The FireEye Countermeasure Scanner component
The FireEye Countermeasure Scanner component uses the YARA file scanner from VirusTotal, alongside a definition set produced by FireEye, to detect files that match the signatures of tools stolen from them in the hack of their Red Team on December 8, 2020.
By using this component, you can ensure that your workstations do not contain traces of the stolen code and thus, by association, that a bad actor has not attempted to leverage the stolen FireEye code to gain access to your infrastructure.
Special considerations
- The Microsoft Visual C++ redistributable is required. You can find an installer in the Datto RMM ComStore.
- The component only runs on Windows systems. PowerShell 2.0 is required. (Windows 7 ships with PowerShell 2 out of the box.)
Adding the component
The component is available free of charge for all Datto RMM users. For assistance installing agent components in Datto Cloud Continuity, refer to Deploying the Cloud Continuity agent via Datto RMM.
- In Datto RMM, navigate to the ComStore and download the FireEye Red Team Countermeasures Scanner [WIN] component.
- Click the Add button next to the component to add it to your Component Library.
Using the component
The component will scan when you run a quick job. Refer to Quick jobs to learn more about running quick jobs and making components available for them.
Setting the scan scope
When running the component, it will let you set the scope of the scan (usrScanScope). The values are the following:
- Scan all EXEs in memory: This short scan should conclude in five to ten minutes. This option only scans files that are running at scan time.
- Scan all EXEs on home drive: This scan may take an hour or more, depending on how full the home drive is.
- Scan all EXEs on all fixed and removable drives: This scan's duration will scale according to usage.
- Scan all EXEs on all drives: As above. This will also check network drives.
Handling scan results
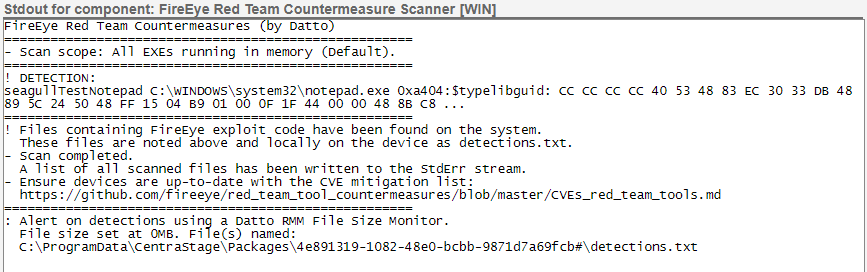
The component shows the results in the Datto RMM interface. Clean runs will show a successful status. Infected or problematic runs will give a failed status.
If the component discovers an infected file, it will produce a file called detections.txt in addition to showing the failure status of the job run. The job run's StdOut gives instructions on how to monitor for this. Run the component on one device (scan running EXEs). The StdOut will show a file path. Copy this path into a Datto RMM File Size monitor (not a component) with the alert threshold set at 0MB.
You can apply this monitor to all devices on which the Countermeasure Scanner is being run in order to produce an alert if the component finds an infection.