Microsoft 365 Integration troubleshooting
This topic outlines common Microsoft 365 synchronization issues in Datto RMM and guidance on how to resolve them.
To learn about the integration with Microsoft 365 and Datto RMM, refer to Microsoft 365 Integration.
Tenant sync issues
Expand the drop-down menus to uncover explanations and solutions for the following issues:
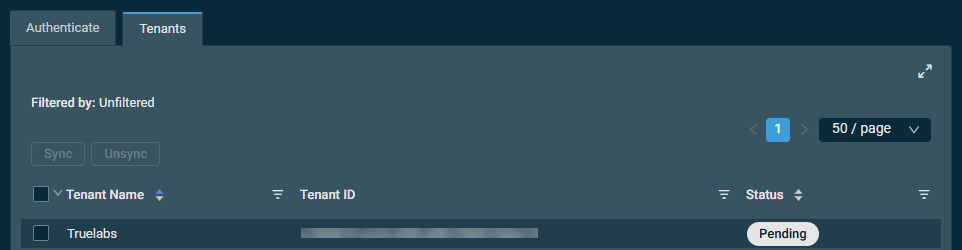
If a Microsoft 365 client tenant has not been granted the required GDAP permissions, Datto RMM shows the Failed status for that tenant.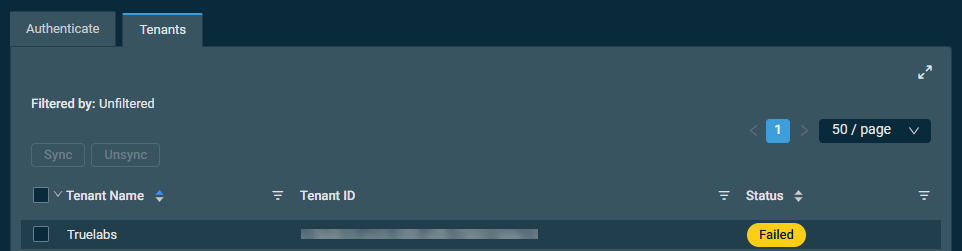
Steps to resolve in your Microsoft Partner Center account
- Navigate to the Microsoft Partner Center customer list.
- Click the name of the applicable customer in the list.
- In the left navigation menu, click Admin relationships.
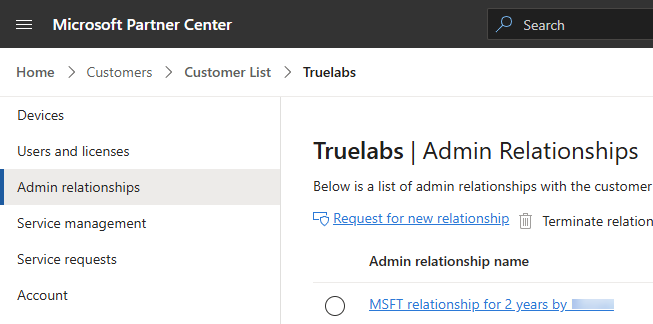
- Check for the following configurations:
- In the GDAP relationship, ensure that Global Reader and Application Administrator roles are included (Global Administrator also suffices).
- In the GDAP relationship, check which security group has the required permissions.
- In your own Microsoft Entra tenant, ensure the account used for partner access in Sync 365 is in the relevant GDAP security group.
Within about 30 minutes of placing the account in the correct group, the status should no longer show Failed.
Steps to resolve in your Microsoft Partner Center account
- Navigate to the Microsoft Partner Center customer list.
- Click the name of the applicable customer in the list.
- In the left navigation menu, click Admin relationships.

- Ensure that sufficient roles (Global Administrator, Cloud Application Administrator, or Application Administrator) and consent have been granted. Follow the steps from Microsoft to grant admin consent. For navigation instructions, refer to this section.
