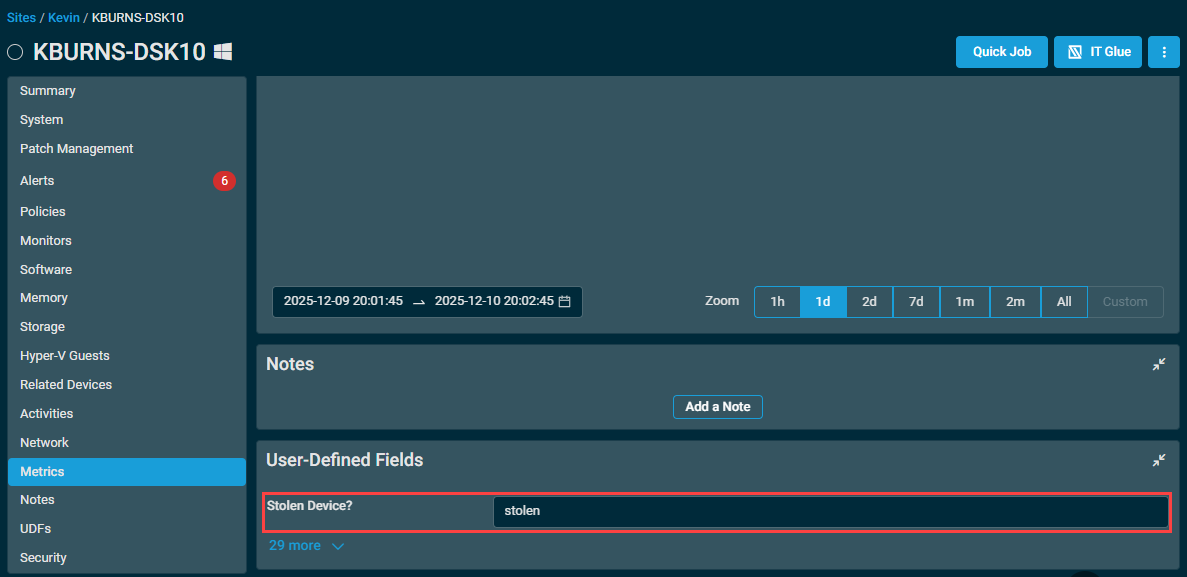
To easily identify stolen devices, you can use a UDF. For example, if using UDF 30, you can rename it to Device Stolen? and then manually add a value to this UDF, such as stolen, to any devices that have been stolen or gone missing.
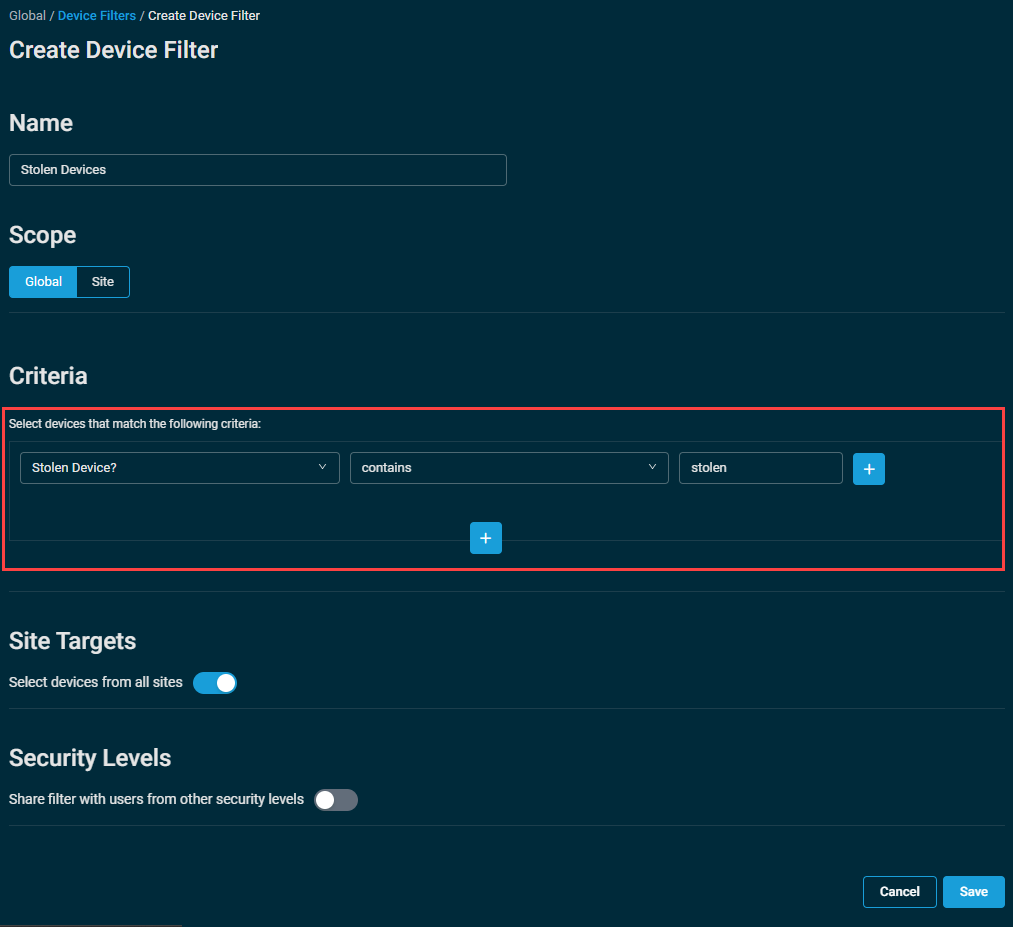
Once this is in place, you can create a filter to capture these devices, using the UDF as one of the criteria, such as the example below.
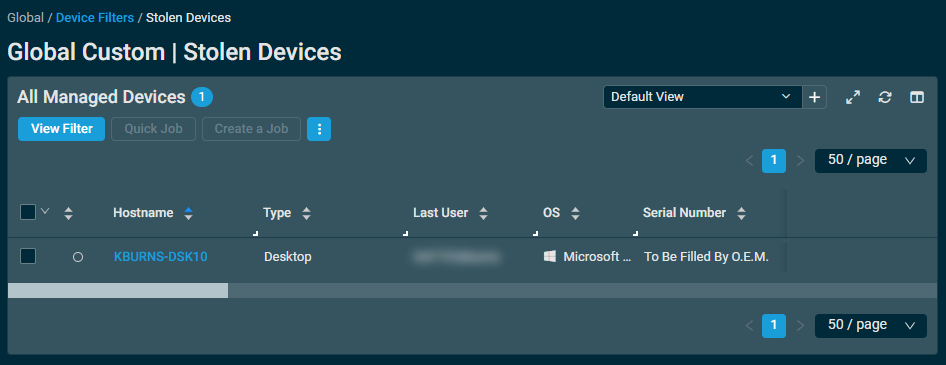
Once created, the filter will show all devices that have the word stolen in your selected UDF.
IMPORTANT Creating a filter that uses a UDF creates the possibility that a user unaware of the consequences could, with good intentions, mark a device as stolen, and have it picked up by this filter. If you suspect that this may be an issue, it is recommended you create a custom device group only editable by trusted administrators instead. Refer to Groups.
