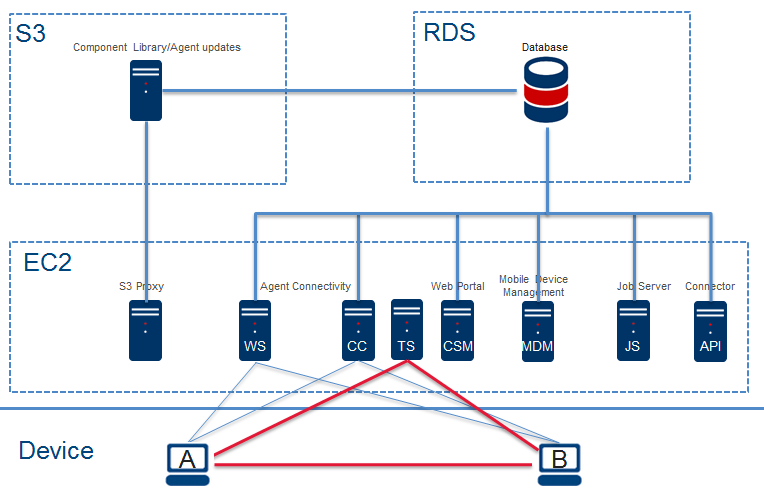
Allowlist requirements for IP addresses and URLs
This article outlines the requirements for allowing Datto RMM the network access it needs to work at its full potential if devices are behind a firewall, as well as additional information related to network connectivity for various Datto RMM functions.
Initial allowlisting for Datto RMM
In order to ensure the networks your managed devices are on are properly configured, and to track down any connection issues you may have, refer to the below list.
- Allow inbound traffic from Datto RMM to your managed devices: Allowing inbound traffic from Datto RMM to your managed devices can be accomplished by allowlisting the Fully Qualified Domain Name (FQDN) for your Datto RMM platform, or, if needed, by allowlisting the IPs returned by that FQDN. For more information, refer to Allowing Datto RMM access to the internet.
- Allow outbound traffic from your managed devices to Datto RMM: If you have outbound traffic restricted, then you will need to configure outbound rules to allow your managed devices to send information to the Datto RMM service. Refer to IP addresses per platform (Outbound).
- Allow access to the Datto RMM web interface: If you need to allow access to the Datto RMM web interface, refer to Connecting to the Datto RMM web interface.
- Allow access for Web Remote communication: If you need to allow access to allow our Web Remote tool to connect to your remote devices, refer to Web Remote communication.
- Inbound and Outbound rules for Datto RMM processes and services: The Datto RMM agent uses various services and processes, all of which have allowlisting needs. Refer to Inbound and Outbound Rules.
- Allow access for communication over needed ports: Various ports are used for communication in Datto RMM. Refer to Port usage.
IMPORTANT In addition to the configurations in the above listed items, some firewalls, proxies, or security appliances may require access to the URL of the service as well as the IP address. To review all URLs used by your Datto RMM platform, refer to URLs.
Allowlisting for additional Datto RMM functions
The above steps will get you started with the basic functions of Datto RMM. Review the below list for information on allowlisting needed for the following optional features and integrations.
- Advanced Software Management: If you are using Advanced Software Management, you will need to allowlist our Advanced Sofware Management URL. Refer to Advanced Software Management communciation.
- Datto AV: If you are integrated with Datto AV, you will need to add additional URLs to your allowlist. Refer to Datto AV.
Additional Information
This article also hosts additional information on the following topics:
- Temporary directory location: Many operations performed by Datto RMM do not use the OS's default temp folder location. Refer to Change of Temporary directory.
- Connecting agents through the tunnel grid: To learn more about how connections are established with remote Agents, refer to Connecting Agents through the tunnel server grid.
- UI access on restricted networks: In certain cases, depending on your network setup, users may be locked out of accessing the UI. To learn how to resolve this, refer to UI access on restricted networks.
- AV Exclusions: Depending on your antivirus, you may need to set up exclusions to certain file or folder locations to ensure Datto RMM can operate uninterrupted. Refer to Folders and file paths used by Datto RMM.
- Receiving emails from Datto RMM: To ensure you are not blocking emails from Datto RMM, ensure you are not blocking emails from the rmm.datto.com email domain.
EXAMPLE alerts@rmm.datto.com for alerts, reports@rmm.datto.com for reports, etc.
- Internet protocol: The Datto RMM Agent communicates with the platform using the IPv4 protocol
NOTE IPv6 connections are not supported at this time
- Stateful packet inspection: It is strongly recommended that any Stateful Packet Inspection be turned off for access to any centrastage.net address, and that all attempts possible are made to guarantee that TCP connections to the cc.centrastage.net addresses are not terminated in cases of inactivity (these connections may be inactive for up to 180 seconds at a time if no client activity is detected).
- Blocklist: Some countries are not permitted access to the Datto RMM web interface. For more information, refer to Blocklist.
To help ease the burden of administration and reduce human error when managing allowlists across multiple firewalls, a series of Fully Qualified Domain Names (FQDNs) for DNS A records have been made available. These will return every IP address applicable for a given platform, correct as of the time of the query.
The records for each platform are as follows:
- concord-ips.centrastage.net
- vidal-ips.centrastage.net
- zinfandel-ips.centrastage.net
- merlot-ips.centrastage.net
- pinotage-ips.centrastage.net
- syrah-ips.centrastage.net
Additionally, the Tunnel Server network, which is used for remote takeover, can be added in a similar fashion using the below A Record:
-
tunnel-ips.centrastage.net
Provided it is a supported option, the FQDNs for these A Records can be added as required to a firewall’s allowlist configuration to permit network access to Datto RMM. This allows the IP addresses used by Datto RMM to change without interrupting coverage or leaving out of date entries in the allowlist configuration.
If this method is not available for your firewall, refer to Method 2: Manually as individual IP addresses.
Some networking hardware may not be capable of accepting FQDNs for allowlisting. In this situation, A Records can be polled manually by a computer running any mainstream operating system for a list of IP addresses accurate as of the time of the query. These IP addresses can then be entered manually into the configuration.
IMPORTANT As is typical for any cloud-hosted product, Datto RMM’s IP addresses change regularly. Please ensure you check periodically to ensure the IP addresses you are allowlisting for Datto RMM are up-to-date.
NOTE It is recommend that monthly notes are kept of which IP addresses are being manually allowlisted to ensure unused or remnant entries are cleared out.
To query the DNS A records, use the following commands depending on your operating system:
- Windows: nslookup <platform>-ips.centrastage.net
- Linux: dig <platform>-ips.centrastage.net, host <platform>-ips.centrastage.net, or nslookup <platform>-ips.centrastage.net
- macOS: host <platform>-ips.centrastage.net
For more information, refer to this Kaseya Community post.
To allow seamless connectivity to the Datto RMM web interface and between Agents, you must open TCP port 443 outbound through your firewall.
If your company has a more aggressive security posture for outbound traffic (for example, port blocking and IP address access lists), then you may need to add a number of IP addresses and/or URLs to the allowlist in addition to opening up port 443 to allow Datto RMM to make the required connections. The IP addresses and URLs you must add to the allowlist are specific to your platform, and you only need to add those associated with your platform.
To learn more about which addresses allow access to the Datto RMM web interface for your platform, select your platform below and review the Web Interface section of the linked table.
NOTE For information about the platform your site is hosted on, refer to Datto RMM platforms.
If accessing the Datto RMM web interface on a restricted network, such as through Microsoft's Global Secure Access, you may need to add allowlisting for one of the following URLs, depending on which Datto RMM platform you are on, to access the New UI:
| Platform | URL |
|---|---|
| Pinotage | https://pinotage-frontend-api.centrastage.net |
| Merlot | https://merlot-frontend-api.centrastage.net |
| Concord | https://concord-frontend-api.centrastage.net |
| Vidal | https://vidal-frontend-api.centrastage.net |
| Zinfandel | https://zinfandel-frontend-api.centrastage.net |
| Syrah | https://syrah-frontend-api.centrastage.net |
For information on all URLs that may need to be allowlisted for access to the Datto RMM web interface, and more, refer to URLs.
IMPORTANT In order to reduce security false positives, improve monitoring and automation reliability, and make our Agent’s allowlisting more comprehensive, we make use of a temporary directory underneath the Datto RMM Agent’s installation path rather than the %TEMP% folder.
These paths are as follows:
• Windows: %ProgramData%\CentraStage\Temp, %ProgramData%\CentraStage\AEMAgent\Temp
• macOS and Linux: usr/local/share/CentraStage/Temp, usr/local/share/CentraStage/AEMAgent/Temp
The following operations by default do not create or modify files in the %TEMP% folder:
- Script files
- Downloading of Agent Modules packages
- CagService update
- Agent update
- Downloading of Windows Updater file
- Vine VNC setup script file (macOS)
- Screen Capture (macOS)
- Web Remote file transfer
NOTE If the CagService, Agent, or Web Remote operations are not able to create or use their own Temp directory, all operations above will fallback to using the default %TEMP% folder.
Datto RMM uses several ports for various functions. All of the ports needed and their functions are listed below.
| Datto RMM Function | Port(s) | TCP/UDP | Inbound/Outbound | Additional Information |
|---|---|---|---|---|
| Web interface and Agent to Agent connection | 443 | TCP | Outbound | Connecting to the Datto RMM web interface |
| Agent Discovery | 13300 | UDP | Inbound | This port is used for network discovery in environments with rigorous network security. |
| Web Remote | 3478 and port range 49152 - 65535 | TCP and UDP | Outbound | These ports need to be opened for the tunnel server DNS A record. For more information on Web Remote requirements, refer to Web Remote communication. |
When working with antivirus solutions, such as Datto AV, there may be a need to exclude certain files or folders that Datto RMM uses in order to ensure it behaves consistently.
Excluding the following locations from being targeted by your AV policy can help prevent it from flagging Datto RMM as unwanted or malicious:
- Datto RMM folder paths:
- C:\Program Files (x86)\CentraStage\
- C:\ProgramData\CentraStage\
- Datto RMM executable paths:
- C:\Program Files (x86)\CentraStage\CagService.exe
- C:\ProgramData\CentraStage\AEMAgent\AEMAgent.exe
- C:\Program Files (x86)\CentraStage\gui.exe
- C:\ProgramData\CentraStage\AEMAgent\RMM.WebRemote\*\RMM.WebRemote.exe
- C:\ProgramData\CentraStage\AEMAgent\RMM.WebRemote\*\RMM.RTC.Proxy\RMM.RTC.Proxy.exe
IMPORTANT While this is a proven list of known locations to exclude for Datto AV, your antivirus configuration may differ. Always check the AV developer documentation for recommended best practices before making any changes.
The initial connection between browser and Agent is initialized via WebRTC servers. Refer to WebRTC. Depending on the firewall configuration, the connection will resolve via STUN server (when P2P connection is possible) or TURN server (when Relay connection would be chosen). The WebRTC servers are located in several regions. Refer to Method 1: Via FQDNs/DNS A records.
The minimum requirements for Web Remote are as follows: outbound port 3478 and ports between 49152 - 65535 should be open (both TCP and UDP) for the tunnel server DNS A record. Refer to Method 1: Via FQDNs/DNS A records.
The following URLs need to be added to the allowlist:
| Software | Operating System | URL |
|---|---|---|
| Microsoft .NET (dotnet.exe) | Windows | https://dotnet.microsoft.com |
| N/A | Windows and macOS | https://tunnel.rmm.datto.com |
|
N/A |
Windows and macOS |
https://webrtc.rmm.datto.com |
IMPORTANT In addition, all DigiCert certificate status IPv4 addresses need to be allowed outbound access. The list of IP addresses and domains that need this access is located in the DigiCert Certificate Status IP Addresses article. There is a link to download a spreadsheet of this information at the bottom of the linked page.
For partners using Advanced Software Management, the following URL must not be blocked for the feature to function correctly:
URL:
- smpm.kaseya.com
IMPORTANT Advanced Software Management does not currently support proxy-configured Datto RMM agents.
Refer to Advanced Software Management.
If you are integrated with Datto AV, the following URLs will need to be added to the allowlist to allow installation:
- hunt-saas-files.s3.us-east-1.amazonaws.com
- hunt-saas-surveys.s3.us-east-1.amazonaws.com
- infocyte-downloads.s3.us-east-1.amazonaws.com
For more information on integrating Datto AV with Datto RMM, refer to Datto Endpoint Security Integration.
Unless a peer-to-peer connection can be established between devices, Agent to Agent connectivity and remote takeover are managed by a tunnel server over an encrypted connection. Tunnel servers are connection relays located around the globe to provide maximum coverage and the best performance depending on your location. They are automatically available to all users.
When a remote takeover session is initiated:
- The admin device performs a DNS query to find the nearest tunnel server. The tunnel server is picked based on the proximity to the admin device.
NOTE When connecting to a device via Web Remote, the tunnel server is picked based on proximity to the remote device instead of the admin device.
- A connection is made to a load-balanced tunnel server cluster.
- Finally, a connection is established to the remote device.
To make the most of the tunnel server grid, please ensure that the IP addresses relevant to your geographic location are added to the allowlist and outbound traffic on port 443 is open on your own and your endpoints' firewalls.
The following rules are configured for all local and remote ports:
| Rule Name | Protocol | Description | Inbound | Outbound |
|---|---|---|---|---|
| AEMAgent | ANY | Datto RMM Agent Process |
|
|
| CentraStage_monitor | TCP/UDP | Datto RMM Monitoring Agent |
|
|
| CentraStage_service | TCP/UDP | Datto RMM Agent Service |
|
|
| RMM RTC Proxy | ANY | Datto RMM Web Remote RTC Proxy Service |
|
|
| RMM RTO Proxy | ANY | Datto RMM Web Remote RTO Proxy Service |
|
|
| RMM Web Remote | ANY | Datto RMM Web Remote Process |
|
|
| uVNC_Service | TCP/UDP | uVNC Service for VNC Connections |
|
Additional IP addresses and URLs
IMPORTANT Aside from the following IP addresses listed, additional IPs may be used to access various Amazon Web Services (AWS) infrastructure. The list gets updated as AWS makes changes. For more information, refer to AWS IP Address Ranges.
IMPORTANT If your antivirus product has flagged the Datto RMM Agent installer as malicious, speak to your antivirus provider and request that they mark the installer as a false positive to allow it through.
Inbound and tunnel server IP addresses for Datto RMM
For information on how to obtain a list of inbound and tunnel server IP addresses for Datto RMM, refer to Method 1: Via FQDNs/DNS A records.
IP addresses per platform (Outbound)
Add the following IP addresses to the allowlist for outbound communication if either of these scenarios apply to your Datto RMM account:
- You are using the ConnectWise PSA Integration and are connecting to an on-premise Connectwise PSA server.
- You are using the IT Glue Integration, and IP Access Control in your instance of IT Glue is restricted to certain IP addresses. For details, refer to Allow the IP address of your Datto RMM platform access to IT Glue.
| Concord (US East) | Vidal (US East) | Zinfandel (US West) | Merlot (EU) | Pinotage (EU) | Syrah (APAC) |
|---|---|---|---|---|---|
|
54.90.30.238 18.210.141.219 34.206.106.100 52.72.137.122 |
107.22.0.143 34.231.104.171 34.232.253.178 |
52.33.150.151 44.237.4.153 52.41.95.147 |
18.202.215.160 3.251.48.174 |
52.31.46.222 52.210.155.229 52.212.169.223 54.155.36.8 |
3.104.103.44 52.62.188.240 |
URLs
In addition to IP addresses, some firewalls, proxies, or security appliances may require access to the URL of the service as well as the IP address.
If you are using a proxy or security appliance, we recommend that you add the centrastage.net and the rmm.datto.com domains to the allowlist in their entirety if possible or, at a minimum, ensure that the relevant URLs to your platform are added to the allowlist.
ComStore component and Software Management URLs
If you are downloading and running components from the ComStore, we recommend that you add storage.centrastage.net and storage.rmm.datto.com to the allowlist. Additionally, if you use any of the following software applications either as a ComStore component or via Software Management, make sure to add the relevant URL(s) to the allowlist:
| Software | Operating System | URL |
|---|---|---|
| 7-Zip | Windows | https://www.7-zip.org |
| Adobe Acrobat Reader DC | Windows, macOS | https://ardownload2.adobe.com |
| Adobe Air | Windows, macOS | https://airsdk.harman.com |
| Bitdefender Endpoint Security Tools | Windows | http://download.bitdefender.com and https://cloudgz.gravityzone.bitdefender.com |
| Bitdefender GravityZone - Deployment/Management | Windows, macOS, Linux | http://download.bitdefender.com |
| Citrix Workspace | Windows, macOS | https://downloads.citrix.com |
|
Datto Secure Edge |
Windows, macOS |
https://cf-dl.datto.com |
| ESET Direct Endpoint Management - Deployment | Windows, macOS | https://update.esetusa.com |
| FileZilla Client | Windows | https://filezilla-project.org |
| Foxit Reader | Windows | https://www.foxitsoftware.com |
| Google Chrome | Windows, macOS | http://dl.google.com |
| Huntress Agent Deployment | Windows | https://huntress.io |
| Java Runtime Environment 8 (latest update) | Windows | https://javadl.oracle.com and https://sdlc-esd.oracle.com |
| Liongard Agent | Windows | https://agents.static.liongard.com |
| Microsoft .NET Desktop Runtime | Windows | https://builds.dotnet.microsoft.com |
| Microsoft Office 365 (Current and Semi-Annual Channels) | Windows | http://dl.delivery.mp.microsoft.com and https://download.microsoft.com https://clients.config.office.net |
| Microsoft Teams | Windows | https://aka.ms and https://teams.microsoft.com |
| Microsoft Visual C++ Redistributable | Windows | https://aka.ms and https://download.visualstudio.microsoft.com |
| Mozilla Firefox | Windows, macOS | https://download.mozilla.org |
| Mozilla Thunderbird | Windows, macOS | https://download.mozilla.org and https://download-installer.cdn.mozilla.net |
| Notepad++ | Windows | https://notepad-plus-plus.org |
| Paint.NET x86/x64 | Windows | https://www.dotpdn.com |
| PuTTY | Windows | https://the.earth.li (official mirror) |
| Trend Micro Worry-Free Services - Deployment | Windows | https://wfbs-svc-nabu-aal.trendmicro.com or https://wfbs-svc-emea-aal.trendmicro.com (depending on geographical region) |
| VLC Media Player | Windows | https://www.mirrorservice.org https://download.videolan.org |
| VMWare Tools | Windows | https://packages.vmware.com |
| Webroot SecureAnywhere Endpoint Protection | Windows | https://anywhere.webrootcloudav.com |
| Windows 10 & 11 Upgrade Components | Windows | http://dl.delivery.mp.microsoft.com and https://download.microsoft.com |
| WithSecure (F-Secure) Various | Windows | https://download.sp.f-secure.com |
| Zoom | Windows, macOS |
https://www.zoom.us https://cdn.zoom.us |
Supported TLS Cipher Suites
Certain TLS 1.2 Cipher Suites, which are typically enabled by default on Windows operating systems but can be manually disabled, must be enabled on Windows Servers for the Datto RMM Agent to connect.
Datto RMM utilizes Amazon CloudFront for connections and currently follows the security policy TLSv1.2_2019. When enabled, the following TLS Cipher Suites allow the Datto RMM Agent to connect:
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
Refer to Supported protocols and ciphers between viewers and CloudFront in the Amazon CloudFront Developer Guide.