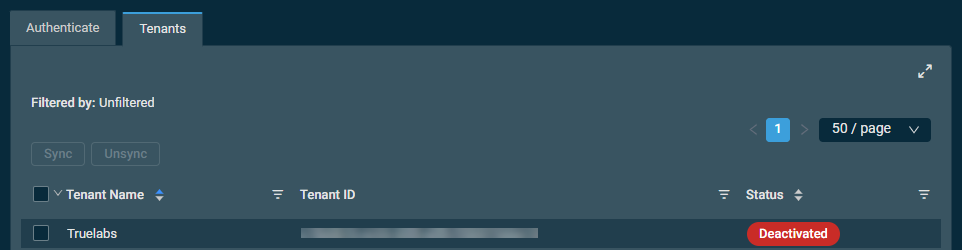
When conditional access policies are in place, tenants may not appear in Datto RMM.
Potential resolutions
- Ensure the correct tenant ID is entered in Datto RMM to authenticate the integration.
- Ensure GDAP is correctly configured for the tenant, and ensure the security group is granted one of the following roles: Global Administrator, Cloud Application Administrator, or Application Administrator.
- If application logs in Microsoft Entra are selected, you may see the following error details (which causes this issue):
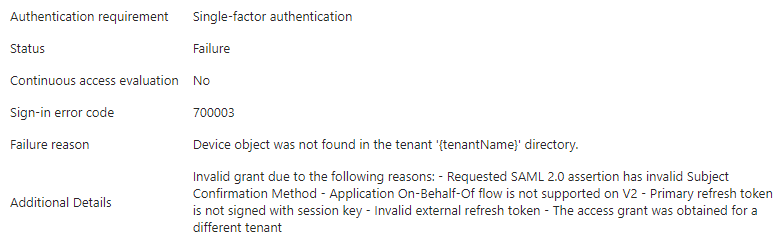
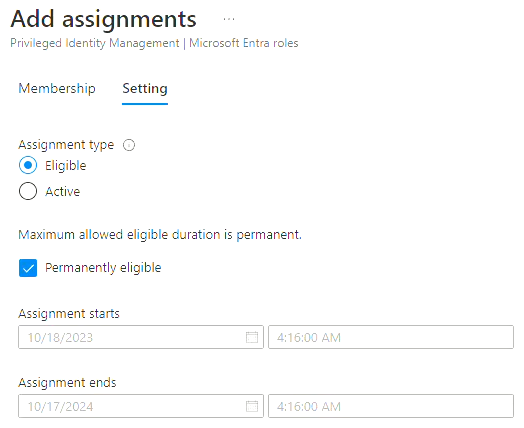