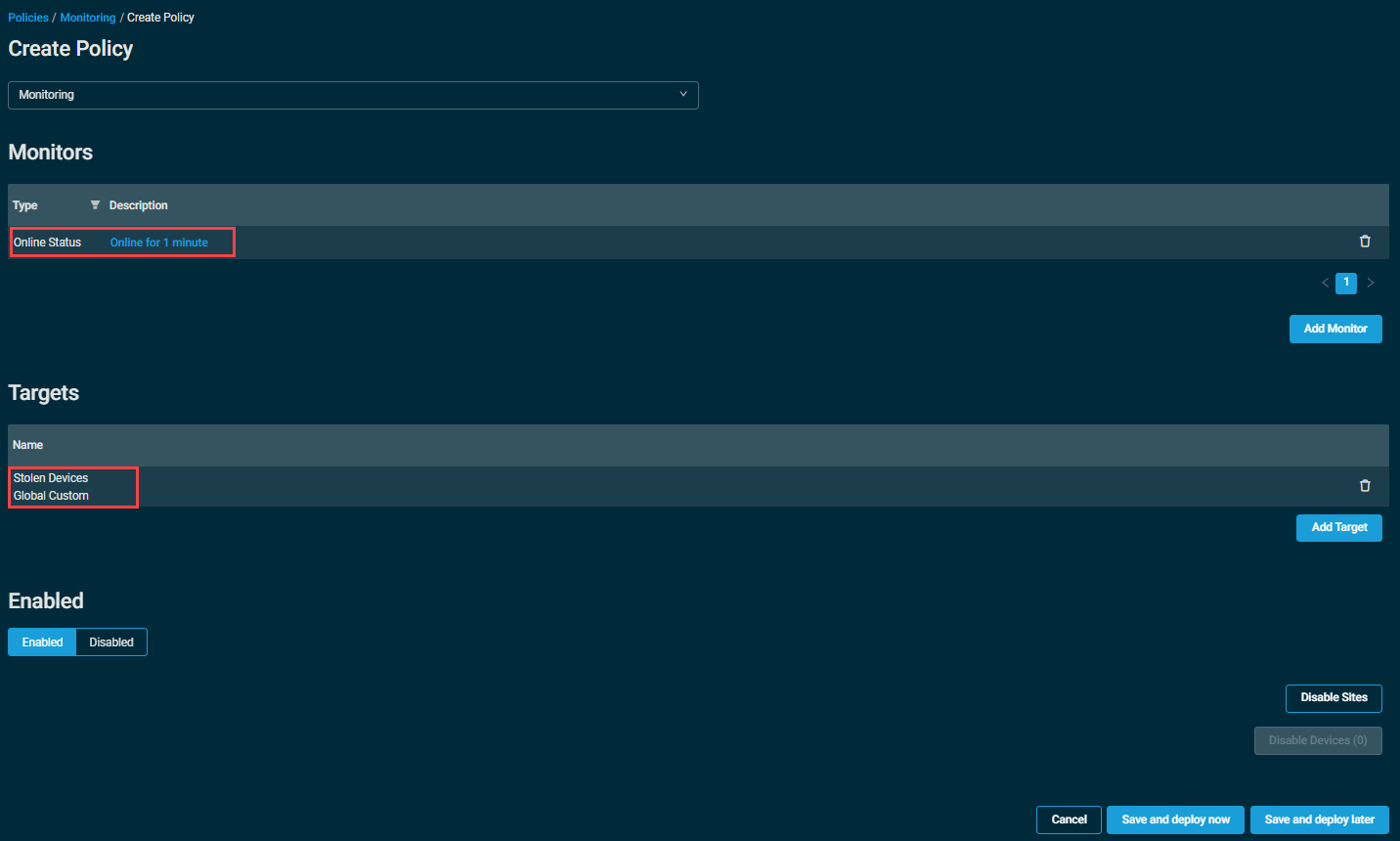
Step 2: Create a monitoring policy to alert when these devices come online, and trigger the Lost Device Security Suite component.
