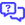Best practices for measuring devices against a security posture
With an ever-increasing number of threats targeting endpoints, it’s useful to be able to measure security compliance, patching status, antivirus status, and so forth. Datto RMM offers built-in widgets that enable MSPs and internal IT departments to quickly gather the relevant security information and display it on an easy-to-use management dashboard. Refer to Dashboards and Widget Library.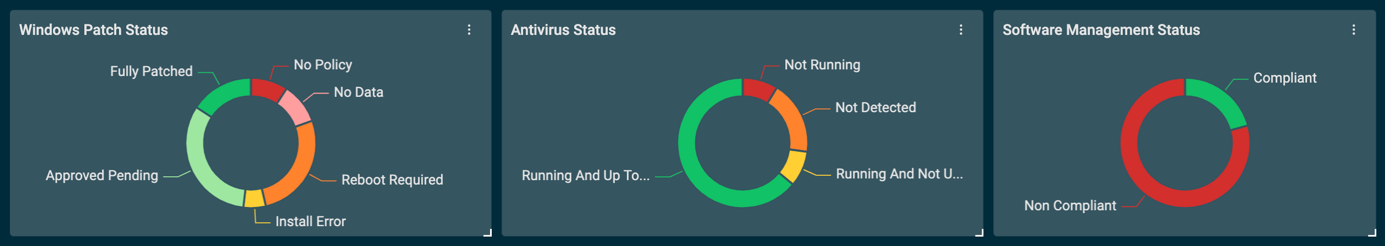
Individual widgets serve as isolated snapshots of security data. A single device may appear in multiple widgets or have multiple compliance failures, for example. This is why a defined security posture can become a useful measure.
A typical security posture statement may include the following:
- All endpoints must be fully patched.
- All endpoints must have either Datto AV or Microsoft Windows Defender installed.
- All antivirus software must be running and up to date.
- All endpoints must be compliant with our Software Management policy.
While the preceding four-point statement is reflected in the example in the next section, other measures you may want to consider include requiring all endpoints to have an EDR solution installed, a VPN client or a web filtering application, or encryption or a local firewall.
Datto RMM can be used to measure your devices against your security posture and display the devices that are not compliant. In our example, compliance is achieved when a device meets the requirements of all four statements. If any statement is not true, the device is considered not compliant.
You can display the devices that are not compliant on a dashboard using a filter widget.
Building the compliance widget
First, you'll build a filter to measure the devices against your security posture statement. If you require additional compliance checks, you will need to incorporate them in your filter.
Create a global device filter, remembering to use the OR statement rather than the AND statement. Refer to Device filters.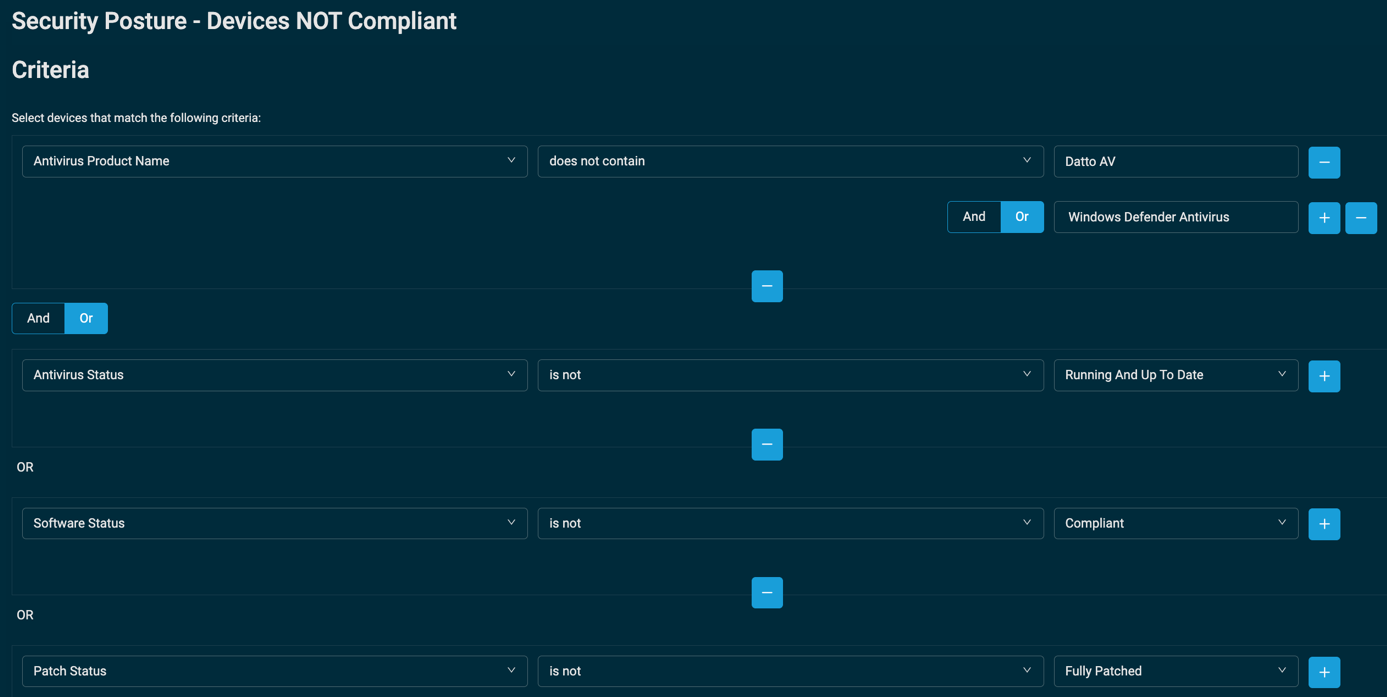
This criteria will filter for devices that are not compliant (i.e., the absence of certain criteria), such as devices that are not fully patched, do not have the required antivirus software installed, and so forth.
Once the filter is created, it will produce a list of devices that don’t fulfill your security posture statement. Refer to List of devices.
To make this view more relevant, you can use the Column Chooser to display the security-related fields. Refer to Column Chooser - Devices.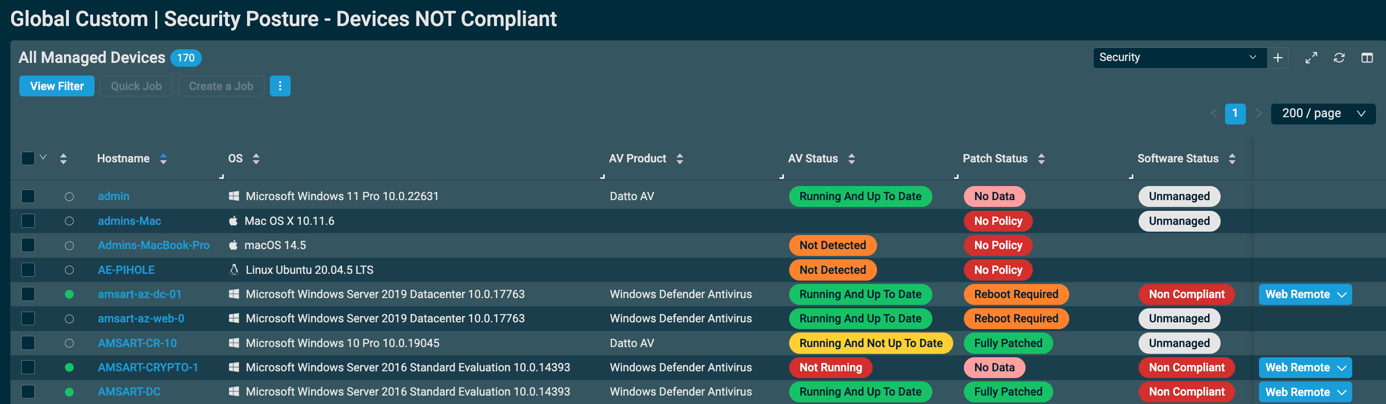
For information about saving specific device list configurations for use in the future, refer to Saving multiple list views in Devices.
Now, you can add your filter to a dashboard as a filter widget. Refer to Best practices for creating custom dashboard widgets.
Conclusion
Datto RMM not only provides you a way of highlighting devices that don’t meet your individual checks, are not fully patched, have out-of-date antivirus software installed, and so on, but you also have a way of seeing the devices that do not comply with your overall security posture statement on a single dashboard.
These devices would represent the highest threat in terms of endpoint security and should be addressed first. Your overall goal should be to reduce the number of non-compliant devices to as close to zero as possible.