Infrastructure and security
Datto RMM enables IT support organizations to monitor and manage multiple remote computers over any network, bringing visibility and control to the service provider. The solution has been built for organizations supporting IT over public networks, so careful consideration has been given to the infrastructure and security of the product.
IMPORTANT Several elements of Datto RMM will be flagged as malicious based off of behavioral analysis by Next-Generation Antivirus (NGAV), such as SentinelOne, CrowdStrike, and so forth. This flagging is the result of Datto RMM's deep integration within managed devices and ability to control most or all aspects of systems, which is expected functionality of Datto RMM. You may want to explore allowlisting the agent's executables (that is, AV exceptions) if notifications of this behavior become an issue. Some files typically impacted include CagService.exe, AEMAgent.exe, RMM.WebRemote.exe, and update files. Refer to Folders and file paths used by Datto RMM.
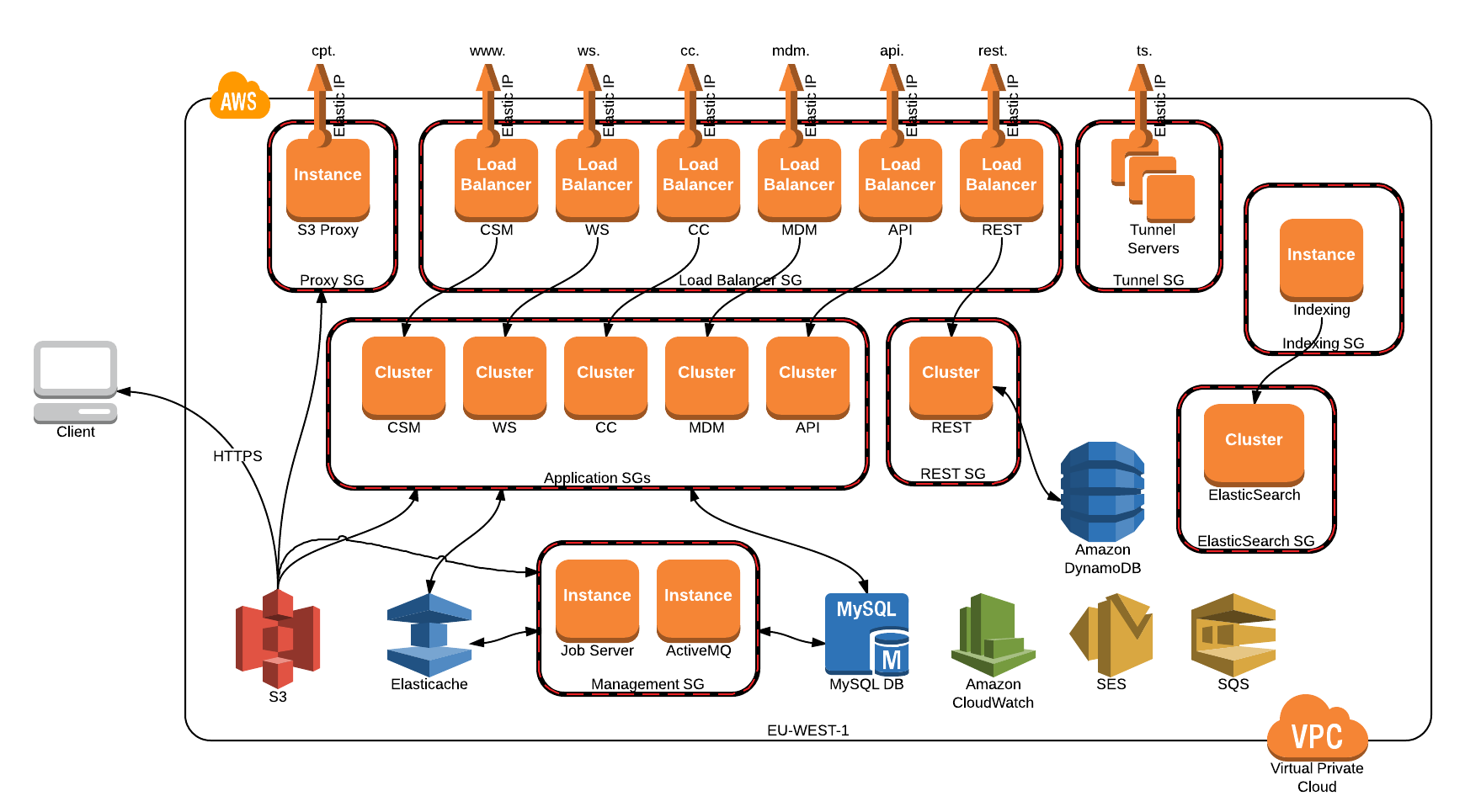
Datto RMM operates on multiple resilient, high-availability, scaling platforms hosted within Amazon Web Services (AWS). These platforms exist and span a number of different AWS Regions to provide increased performance for partners around the globe. At present, the core platforms are hosted in the EU-WEST-1 (Ireland), US-WEST-2 (Oregon), US-EAST-1 (Virginia), and AP-SOUTHEAST-2 (Sydney) regions, with additional servers in AP-SOUTHEAST-1. Refer to Datto RMM platforms.
All communication that needs to travel between AWS Regions is performed via secure SSH Tunnels or HTTPS connections.
To achieve the required levels of resilience and scalability, Datto RMM servers are separated into five partner-facing services. The services are separated as follows:
- Web interface
- Control Channel (CC): A permanent connection established with all connected devices to facilitate low latency event and command communication.
- Web Service (WS): A stateless SOAP Web Service for Agent-to-platform communication.
- Monitor Service: A stateless REST Web Service for Agent-to-platform communication.
- API: A REST API for programmatic interaction with the platform.
Availability zones
Within each AWS Region, there are two or more Availability Zones. These zones are distinct locations within a region that are engineered to be isolated from failures in one another while still providing high performance, low latency inter-AZ connectivity. By hosting across multiple Availability Zones, Datto RMM is able to ensure that a failure in a single Data Center does not affect the availability of a platform.
Load balancing
All of the core platform services (web interface, CC, WS) exist as multiple servers within AWS and are themselves only accessible through dedicated Load Balancers. For the web interface, this load balancing is provided via the use of the Amazon Elastic Load Balancer service, while the CC and WS servers use dedicated Load Balancing instances. By spreading these load balancers across multiple availability zones and using DNS Round-Robin, we are able to ensure high availability, scalability, and performance of the platform. Servers can be commissioned and decommissioned as required with no impact to the service itself.
Server instances
Datto RMM uses Ubuntu for the base operating system of the server instances, hosted within AWS Elastic Compute Cloud (EC2). The version used has been specifically prepared and hardened for use in AWS by Canonical Ltd, the provider of the Ubuntu platform. Server instances are launched from prebuilt and tested machine images to ensure 100% consistency. These machine images are backed up to the AWS Simple Storage Service (S3), which has 99.999999999% (11 9’s) durability. Servers are stateless in that they do not store any persistent data, allowing them to be replaced on demand, negating the need for individual server backups, and ensuring that the failure of a server does not result in a loss of partner data.
File storage
All components uploaded to the Datto RMM platform are uploaded to buckets within S3. This ensures durability of data and also provides a highly available mechanism to securely serve these files back to devices across the globe as required. By using S3, we ensure that components can be instantly provisioned to any number of devices over a high bandwidth connection, not tied to a static number of background instances.
Firewalls
AWS EC2 instances are, by default, closed for ingress via the use of configurable security groups. By default, Datto RMM core servers are only accessible via dedicated Load Balancer or SSH Tunnel instances, which exist in separate security groups. This means that access to these instances is either via 443 for HTTPS or secure TCP traffic from Load Balancers, or via SSH Tunnel on port 22 through a dedicated SSH Instance. Any servers which do not require external connections are therefore locked down and accessible only on port 22 via first connecting to a controlled SSH Instance.
This security group concept extends to Amazon's Relational Database Service (RDS) and means that the Databases that back the platforms are not externally accessible; instead, they are only open to connections from specific security groups.
Auto scaling
In times of high load, Datto RMM servers can auto scale, adding additional server resource automatically to areas of the system that are most heavily utilized. Additional servers can be automatically brought online and added to the load balancer as required. Conversely, auto scaling can remove excess processing in times of minimal load. Additional server instances are can be provisioned in under 60 seconds and can ensure a consistent level of service for users despite platform load.
Database
Datto RMM is underpinned by a high availability, relational database service (RDS) for MySQL, which is distributed across two availability zones in a primary-secondary arrangement. In the unlikely event of a database failure, Datto RMM will automatically fail over to the secondary database in the other availability zone within a matter of minutes. RDS automatically patches the database software and backs up the database, storing the backups for a user-defined retention period and enabling point-in-time recovery.
Data protection
We work hard to ensure the security and protection of any data stored on the Datto RMM platform. For sensitive information, in addition to access controls and platform penetration testing, this also includes encryption using the AES/CBC/PKCS5Padding Cipher before it is transferred to the Datto RMM Database.
Partners should also be aware that data is never stored outside of the platform region that they select when signing up for the service. For partners on our EU platforms, this means all data is stored in Ireland. For partners on US Platforms, this currently means all data is stored in Virginia or Oregon. For partners in APAC, this means all data is stored in Sydney. Where new platforms are added in the future, the location of the corresponding data center will be announced to allow partners to make appropriate decisions when reviewing concerns such as the Data Protection Directive.
Platform monitoring
In addition to the instance monitoring services provided by AWS CloudWatch, Datto RMM uses a number of services in order to provide effective monitoring of platform health and metrics. For example, core platform services are monitored for health and throughput using custom metrics that are then pushed to CloudWatch, the NewRelic Application, Server Monitoring Service, and Graphite. A custom metric-gathering code is also deployed to each server.
NewRelic and our own custom metrics provide us with near real-time feedback on platform load, allowing the system to scale on demand when required and alerting us to potential problems or service outages. 24/7 response is ensured through the use of PagerDuty and a robust and well-practiced escalation procedure within Datto RMM.
By monitoring the platforms in this fashion, coupled with the log aggregation services currently being deployed across the estate, Datto RMM is moving toward being able to identify, pinpoint, and resolve potential partner issues before they become apparent to the end user with both predefined intelligence- and exception-based alerting.
Platform status
Current platform status, health, and issues are pro-actively reported to end users via a comprehensive Status page. Not only does this give users a way of being alerted to potential platform issues and notification of upcoming planned maintenance, it also provides a complete history of issues that have affected the platform, giving new and existing partners insights into platform stability and response times.
Platform stability
Datto RMM performs regular stability testing on the platform, using automated tools to terminate core servers and to ensure the platform is able to both continue functioning and gracefully recover the affected services without the need for manual intervention.
Through this kind of testing, we can ensure that not only has the platform itself been effectively engineered to ensure resilience and high availability, but that in the event of an unexpected issue, all the core staff within Datto RMM are able to execute a well-practiced response.
Global relay servers
Despite platforms themselves being located in specific regions, all inter-Agent connectivity takes advantage of a network of tunnel servers, with the Agents intelligently selecting their closest and healthiest server through which to establish a connection.
Partners who do not wish to utilize this network can select a specific server to use, with IP Addresses of those and the other endpoints. Refer to Allowlist requirements for IP addresses and URLs.
Datto RMM AWS architecture
Figure - Datto RMM Platform Infrastructure – This is a high level diagram and may not represent the full set of services and servers.
Web interface security
|
Encryption |
AES-256, 256 Bit keys. The connection supports TLS 1.2. |
|
Passwords |
Strong passwords required: minimum of 9 characters. |
|
Accounting |
Session activity logged to system level log files and audit trail database. |
Two-factor authentication
A Two-Factor Authentication mechanism based around the use of Time-Based One-Time Passwords (TOTP: http://tools.ietf.org/html/rfc6238) is required in the Datto RMM web interface. This allows any user with a smartphone the ability to use that device as a second step in the authentication process, requiring them to provide a Username, Password, and token generated on their phone to log in to the website.
By enforcing TOTP across all users in their account, partners can ensure that a compromised password doesn’t lead to a third party being able to access the web interface.
Agent and Web Remote security
|
Encryption (Agent to server) |
TLS 1.2, TLS 1.3 |
|
Protocol |
HTTPS / TCP 443 |
The following processes are digitally signed with a certificate from Datto, LLC:
- CAGService.exe
- AEMAgent.exe
- gui.exe
- RMM.WebRemote.exe
- RMM.RTO.Proxy.exe
- RMM.RTC.Proxy.exe
NOTE All .dll and .exe files built for the Windows agent are now signed, with the exception of third-party libraries.
Internet Protocol
The Datto RMM Agent communicates with the platform using the IPv4 protocol.
NOTE IPv6 connections are not supported at this time.
Stateful Packet Inspection
It is strongly recommended that any Stateful Packet Inspection be turned off for access to any centrastage.net address, and that all attempts possible are made to guarantee that TCP connections to the cc.centrastage.net addresses are not terminated in cases of inactivity (these connections may be inactive for up to 180 seconds at a time if no client activity is detected).
VNC
On Windows devices, you can control whether VNC is allowed globally. Refer to VNC Integration. When VNC is allowed, Datto RMM installs a VNC (Virtual Network Computing) server as part of the Agent. However, this service is not configured to be open. The VNC server is configured to only listen for connection requests that come from the local device itself, and not the internet. As such, only the Datto RMM Agent is able to communicate with it, with the connections occurring through Datto's own secured tunnel server network.
Supported TLS Cipher Suites
Certain TLS 1.2 Cipher Suites, which are typically enabled by default on Windows operating systems but can be manually disabled, must be enabled on Windows Servers for the Datto RMM Agent to connect.
Datto RMM utilizes Amazon CloudFront for connections and currently follows the security policy TLSv1.2_2019. When enabled, the following TLS Cipher Suites allow the Datto RMM Agent to connect:
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
Refer to Supported protocols and ciphers between viewers and CloudFront in the Amazon CloudFront Developer Guide.
Datto RMM runs on a hardened Ubuntu Linux platform, with all instances launched from a patched and maintained Elastic Block Storage (EBS) image based on an original provided by Canonical Ltd. All instances exist for a maximum of one release cycle before being terminated and replaced by a newly instantiated server. This ensures consistency across all servers in the Datto RMM platform and provides a base level of security without the need to worry about missing critical patches or configuration for each server.
AWS Console access
Each Datto RMM platform is hosted within a separate AWS Account, with no shared access. Administration of the services provided by AWS (EC2, RDS, S3, etc.) is performed through the use of both the AWS Console and the AWS API Services for programmatic access.
Only essential staff within Datto RMM have access to these services, with access configured on a per-platform basis through the use of AWS Identity and Access Management. All logins to the console are required to have a secure password of at least 12 characters and high complexity in addition to the use of TOTPs. Programmatic access to the AWS API is controlled through Secure Keys and Secrets issued via the IAM interface.
Each user, and by extension each Secure Access Key, has their rights and permissions tailored to their role or intended usage. Should a single access key be compromised, its access is restricted to specific areas of functionality. It cannot be used to “mint” more access keys, and it can be easily revoked and replaced.
Instance access
There exists a single instance within the Pinotage platform which is externally accessible over a port other than 443. This instance is the SSH Instance and can be accessed via a secure SSH connection on port 22, authenticated only through the use of one of a small number of Private Keys. This ensures that access to the platforms can be tightly controlled and logged. Access to further AWS Instances is then available through this dedicated SSH instance, via the use of additional Private Keys.
Since the database is not externally accessible, it too must be accessed through this dedicated SSH instance via the use of a secure SSH Tunnel.
Penetration testing
The Datto RMM platform undergoes periodic Penetration Testing via external approved companies. In addition to this, the platform is regularly tested for vulnerabilities via the use of automated tools such as Tenable Nessus.
Not only is the platform itself probed for vulnerabilities, but the Web Interface and Web Services are regularly tested. This testing focuses on ensuring that not only are accounts secure from unauthorized access, but that the Web Interface is hardened against XSS or CSRF attacks, username enumeration, file upload vulnerabilities, and more.
Instance monitoring
Where previously all instances were periodically logging to S3 with the SSH Instance logs regularly reviewed, Datto RMM is now moving to a centralized log aggregation system called Loggly. This system ensures that all system and application logs can be monitored and reviewed in real time, providing instant alerting of issues or unauthorized access attempts to a system. This centralization not only provides increased security, but also visibility of potential application issues before they become a problem.
As follows is a brief outline of AWS Security and Compliance information. For a full overview, please visit https://aws.amazon.com/security/.
Physical security
AWS data centers are housed in nondescript facilities. Physical access is strictly controlled both at the perimeter and at building ingress points by professional security staff utilizing video surveillance, intrusion detection systems, and other electronic means. Authorized staff must pass two-factor authentication a minimum of two times to access data center floors.
All visitors and contractors are required to present identification and are signed in and continually escorted by authorized staff.
Our hosting center only provides data center access and information to employees and contractors who have a legitimate business need for such privileges. When an employee no longer has a business need for these privileges, his or her access is immediately revoked, even if they continue to be an employee of the hosting center. All physical access to data centers by employees is logged and audited routinely.
Control environment
Our hosting center manages a comprehensive control environment that includes the necessary policies, processes and control activities for the delivery of each of the Datto RMM service offerings. The collective control environment encompasses the people, processes, and technology necessary to maintain an environment that supports the effectiveness of specific controls and the control frameworks for which the hosting center is certified and/or compliant.
Our hosting service is compliant with various certifications and third-party attestations. These include:
- SAS70 Type II. This report includes detailed controls that the hosting service operates along with an independent auditor opinion about the effective operation of those controls.
- PCI DSS Level 1. The hosting service has been independently validated to comply with the PCI Data Security Standard as a shared host service provider.
- ISO 27001. The hosting service has achieved ISO 27001 certification of the Information Security Management System (ISMS) covering infrastructure, data centers, and services.
- FISMA. The hosting service enables government agency partners to achieve and sustain compliance with the Federal Information Security Management Act (FISMA). The hosting service has been awarded an approval to operate at the FISMA-Low level. It has also completed the control implementation and successfully passed the independent security testing and evaluation required to operate at the FISMA-Moderate level.
Environmental safeguards
The hosted data centers are state-of-the-art, utilizing innovative architectural and engineering approaches.
Fire detection and suppression
Automatic fire detection and suppression equipment has been installed to reduce risk. The fire detection system utilizes smoke detection sensors in all data center environments, mechanical and electrical infrastructure spaces, chiller rooms, and generator equipment rooms. These areas are protected by either wet-pipe, double-interlocked pre-action, or gaseous sprinkler systems.
Power
The data center electrical power systems are designed to be fully redundant and maintainable without impact to operations, 24 hours a day, and seven days a week. Uninterruptible Power Supply (UPS) units provide back-up power in the event of an electrical failure for critical and essential loads in the facility. Data centers use generators to provide back-up power for the entire facility.
Climate and temperature
Climate control is required to maintain a constant operating temperature for servers and other hardware, which prevents overheating and reduces the possibility of service outages. Data centers are conditioned to maintain atmospheric conditions at optimal levels. Personnel and systems monitor and control temperature and humidity at appropriate levels.
Refer to Agent encryption.