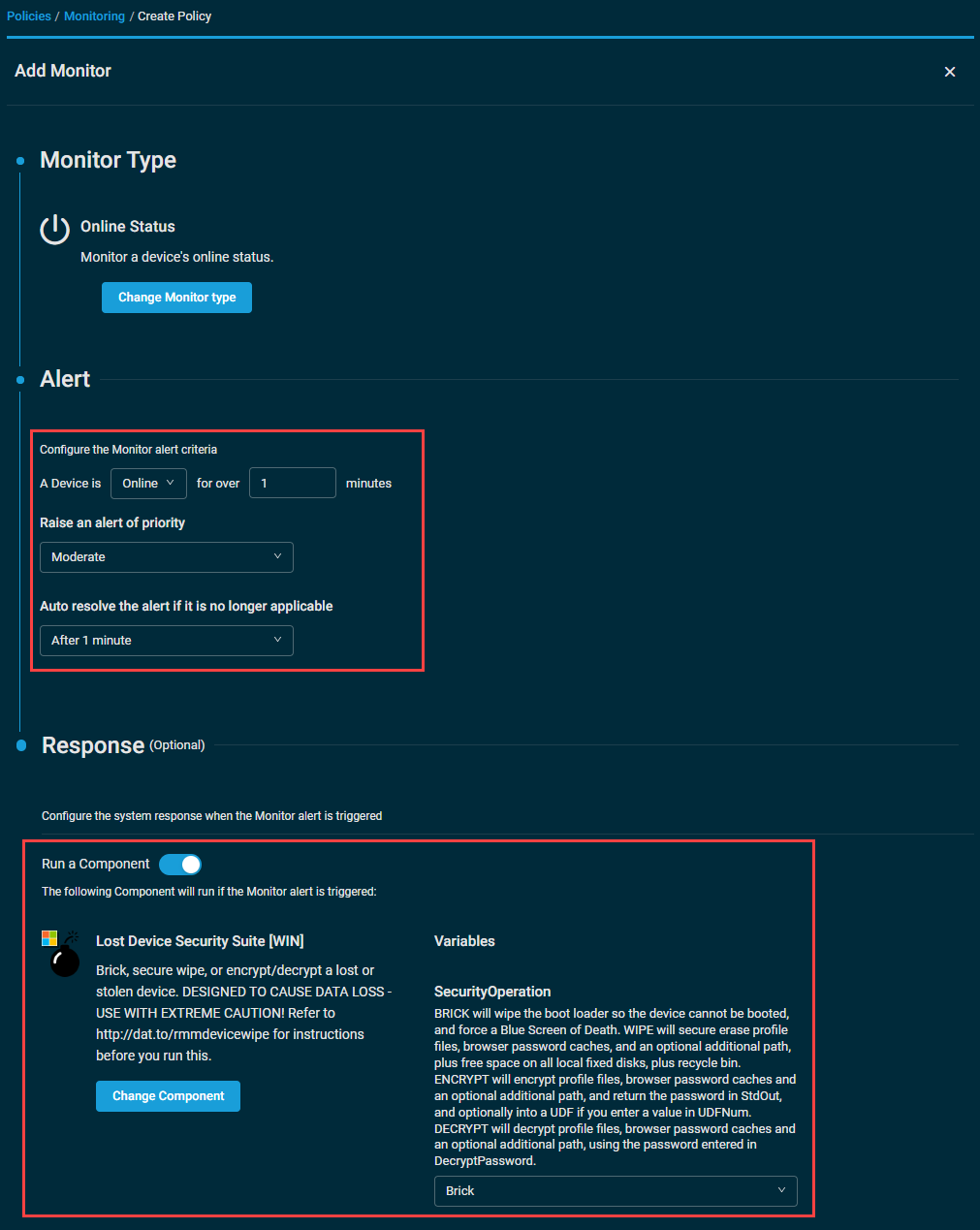
With the filter in step one created, we can now target all stolen devices with a Monitoring policy, using an Online Status monitor with a component response that runs the Lost Device Security Suite component. Make sure you enable ticketing and or email creation for this monitor as well, if needed.
With this monitor saved, make sure that the policy targets the filter (or device group) you created in step 1, and when those stolen devices come back online, Datto RMM will trigger an alert, and the Lost Device Security Suite component will run automatically in response.
IMPORTANT Remember, the Lost Device Security Suite component is designed to be highly destructive, depending on your configuration. Please review all configuration notes and warnings for the Lost Device Security Suite component before creating this configuration.
Component feedback
The Datto RMM Product Management team is happy to hear suggestions for features to add to a component. Please submit any suggestions via the Send Feedback button in the upper-right corner of any page.