- Ensure Privileged Identity Management has been configured as follows:
- From the left navigation menu in Microsoft Entra, navigate to Identity > Identity Governance > Privileged Identity Management.
- In the Manage section on the Privileged Identity Management page, click Microsoft Entra roles.
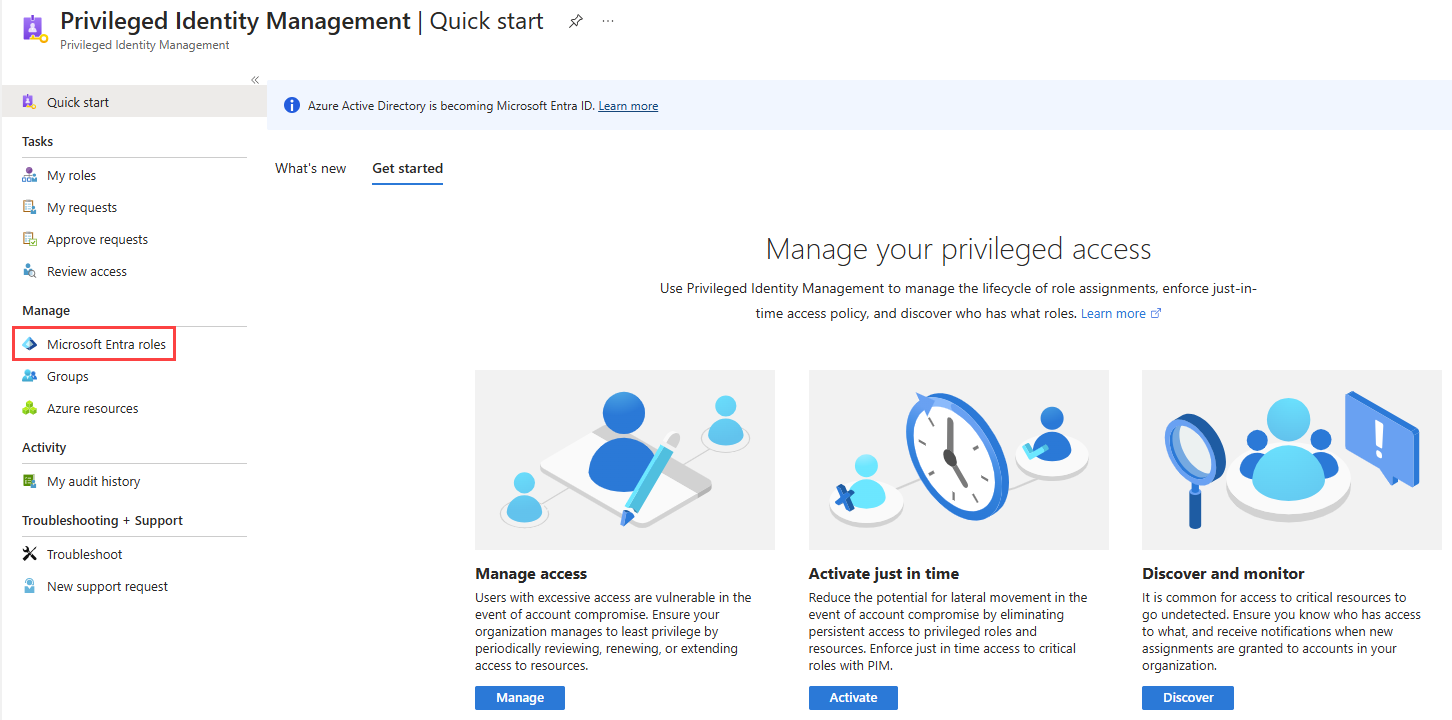
- In the Manage section, click Roles.
- Click the Global Administrator role. Check that the role shows No Results.
- Click Add Assignments.
- In the lower-left corner of the page, click No member selected.
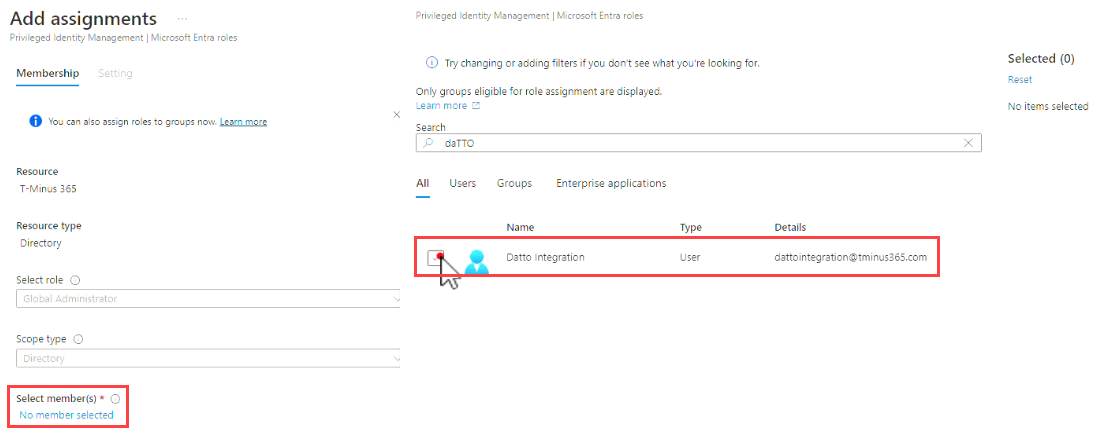
- Search for your integration user, select the check box, and click Next.
- Configure the following settings and click Assign: