Microsoft 365 Integration
PERMISSIONS Administrator (to enable the integration)
PERMISSIONS To configure user access to this integration, refer to Microsoft 365 in Permissions.
NAVIGATION Setup > Integrations > Microsoft 365
NAVIGATION Microsoft 365
About the integration
The Microsoft 365 Integration provides the opportunity to administer your Microsoft 365 tasks through a single user management platform. This integration streamlines otherwise complex workflows and gives technicians access to the most essential Microsoft 365 data and user management actions directly in Datto RMM.
Upon connecting a Cloud Solution Provider (CSP) tenant, Datto RMM automatically fetches all of your client tenants. You have the option to freely sync or unsync specific tenants to or from the integration at any time.
The integration offers quick access to the following resources:
- A dedicated Microsoft 365 menu in Datto RMM.
- An overview of synced tenants that includes seamless navigation to the various Microsoft client portals. Refer to All Tenants.
- A comprehensive user overview for each client tenant. Refer to All Users.
- A dedicated details page for each user featuring a user summary, list of enrolled devices, information about the groups the user is added to, and sign-in logs. Refer to User details.
- The option to create and onboard, edit, or offboard Microsoft 365 users directly from within Datto RMM. Refer to Microsoft 365 user management.
Tiered security level permissions created specifically for this integration allow you to limit access for certain users in your Datto RMM account. Refer to Microsoft 365 in Permissions.
To learn more, refer to Microsoft 365 Integration FAQ.
Prerequisites
The Microsoft 365 Integration with Datto RMM requires a Microsoft Azure account with Cloud Solution Provider (CSP).
IMPORTANT The connection for the integration must be made by a CSP tenant.
We recommend setting up a service account specific to Datto to authenticate the integration: dattointegration@[your domain].com. This will ensure the integration bypasses your Conditional Access policies, remains active, and limits issues in the future.
For this integration to work, a certain configuration is required in Microsoft 365. For guidance, review the following steps and watch the video demonstration.
Step 1: Service account permissions
Configure the following settings in Microsoft Entra:
- The authenticating user requires Microsoft multifactor authentication (MFA), which can be enforced through Conditional Access or per-user MFA settings. The MFA for this user cannot be performed through a third-party application, such as Duo. (MFA through a third-party application is adequate for other users in the account.)
NOTE The user must be excluded from any policies enforcing sign-in restrictions outside the norm of requiring MFA.
NOTE The service account must successfully authenticate with MFA during the initial connection for the integration to work properly. If there are any exceptions in the Conditional Access policy that allow MFA to be bypassed during this connection, tenants will not be pulled in to Datto RMM.
Step 2: Service account role
Configure the following settings in Microsoft Entra:
- The integrating service account must be part of two security groups: the AdminAgents security group and the security group assigned to the GDAP relationship, as described in the next section (step 3).
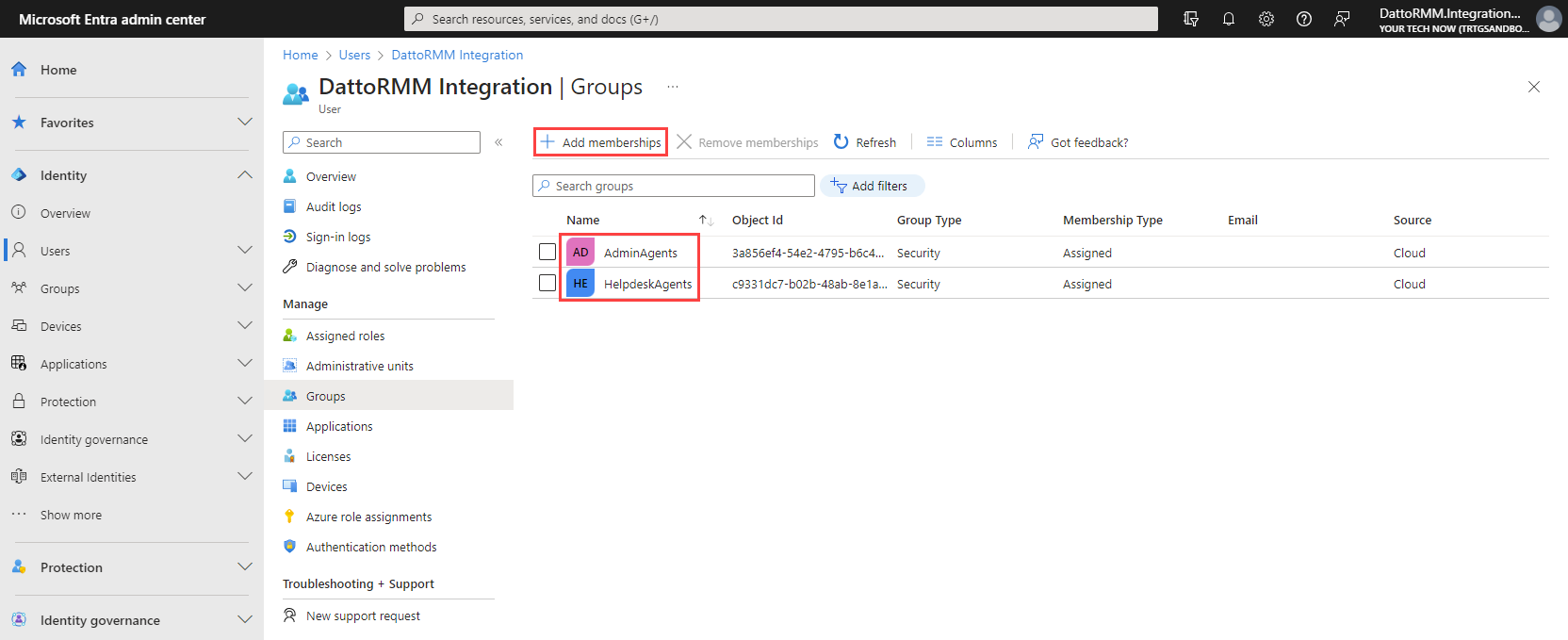
Step 3: GDAP relationship configuration
NAVIGATION Microsoft Partner Center > Customers > Administer > select a customer > select an admin relationship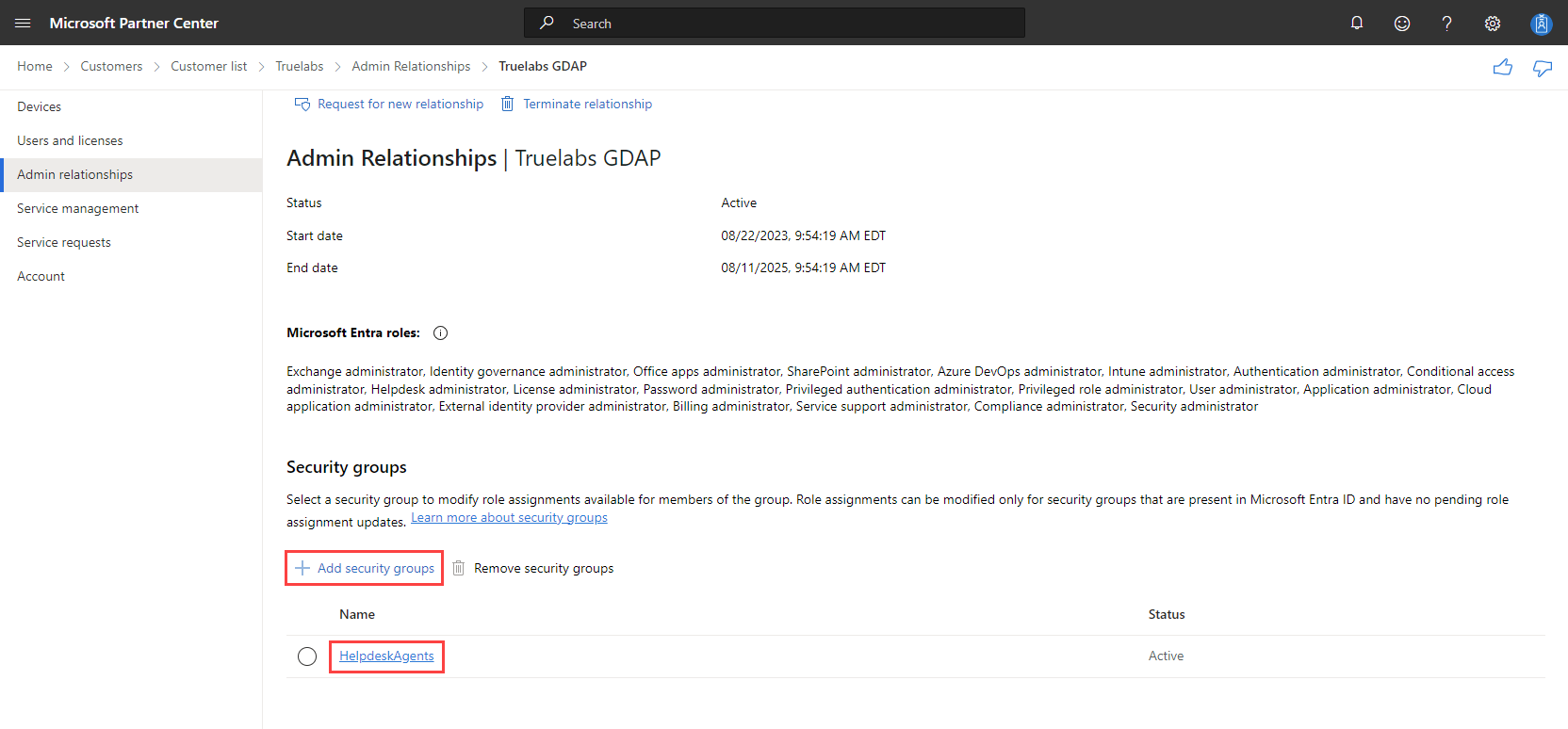
Configure the following settings in Microsoft Partner Center:
- The authenticating user must add a granular delegated admin privileges (GDAP) relationship with all client tenants.
NOTE If a client tenant has more than one GDAP relationship, Microsoft observes only the GDAP relationship that was created most recently. As mentioned, the Microsoft authentication requires the security group on the integrating account and GDAP relationship to be the same. If such is the case on one of the GDAP relationships but not on the one most recently created, then the sync will fail.
The following list contains the required Microsoft Entra Roles for supporting the Microsoft 365 Integration:
|
Microsoft Entra Roles |
Description |
|---|---|
| Application Administrator | Manage applications in the directory |
| Authentication policy administrator | Can create and manage the authentication methods policy, tenant-wide MFA settings, password protection policy, and verifiable credentials. |
| Cloud app security administrator | Can manage all aspects of the Defender for Cloud Apps product |
| Cloud device administrator | Limited access to manage devices in Microsoft Entra ID. |
| Exchange administrator | Manage Exchange Online. |
| Intune administrator | Can manage all aspects of the Intune product. |
| Privileged authentication administrator | Can access to view, set and reset authentication method information for any user (admin or non-admin). |
| Privileged role administrator | Can manage role assignments in Microsoft Entra ID, and all aspects of Privileged Identity Management. |
| Security administrator | Can read security information and reports, and manage configuration in Microsoft Entra ID and Office 365. |
| SharePoint administrator | Can manage all aspects of the SharePoint service. |
| Teams administrator | Can manage the Microsoft Teams service. |
| User administrator | Can manage all aspects of users and groups, including resetting passwords for limited admins. |
API permissions
In Microsoft Entra ID, applications are authorized to call APIs when they are granted permissions as part of the consent process.
Upon setting up the Microsoft 365 Integration from within Datto RMM, you will be required to accept a few Microsoft API permissions to ensure adequate functionality. Refer to step 8 in Enable the Microsoft 365 Integration.
These required permissions will be configured automatically in your integrated CSP tenant once you accept. For your reference, the following table lists the permissions:
| API | Permission Category | Permission | Type | Description |
|---|---|---|---|---|
| Microsoft Graph | Application | Application.ReadWrite.All | Delegated | Read and write all applications. |
| Microsoft Graph | DelegatedAdminRelationship | DelegatedAdminRelationship.ReadWrite.All | Delegated | Manage Delegated Admin relationships with customers. |
| Microsoft Graph | Directory | Directory.ReadWrite.All | Delegated | Read and write directory data. |
| Microsoft Graph | OpenId permissions | offline_access | Delegated | Maintain access to data you have given it access to. |
| Microsoft Graph | OpenId permissions | openid | Delegated | Sign users in. |
| Microsoft Partner Center | Permissions | user_impersonation | Delegated | Access Partner Center. |
Features
If you encounter synchronization issues, refer to Microsoft 365 Integration troubleshooting.
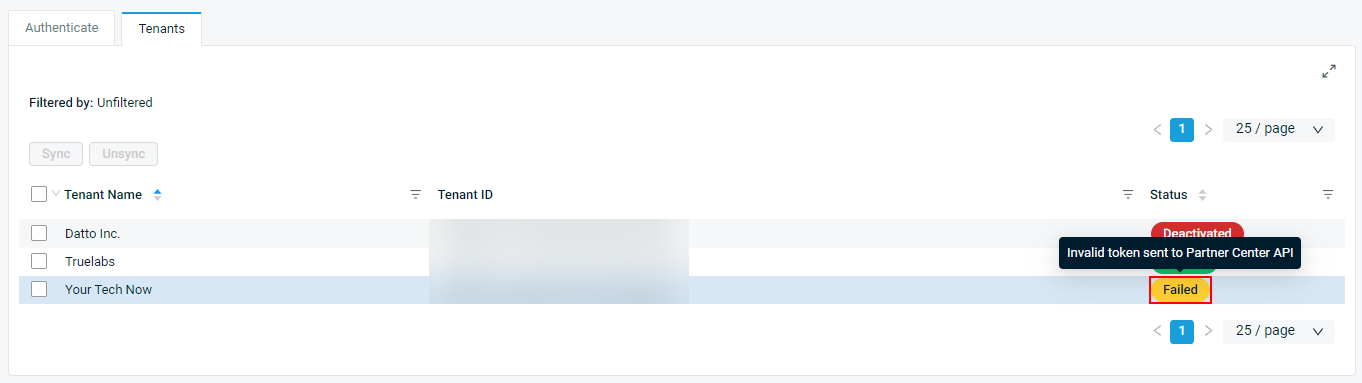
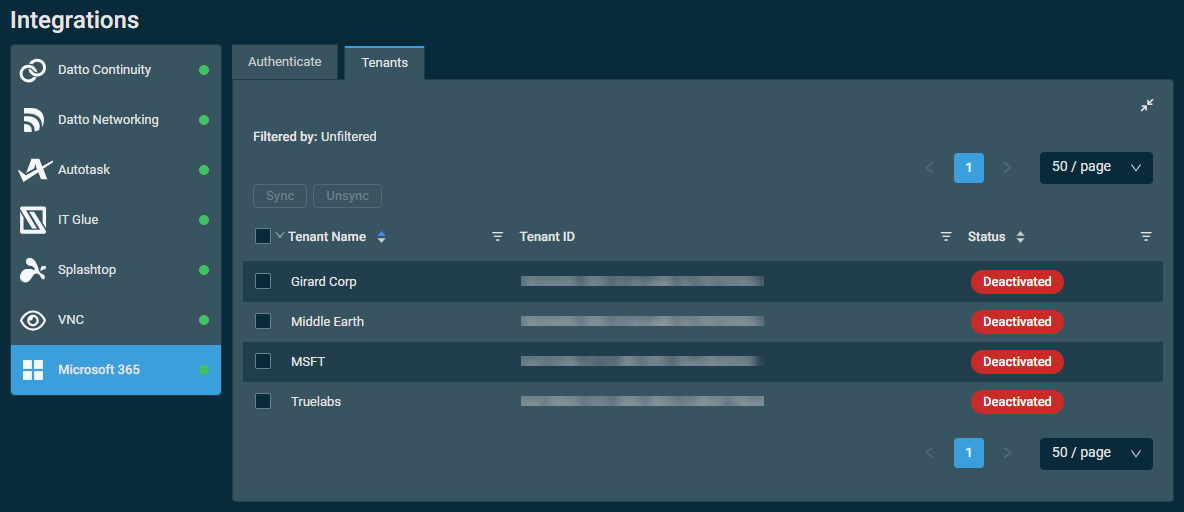
To access the tenant sync table, navigate to Setup > Integrations > Microsoft 365 > Tenants.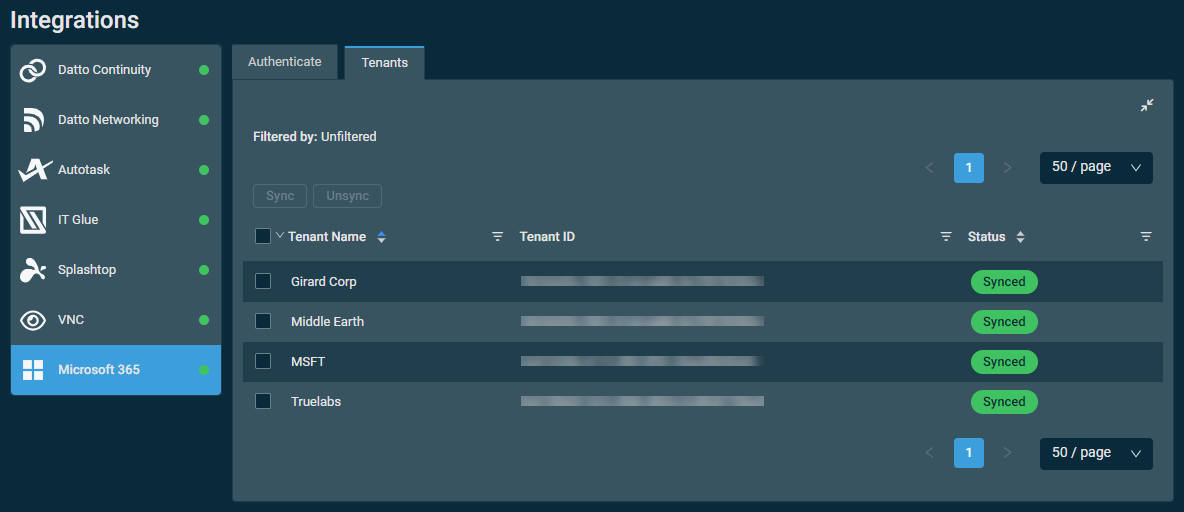
Once the Microsoft 365 Integration is enabled, Datto RMM automatically fetches all of your Microsoft 365 client tenants. Any tenants in this list can be freely synced to or unsynced from Datto RMM while the integration is active. Manual tenant syncing is required to begin using the integration. For instructions, refer to Sync Microsoft 365 client tenants to Datto RMM.
The tenant sync table displays the following information:
| Field | Sortable? | Description |
|---|---|---|
| Tenant Name |
|
The name of the tenant as it exists in Microsoft Entra ID. To narrow the list, click the filter icon |
| Tenant ID | Displays the tenant ID. To narrow the list, click the filter icon |
|
| Status |
|
Displays the sync status of the tenant, which can be one of the following:
To narrow the list, click the filter icon |
You can filter both of the columns. The Filtered by bar displays all applied column filters. If a filter search term includes wildcard characters (for example, underscores and percent signs), they serve as normal characters if they are preceded by a backslash. For details, refer to Wildcard characters. Click the X next to any filter to remove that filter or click Reset Filters to remove all filters. If no filter is applied, the Filtered by bar displays Unfiltered. The filter selection in the columns will persist the next time the page is accessed.
The table density is set to condensed theme by default. To change it to relaxed theme, click the density toggle icon. ![]() The selection will persist across all pages.
The selection will persist across all pages.
The number of results displayed can be specified by selecting the desired number from the pagination control. This selection will persist the next time the page is accessed.
Action buttons
The action buttons are unavailable if no row is selected in the table. The check boxes allow you to select one or more rows. Select all rows shown on a page by selecting the check box in the table header. You can also use the drop-down arrow next to the check box in the table header to choose one of the following options: Select none, Select all on page, or Select all rows across all pages. If you choose to select all rows across all pages, the check boxes of the rows will not be selected; however, the page will indicate that all rows have been selected.
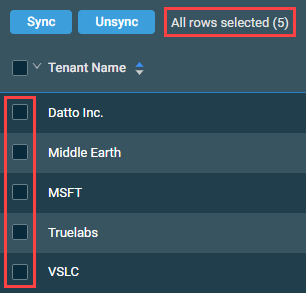
| Action Button | Description |
|---|---|
| Sync | Initiates the operation to sync the selected tenants to Datto RMM. Refer to Sync Microsoft 365 client tenants to Datto RMM. |
| Unsync | Initiates the operation to unsync the selected tenants from Datto RMM. Refer to Unsync Microsoft 365 client tenants from Datto RMM. NOTE If your own tenant (the primary tenant) is synced, it cannot be unsynced. |
Once the Microsoft 365 Integration is enabled and tenants are synced, the All Tenants page and All Users page can be used to view Microsoft 365 data. Refer to Enable the Microsoft 365 Integration and Sync Microsoft 365 client tenants to Datto RMM.
You can easily access these pages from the Microsoft 365 menu in the left navigation menu.
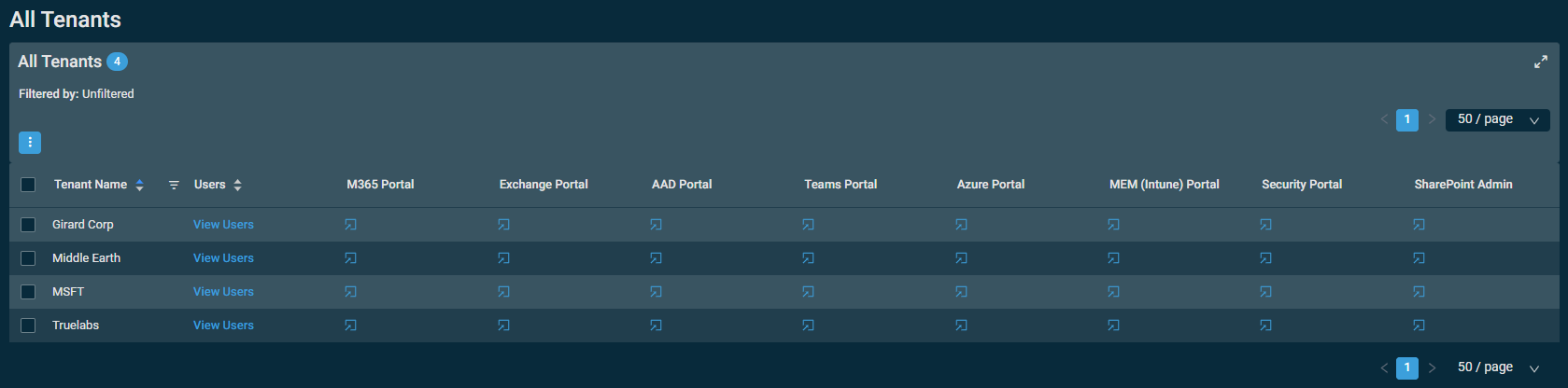
To access the All Tenants page, navigate to Microsoft 365 > All Tenants.
List of tenants
IMPORTANT Only the tenants you have manually synced will appear in this list. Refer to Sync Microsoft 365 client tenants to Datto RMM.
This page allows you to open Microsoft client portals directly from Datto RMM. The portals open in new tabs.
NOTE The redirects to the Microsoft portals comply with Microsoft user permissions. If a user clicks a link in Datto RMM to navigate to a Microsoft page they do not have permission to access, Microsoft will block the user's access.
The badge in the table header shows the number of synced client tenants.
The table displays the following information:
| Field | Sortable? | Description |
|---|---|---|
| Tenant Name |
|
The name of the tenant as it exists in Microsoft Entra ID. To narrow the list, click the filter icon Click the name to open an overview of the tenant details in Datto RMM. |
| Users | Click View Users to open the list of users that belong to the tenant. Refer to All Users. | |
|
|
Click View Devices to open the list of devices that belong to the tenant. Refer to All Devices. |
|
| Entra Admin Portal* | Click the arrow to manage the tenant in this portal. | |
| Azure Portal* | Click the arrow to manage the tenant in this portal. | |
| Exchange Admin* | Click the arrow to manage the tenant in this portal. | |
| M365 Admin* | Click the arrow to manage the tenant in this portal. | |
| Intune Admin* | Click the arrow to manage the tenant in this portal. | |
| M365 Defender* | Click the arrow to manage the tenant in this portal. | |
| SharePoint Admin* | Click the arrow to manage the tenant in this portal. | |
| Teams Admin* | Click the arrow to manage the tenant in this portal. |
NOTE *Users with the proper access in Datto RMM will be able to see and click these links but will require the proper permissions in Microsoft 365 to access the related areas within the tenant.
The columns can be reordered and resized. The order and size of the columns will persist the next time the page is accessed.
You can filter the Tenant Name column. The Filtered by bar displays all applied column filters. If a filter search term includes wildcard characters (for example, underscores and percent signs), they serve as normal characters if they are preceded by a backslash. For details, refer to Wildcard characters. Click the X next to any filter to remove that filter or click Reset Filters to remove all filters. If no filter is applied, the Filtered by bar displays Unfiltered. The filter selection will not persist the next time the page is accessed as the table will return to the default view (unfiltered).
The table density is set to condensed theme by default. To change it to relaxed theme, click the density toggle icon. ![]() The selection will persist across all pages.
The selection will persist across all pages.
The number of results displayed can be specified by selecting the desired number from the pagination control. This selection will persist the next time the page is accessed.
Action buttons
To access the available action buttons, click the Row Actions icon. The action buttons are unavailable if no row is selected or if the action is not applicable to the selected rows. The check boxes allow you to select one or more rows. Select all rows shown on the page by selecting the check box in the table header.
The following table lists all available action buttons:
To access the All Users page, navigate to Microsoft 365 > All Users.
Create User
For complete instructions on the Create User action button in the upper-right corner of the page, refer to Microsoft 365 user management.
List of users
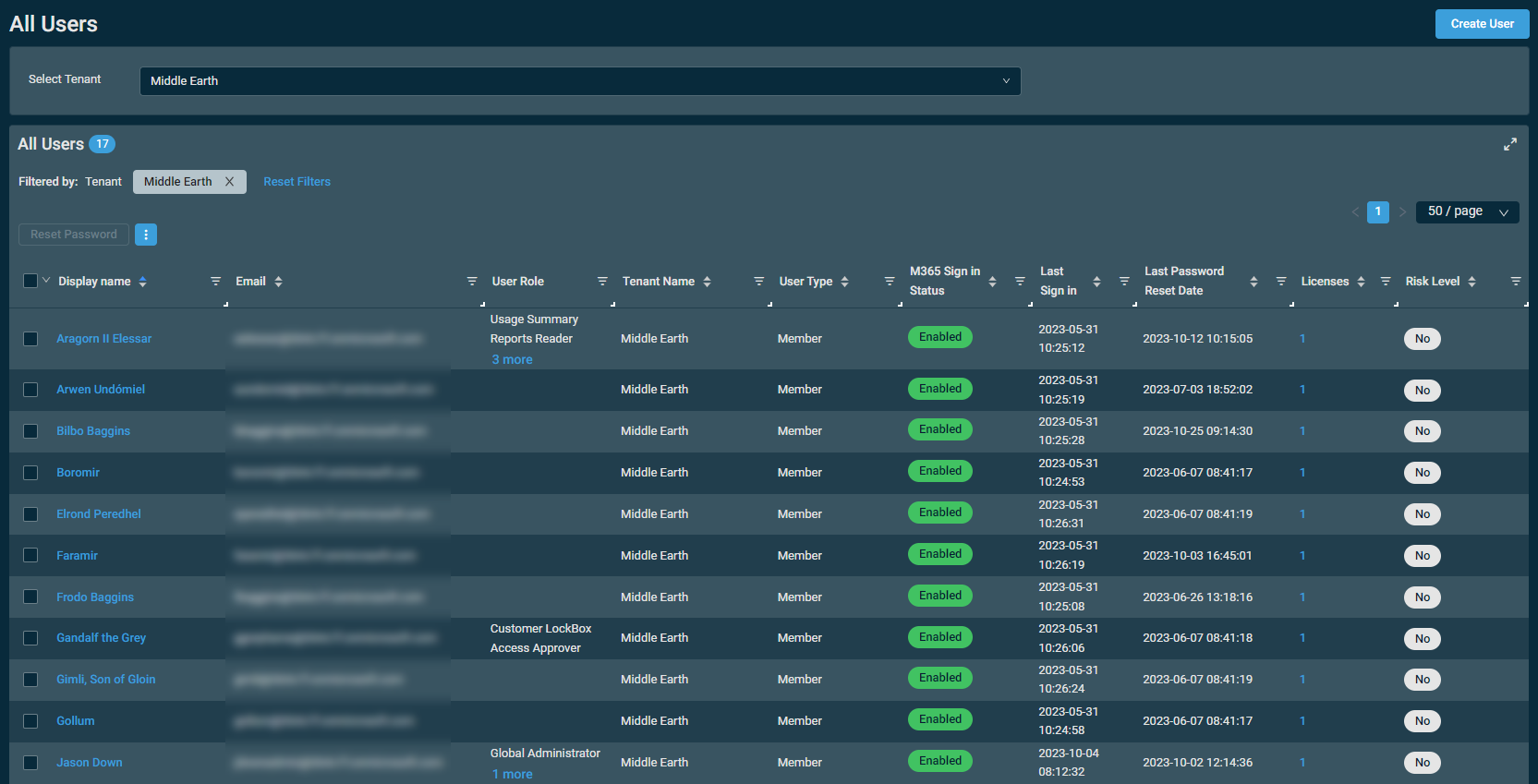
By default, the page displays all users across all tenants. To populate a list of users from specific tenants, select one or more tenants from the Select Tenant drop-down menu.
You can filter by one or more tenants using the filter icon ![]() in the Tenant Name column. Refer to Tenant Name.
in the Tenant Name column. Refer to Tenant Name.
You can also open this list from the All Tenants page. Click View Users in the Users column. Refer to Users in List of tenants.
The badge in the table header shows the number of users in the currently displayed list, whether filtered or unfiltered.
NOTE This list supports up to 999 users. The first 999 users fetched by Microsoft are those that sync to the integration.
The table displays the following information:
| Field | Sortable? | Description |
|---|---|---|
| Display Name |
|
The display name of the user as it exists in Microsoft. To narrow the list, click the filter icon NOTE This field is searchable via global search. Refer to Global search. |
|
|
The username/user principal name (user email address) as it exists in Microsoft. To narrow the list, click the filter icon NOTE This field is searchable via global search. Refer to Global search. |
|
| User Role |
|
The user role(s) assigned to the user in Microsoft. To narrow the list, click the filter icon |
| Tenant Name |
|
The name of the client tenant, which the user belongs to, as it exists in Microsoft Entra ID. To narrow the list, click the filter icon NOTE You can change the selected tenant from the Select Tenant drop-down menu at the top of the page. |
| User Type |
|
The user type assigned to the user in Microsoft. To narrow the list, click the filter icon |
| M365 Sign In Status |
|
Displays whether or not signing into this user account has been blocked, as follows:
Refer to Block Sign In/Unblock Sign In in User details. |
| Last Sign In |
|
Displays how long ago the user's latest sign-in occurred. Time stamps reflect the user time zone and preferred date format configured on the Setup > My Settings page. Hovering over any time stamp will show its date in the alternative format. Refer to User Time Zone and Date Format. Click the filter icon The Sign in Logs card displays additional sign-in information. Refer to Signin Logs. |
| Last Password Reset Date |
|
Displays how long ago the user's latest password reset occurred. Time stamps reflect the user time zone and preferred date format configured on the Setup > My Settings page. Hovering over any time stamp will show its date in the alternative format. Refer to User Time Zone and Date Format. Click the filter icon |
| Licenses |
|
Displays the Microsoft licenses assigned to this user. To narrow the list, click the filter icon |
The columns can be reordered and resized. The order and size of the columns will persist the next time the page is accessed.
You can filter any columns with the filter icon ![]() . The Filtered by bar displays all applied column filters. If a filter search term includes wildcard characters (for example, underscores and percent signs), they serve as normal characters if they are preceded by a backslash. For details, refer to Wildcard characters. Click the X next to any filter to remove that filter or click Reset Filters to remove all filters. If no filter is applied, the Filtered by bar displays Unfiltered. The filter selection in the columns will persist the next time the page is accessed.
. The Filtered by bar displays all applied column filters. If a filter search term includes wildcard characters (for example, underscores and percent signs), they serve as normal characters if they are preceded by a backslash. For details, refer to Wildcard characters. Click the X next to any filter to remove that filter or click Reset Filters to remove all filters. If no filter is applied, the Filtered by bar displays Unfiltered. The filter selection in the columns will persist the next time the page is accessed.
The table density is set to condensed theme by default. To change it to relaxed theme, click the density toggle icon. ![]() The selection will persist across all pages.
The selection will persist across all pages.
The number of results displayed can be specified by selecting the desired number from the pagination control. This selection will persist the next time the page is accessed.
Action buttons
To access all action buttons, click the Row Actions icon.
The action buttons are unavailable or become unavailable if no row is selected in the table or if the action button is not applicable to the selected rows. The check boxes allow you to select one or more rows. Select all rows shown on a page by selecting the check box in the table header. You can also use the drop-down arrow next to the check box in the table header to choose one of the following options: Select none, Select all on page, or Select all rows across all pages. If you choose to select all rows across all pages, the check boxes of the rows will not be selected; however, the page will indicate that all rows have been selected.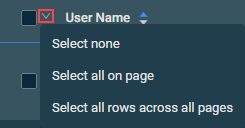
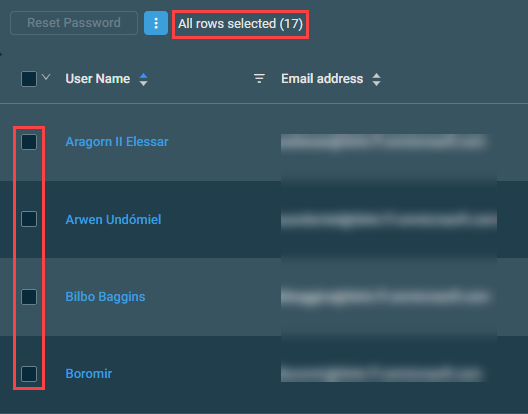
NOTE When all rows are selected across all pages, only certain action buttons are supported, which is indicated in the All Rows column in the following table.
The user actions are also available on the individual user details pages. Refer to Action buttons in User details.
| Action Button | All Rows | Description |
|---|---|---|
| Reset Password |
|
Available only when one user is selected. Refer to Reset Password in User details. |
| Export Selected Rows to CSV | In the confirmation dialog box that appears, select whether to show table headers in the file by turning on the toggle for Show table headers in the exported CSV. Click Confirm to download the file or Cancel to close out of the dialog box. Any column selections, filters, and sorting that have been applied to the table will also be applied in the CSV file.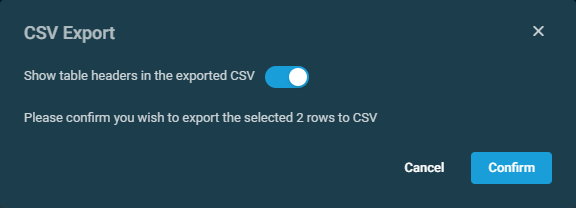 |
|
| Export All Rows to CSV |
|
This action button is available only if all rows have been selected across all pages in the table. In the confirmation dialog box that appears, click Confirm to download the file or Cancel to close out of the dialog box.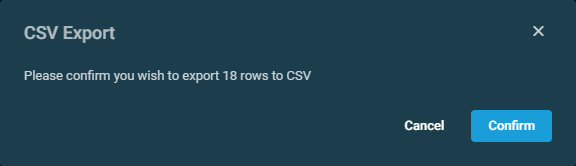 Pop-up notifications will inform you of the start and completion of the CSV export action. Click the X to close the notification; otherwise, the notification will automatically be cleared after five minutes. Any column selections, filters, and sorting that have been applied to the table will also be applied in the CSV file. |
| Create Temporary Access Password |
|
Available only when one user is selected. Refer to Create Temporary Access Password in User details. |
| Block Sign In/Unblock Sign In |
|
Available only when one user is selected. Refer to Block Sign In/Unblock Sign In in User details. |
| Revoke All User Sessions |
|
Available only when one user is selected. Refer to Revoke All User Sessions in User details. |
| Edit User |
|
Available only when one user is selected. Refer to Editing a Microsoft 365 user in Datto RMM. |
| Offboard User |
|
Available only when one user is selected. Refer to Offboarding a user or revoking a user's access. |
| Uncheck All |
|
Clears all selected rows. The number of selected rows is indicated next to the Row Actions icon. NOTE This action button is not available if all rows have been selected across all pages in the table. To clear all selected rows across all pages, use the Select none option from the drop-down arrow next to the check box in the table header. |
To access the details page for a specific user, navigate to Microsoft 365 > All Users, select a tenant, and click a User Name.
Within the Microsoft 365 menu in the left navigation menu, up to five of the most recently viewed users are listed for quick access.
When a user details page is open, you can view each of the available cards by scrolling down on the page or jump to a specific card by selecting it in the upper-left corner of the page underneath the user's name. Refer to Cards.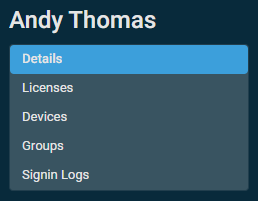
NOTE Datto RMM currently stores any user-related information, and all data securely passes through the Microsoft API.
To access all action buttons, click the More icon in the upper-right corner of the page.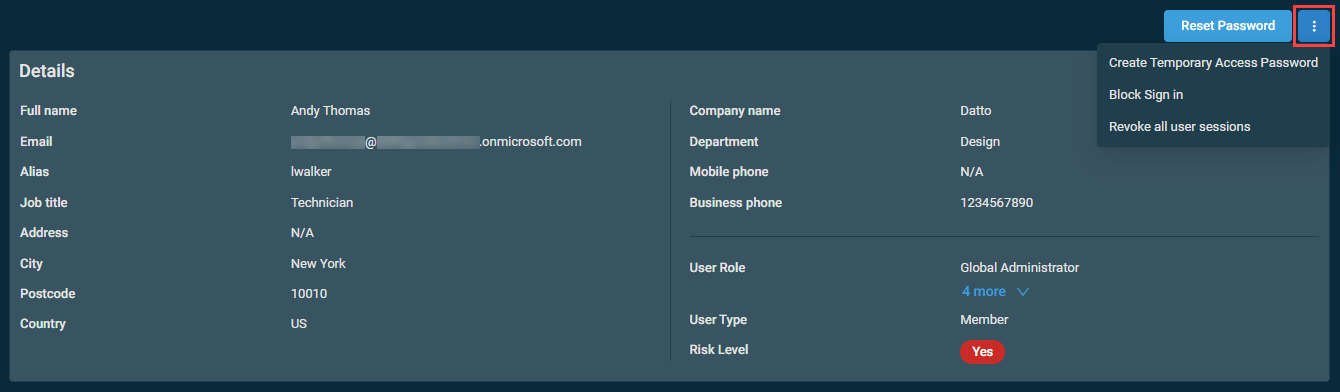
The user actions are also available on the All Users page when one user is selected in the table. Refer to Action buttons in All Users.
The following table lists all available action buttons:
| Action Button | Description |
|---|---|
| Reset Password | Upon confirmation, creates a new reset password for the selected user. Click Confirm to execute the action or Cancel to close out of the dialog box.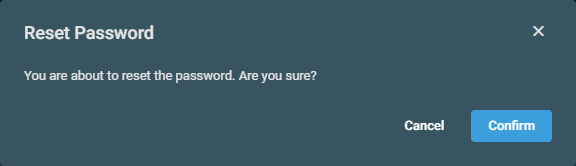 In the next dialog box that appears, click Copy Reset Password to copy the password to your clipboard. 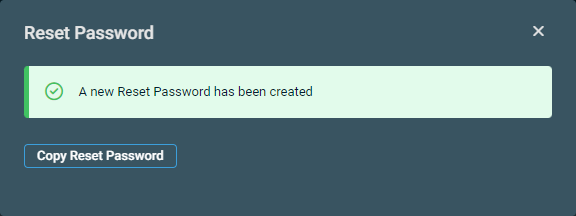 The following description from Microsoft explains the results of this action: "Copy the password and give it to the user. The user will be required to change the password during the next sign-in process. The temporary password never expires. The next time the user signs in, the password will still work, regardless how much time has passed since the temporary password was generated." |
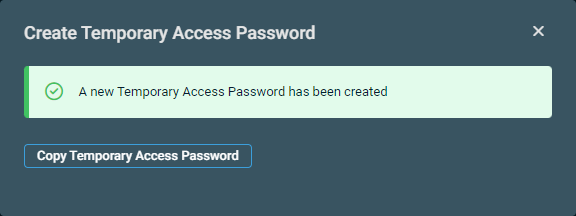
| Create Temporary Access Password |
IMPORTANT To successfully create a Temporary Access Password (TAP) for a user, their tenant must have the Temporary Access Pass policy enabled in Microsoft Entra ID, and the user must not be excluded from the policy. Learn how to enable the Temporary Access Pass policy in Microsoft Entra ID. Automatically creates a new TAP for the selected user. In the dialog box that appears, click Copy Temporary Access Password to copy the password to your clipboard.
|
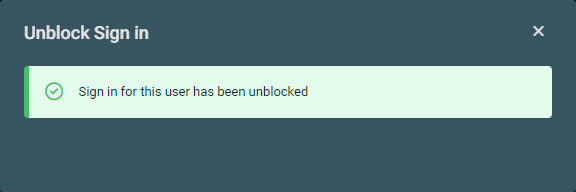
| Block Sign In/Unblock Sign In | Instantly blocks sign-ins into the user account.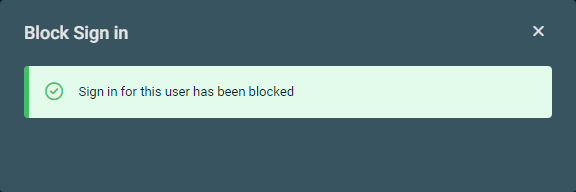 The following description from Microsoft explains the results of this action: "Blocking someone prevents anyone from signing in as this user and is a good idea when you think their password or username may have been compromised. When you block someone, it immediately stops any new sign-ins for that account, and if they’re signed in, they’ll be automatically signed out from all Microsoft services within 60 minutes." If sign-ins are currently blocked for the selected user, this option changes to Unblock Sign in, which instantly turns off the block. NOTE In the Microsoft 365 admin center, these same options are available upon selecting a user from the Active users page, and changes to this setting are immediately reflected in Datto RMM. The sign-in status of a user is displayed in the M365 Sign in Status field on the All Users page and user details page. Refer to M365 Sign In Status in All Users and M365 Sign In Status in User details. |
| Revoke All User Sessions |
Instantly revokes all user sessions for the selected user.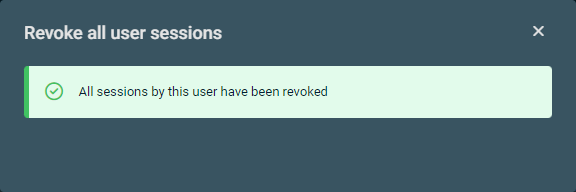 The following description from Microsoft explains the result of this action: "This will revoke all sessions for the user, requiring the user to re-sign in from all devices." |
| Edit User | |
| Offboard User |
Cards
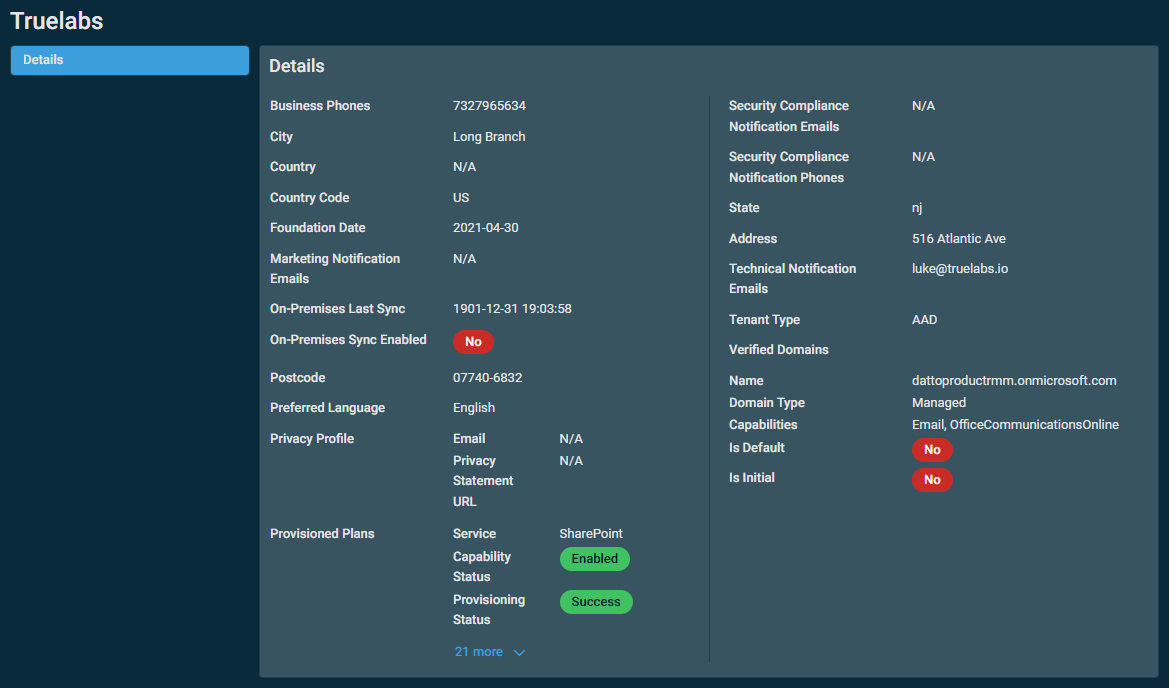
The Details card provides a summary of the selected user.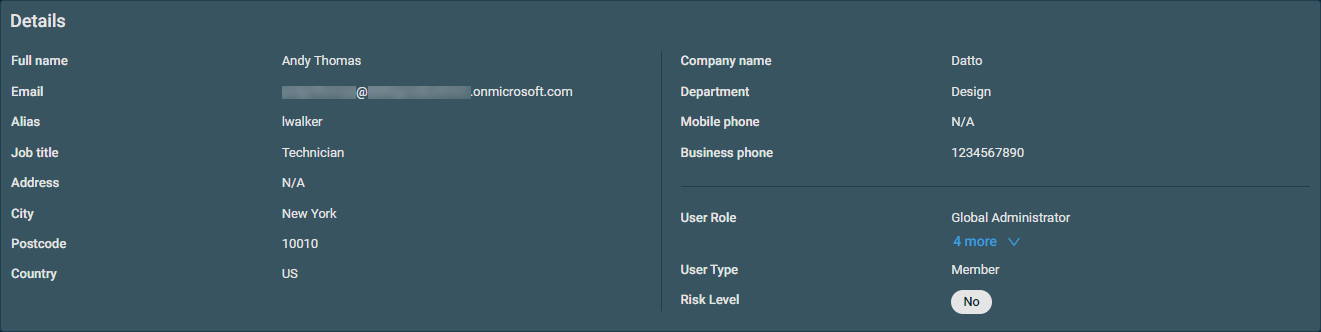
These details are retrieved from Microsoft and can be managed from the following areas:
-
NAVIGATION Microsoft 365 admin center > Users > Active users > select a user > Account tab
-
NAVIGATION Microsoft Entra ID > Users > select a user > Properties tab
The following table displays the information available in the card:
| Field | Description |
|---|---|
| Full Name | The Display name of the user as it exists in Microsoft. NOTE This field is searchable via global search. Refer to Global search. |
| User Principal Name | The username/user principal name as it exists in Microsoft. NOTE This field is searchable via global search. Refer to Global search. |
| Alias | Displayed if configured in Microsoft or via Datto RMM. Refer to Microsoft 365 user management. |
| User Type | Displays Member or Guest. |
| Job Title | Displayed if configured in Microsoft or via Datto RMM. Refer to Microsoft 365 user management. |
| Company Name | Displayed if configured in Microsoft or via Datto RMM. Refer to Microsoft 365 user management. |
| Department | Displayed if configured in Microsoft or via Datto RMM. Refer to Microsoft 365 user management. |
| Employee ID | Displayed if configured in Microsoft or via Datto RMM. Refer to Microsoft 365 user management. |
| Employee Type | Displayed if configured in Microsoft or via Datto RMM. Refer to Microsoft 365 user management. |
| Employee Hire Date | Displayed if configured in Microsoft or via Datto RMM. Refer to Microsoft 365 user management. |
| Office Location | Displayed if configured in Microsoft or via Datto RMM. Refer to Microsoft 365 user management. |
| Manager | Displayed if configured in Microsoft or via Datto RMM. Refer to Microsoft 365 user management. |
| Address | Displayed if configured in Microsoft or via Datto RMM. Refer to Microsoft 365 user management. |
| City | Displayed if configured in Microsoft or via Datto RMM. Refer to Microsoft 365 user management. |
| State | Displayed if configured in Microsoft or via Datto RMM. Refer to Microsoft 365 user management. |
| Postcode | Displayed if configured in Microsoft or via Datto RMM. Refer to Microsoft 365 user management. |
| Country | Displayed if configured in Microsoft or via Datto RMM. Refer to Microsoft 365 user management. |
| Business Phone | Displayed if configured in Microsoft or via Datto RMM. Refer to Microsoft 365 user management. |
| Mobile Phone | Displayed if configured in Microsoft or via Datto RMM. Refer to Microsoft 365 user management. |
| Displayed if configured in Microsoft or via Datto RMM. Refer to Microsoft 365 user management. | |
| Usage Location | Displayed if configured in Microsoft or via Datto RMM. Refer to Microsoft 365 user management. |
The Roles card provides a summary of the selected user's roles.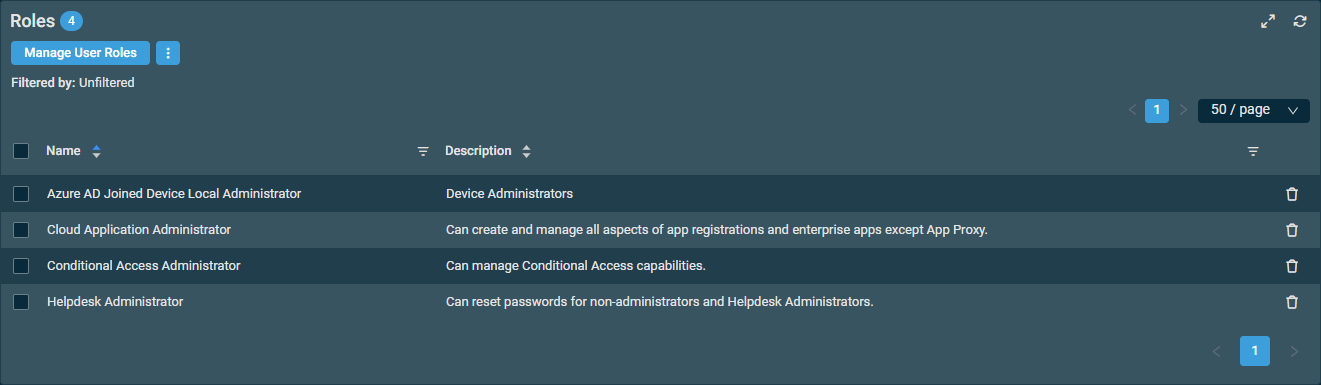
Click Manage User Roles to add or remove user roles.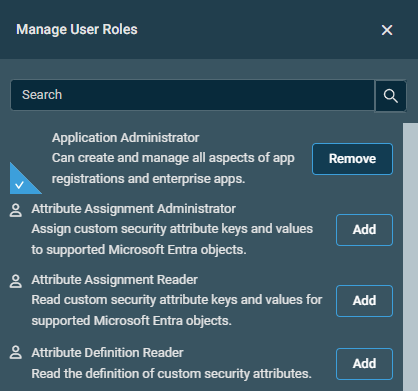
You can filter any columns with the filter icon ![]() . The Filtered by bar displays all applied column filters.If a filter search term includes wildcard characters (for example, underscores and percent signs), they serve as normal characters if they are preceded by a backslash. For details, refer to Wildcard characters.Click the X next to any filter to remove that filter or click Reset Filters to remove all filters.If no filter is applied, the Filtered by bar displays Unfiltered.The filter selection in the columns will not persist the next time the page is accessed as the table will return to the default view.
. The Filtered by bar displays all applied column filters.If a filter search term includes wildcard characters (for example, underscores and percent signs), they serve as normal characters if they are preceded by a backslash. For details, refer to Wildcard characters.Click the X next to any filter to remove that filter or click Reset Filters to remove all filters.If no filter is applied, the Filtered by bar displays Unfiltered.The filter selection in the columns will not persist the next time the page is accessed as the table will return to the default view.
The table density is set to condensed theme by default. To change it to relaxed theme, click the density toggle icon. ![]() The selection will persist across all pages.
The selection will persist across all pages.
The number of results displayed can be specified by selecting the desired number from the pagination control. This selection will persist the next time the page is accessed.
Action buttons
To access the available action buttons, click the Row Actions icon. The action buttons are unavailable if no row is selected or if the action is not applicable to the selected rows. The check boxes allow you to select one or more rows. Select all rows shown on the page by selecting the check box in the table header.
The following table lists all available action buttons:
The Licenses card provides a license summary of the selected user.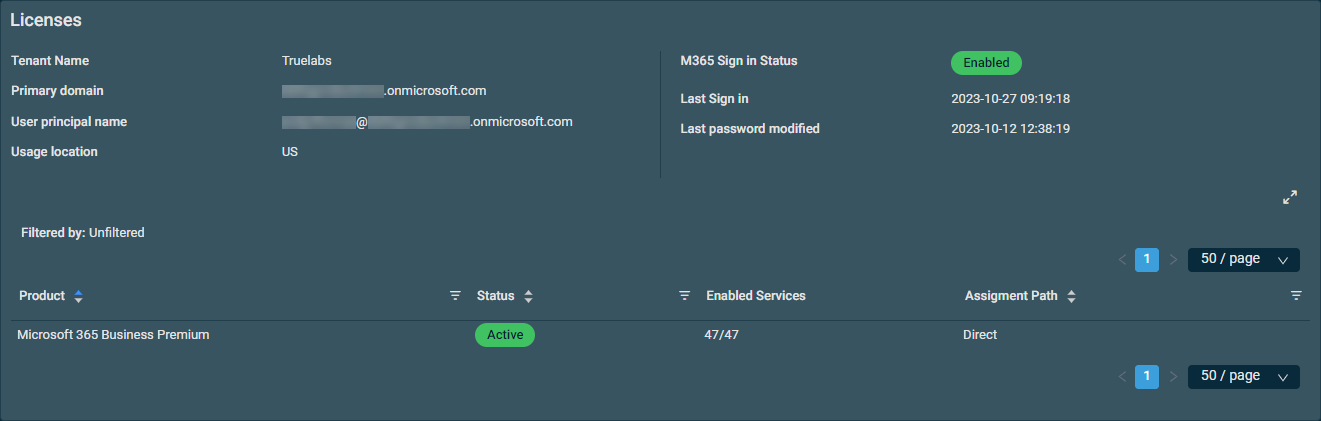
Click Manage User Licenses to add or remove user licenses.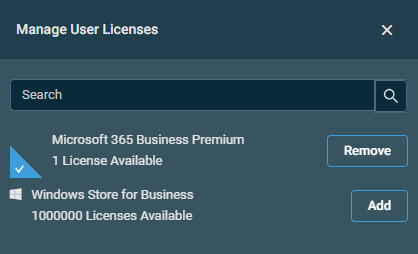
NOTE License information is retrieved live to ensure no conflicts are encountered during user creation. Upon adding a license, the license will be applied instantaneously to the user account.
These details are retrieved from Microsoft and can be managed from the following areas:
-
NAVIGATION Microsoft 365 admin center > Users > Active users > select a user > Account tab
-
NAVIGATION Microsoft Entra ID > Users > select a user > Properties tab
The following table displays the information available in the card:
| Field | Description |
|---|---|
| Tenant Name | The name of the client tenant the user belongs to, as it exists in Microsoft Entra ID. Refer to All Tenants. |
| Primary Domain | The Primary domain of the client tenant the user belongs to, as it exists in Microsoft Entra ID. |
| User Principal Name | The User principal name/Username of the user as it exists in Microsoft. |
| Usage Location | The Usage location of the user as it exists in Microsoft. |
| M365 Sign In Status |
Displays whether or not signing into this user account has been blocked, as follows:
Refer to Block Sign In/Unblock Sign In in Action buttons. |
| Last Sign In | Displays how long ago the user's latest sign-in occurred. Time stamps reflect the user time zone and preferred date format configured on the Setup > My Settings page. Hovering over any time stamp will show its date in the alternative format. Refer to User Time Zone and Date Format. The Sign in Logs card displays additional sign-in information. Refer to Signin Logs. |
| Last Password Modification | Displays how long ago the user's latest password change occurred. Time stamps reflect the user time zone and preferred date format configured on the Setup > My Settings page. Hovering over any time stamp will show its date in the alternative format. Refer to User Time Zone and Date Format. |
|
List of licenses assigned to the user |
Displays the license details, including the product, status, service enablement, and assignment path. You can filter any columns with the filter icon The table density is set to condensed theme by default. To change it to relaxed theme, click the density toggle icon. The number of results displayed can be specified by selecting the desired number from the pagination control. This selection will persist the next time the page is accessed. |
The Devices card shows devices enrolled for the user. If no devices are enrolled, the list is empty.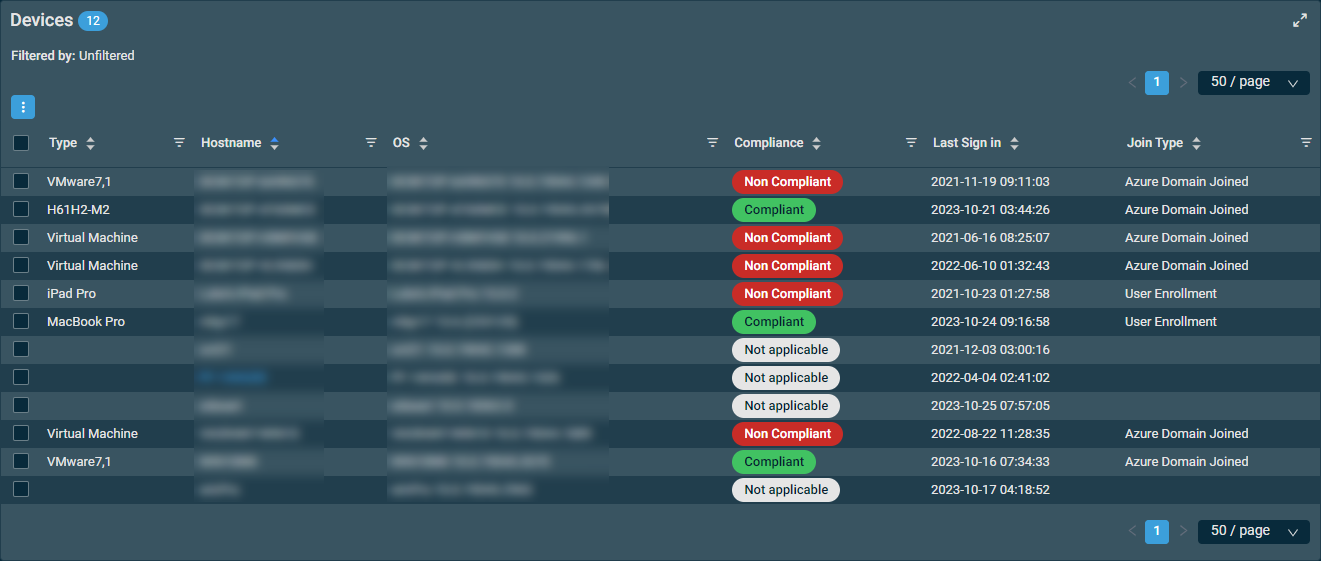
The device details are retrieved from Microsoft, and additional device properties and device management options are accessible in the following areas:
-
NAVIGATION Microsoft Entra ID > Users > select a user > Devices
-
NAVIGATION Microsoft Intune admin center > Devices (only devices enrolled to Microsoft Intune)
The badge in the table header shows the number of devices enrolled for the user.
The Column Chooser icon ![]() allows you to select which columns should be visible in the list. The following columns are available:
allows you to select which columns should be visible in the list. The following columns are available:
| Field | Sortable? | Description |
|---|---|---|
| Type (always visible) |
|
The device type. To narrow the list, click the filter icon |
| Hostname (always visible) |
|
The display name of the device as it exists in Microsoft. If the device is also enrolled in Datto RMM, the hostname is clickable. Click the link to open the device summary page. Refer to Device summary. To narrow the list, click the filter icon |
| OS (always visible) |
|
The version of the operating system on the device. To narrow the list, click the filter icon |
| Android Security Patch Level |
|
Displays the security patch level for any Microsoft 365 managed Android devices. |
| Compliance |
|
Displays whether or not the device is compliant, as follows:
Click the filter icon |
| Device Category | Displays the device's assigned category in Microsoft 365. | |
| Device Registration State | Displays the device's registration state. | |
| Encrypted | Displays the device's encryption status. | |
| Enrollment Date | Displays the date the device was enrolled as indicated by Microsoft. | |
| Enrollment Profile Name | Displays the name of the device's enrollment profile, if one is assigned. | |
| Ethernet MAC Address | Displays the device's Ethernet MAC address. | |
| Free Storage Space | Displays the device's free storage space. | |
| IMEI | Displays the IMEI number for mobile devices. | |
| Jail Broken | Displays if the device has been identified as jail broken. | |
| Join Type |
|
The method used to enroll the device. To narrow the list, click the filter icon |
| Last Sign In |
|
Displays how long ago the device was last signed into. Time stamps reflect the user time zone and preferred date format configured on the Setup > My Settings page. Hovering over any time stamp will show its date in the alternative format. Refer to User Time Zone and Date Format. |
| Last Sync Date | Displays the last time the device's data was synced with Microsoft. Time stamps reflect the user time zone and preferred date format configured on the Setup > My Settings page. Hovering over any time stamp will show its date in the alternative format. Refer to User Time Zone and Date Format. |
|
| Managed | Displays the device management status. | |
| Managed Device Name | Displays the devices Management name. This is in the format of User_OS_JoinedDate_JoinedTime. EXAMPLE A Windows device that joined with user Andy Thomas at 10:44AM on February 2, 2026 would show as andy.thomas_Windows_2/2/2026_10:44 AM. |
|
| Management Agent |
Displays the management channel of the device. EXAMPLE This field has several possible values, which include EAS, MDM, intuneClient, etc. The default value for this field is Unknown. |
|
| Management Certificate Expiration Date | Displays the device management certificate expiration date. | |
| Owner Type | Displays the ownership of the device. This can be Company, Personal, or Unknown. | |
| Partner Reported Threat State | Indicates the threat state of a device when a Mobile Threat Defense partner is in use by the account and device. | |
| Physical Memory | Displays the total memory of the device. | |
| Registration Date | Displays the device's registration date. | |
| Require User Enrollment Approval | Displays if a managed iOS device is configured for user approval enrollment. | |
| RMM Agent Status | Indicates whether the RMM agent is installed and online on enrolled Windows Intune devices.
To narrow the list, click the filter icon NOTE This column has a blank header label. |
|
| Rooted | Displays if the device has been identified as rooted. | |
| Serial Number | Displays the device's serial number. | |
| Supervised | Displays the device's supervision status. | |
| Tenant | The name of the client tenant, which the devices belongs to, as it exists in Microsoft Entra ID. | |
| Tenant ID |
The ID of the client tenant, which the devices belongs to, as it exists in Microsoft Entra ID. |
|
| Total Storage Space | Displays the devices total storage. | |
| User ID | The user name as it exists in Microsoft. | |
| User Principal Name | The username/user principal name (user email address) as it exists in Microsoft. | |
| WiFi MAC Address | Displays the device's WiFI MAC address. |
You can filter any columns with the filter icon ![]() . The Filtered by bar displays all applied column filters. If a filter search term includes wildcard characters (for example, underscores and percent signs), they serve as normal characters if they are preceded by a backslash. For details, refer to Wildcard characters. Click the X next to any filter to remove that filter or click Reset Filters to remove all filters. If no filter is applied, the Filtered by bar displays Unfiltered. The filter selection in the columns will not persist the next time the page is accessed as the table will return to the default view.
. The Filtered by bar displays all applied column filters. If a filter search term includes wildcard characters (for example, underscores and percent signs), they serve as normal characters if they are preceded by a backslash. For details, refer to Wildcard characters. Click the X next to any filter to remove that filter or click Reset Filters to remove all filters. If no filter is applied, the Filtered by bar displays Unfiltered. The filter selection in the columns will not persist the next time the page is accessed as the table will return to the default view.
The table density is set to condensed theme by default. To change it to relaxed theme, click the density toggle icon. ![]() The selection will persist across all pages.
The selection will persist across all pages.
The number of results displayed can be specified by selecting the desired number from the pagination control. This selection will persist the next time the page is accessed.
Action buttons
To access the available action buttons, click the Row Actions icon. The action buttons are unavailable if no row is selected or if the action is not applicable to the selected rows. The check boxes allow you to select one or more rows. Select all rows shown on the page by selecting the check box in the table header.
The following table lists all available action buttons:
The details of any groups the user is assigned to are retrieved from Microsoft. Learn about groups and access rights in Microsoft Entra ID.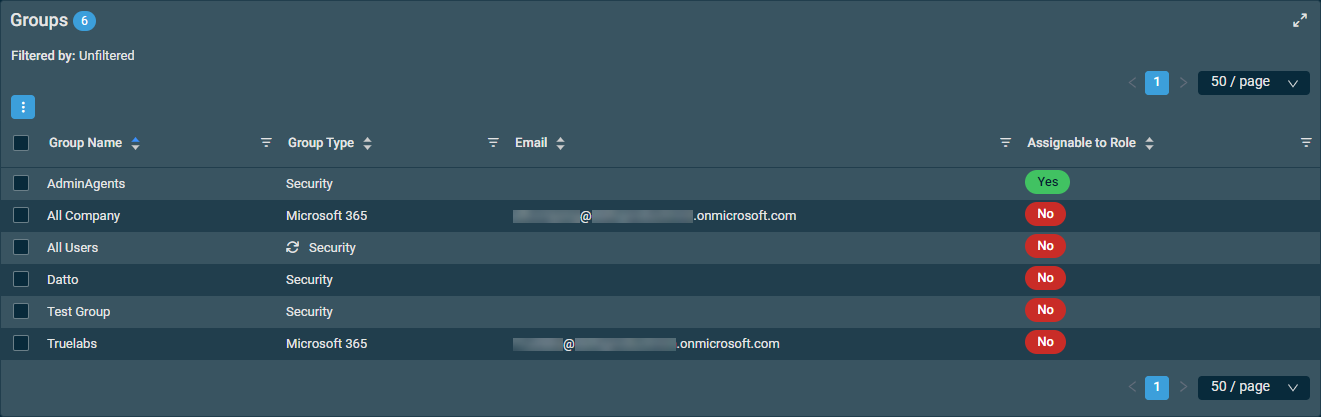
Click Manage User Groups to add or remove groups.
The badge in the table header shows the number of groups the user is assigned to. If the user is not assigned to any groups, the list is empty.
The table displays the following information:
| Field | Sortable? | Description |
|---|---|---|
| Group Name |
|
The name of the group as it exists in Microsoft. To narrow the list, click the filter icon |
| Group Type |
|
The group type, as set in Microsoft. To narrow the list, click the filter icon |
|
|
The email address of the group as it exists in Microsoft. To narrow the list, click the filter icon |
|
| Assignable to Role |
|
Displays whether or not the group can be assigned to roles, as follows:
Learn about using Azure AD groups to manage role assignments. Click the filter icon |
You can filter any columns with the filter icon ![]() . The Filtered by bar displays all applied column filters.If a filter search term includes wildcard characters (for example, underscores and percent signs), they serve as normal characters if they are preceded by a backslash. For details, refer to Wildcard characters. Click the X next to any filter to remove that filter or click Reset Filters to remove all filters. If no filter is applied, the Filtered by bar displays Unfiltered. The filter selection in the columns will not persist the next time the page is accessed as the table will return to the default view.
. The Filtered by bar displays all applied column filters.If a filter search term includes wildcard characters (for example, underscores and percent signs), they serve as normal characters if they are preceded by a backslash. For details, refer to Wildcard characters. Click the X next to any filter to remove that filter or click Reset Filters to remove all filters. If no filter is applied, the Filtered by bar displays Unfiltered. The filter selection in the columns will not persist the next time the page is accessed as the table will return to the default view.
The table density is set to condensed theme by default. To change it to relaxed theme, click the density toggle icon. ![]() The selection will persist across all pages.
The selection will persist across all pages.
The number of results displayed can be specified by selecting the desired number from the pagination control. This selection will persist the next time the page is accessed.
Action buttons
To access the available action buttons, click the Row Actions icon. The action buttons are unavailable if no row is selected or if the action is not applicable to the selected rows. The check boxes allow you to select one or more rows. Select all rows shown on the page by selecting the check box in the table header.
The following table lists all available action buttons:
The sign-in logs are retrieved from Microsoft. Learn about sign-in logs in Microsoft Entra ID.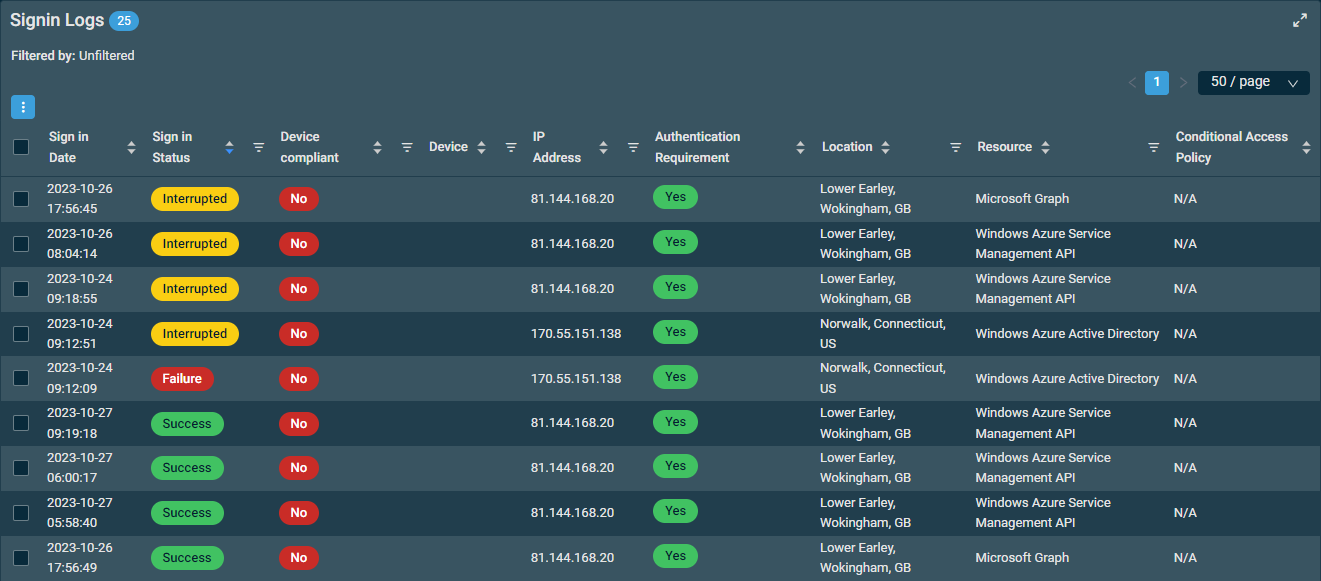
The badge in the table header shows the number of user sign-ins logged. If no sign-ins are logged, the list is empty.
The table displays the following information:
| Field | Sortable? | Description |
|---|---|---|
| Sign In Date |
|
Displays how long ago the sign-in occurred. Time stamps reflect the user time zone and preferred date format configured on the Setup > My Settings page. Hovering over any time stamp will show its date in the alternative format. Refer to User Time Zone and Date Format. |
| Sign In Status |
|
Displays if the sign-in occurred with our without errors. Click the filter icon |
| Device compliant |
|
Indicated whether or not the device the user logged in to is compliant. Click the filter icon |
| Device |
|
The hostname of the device, if available from Microsoft. To narrow the list, click the filter icon |
| IP Address |
|
The IP address the sign-in occurred from. Microsoft provides the following description of IP addresses in relation to sign-ins: "There's no definitive connection between an IP address and where the computer with that address is physically located. Mobile providers and VPNs issue IP addresses from central pools that are often far from where the client device is actually used. Currently, converting IP address to a physical location is a best effort based on traces, registry data, reverse lookups and other information." To narrow the list, click the filter icon |
| Authentication Requirement |
|
Displays if authentication was required for the sign-in. |
| Location |
|
The town, state, and country associated with the IP address the sign-in occurred from. To narrow the list, click the filter icon |
| Resource |
|
The resource used to sign in. To narrow the list, click the filter icon |
| Conditional Access Policy |
|
Displays any Microsoft Conditional Access policies that applied to the user and application during sign-in. If no policy applied, the field displays N/A. Refer to Conditional Access Status. To narrow the list, click the filter icon |
You can filter any columns with the filter icon ![]() . The Filtered by bar displays all applied column filters. If a filter search term includes wildcard characters (for example, underscores and percent signs), they serve as normal characters if they are preceded by a backslash. For details, refer to Wildcard characters. The Filtered by bar displays all applied column filters. Click the X next to any filter to remove that filter or click Reset Filters to remove all filters. If no filter is applied, the Filtered by bar displays Unfiltered. The filter selection in the columns will not persist the next time the page is accessed as the table will return to the default view.
. The Filtered by bar displays all applied column filters. If a filter search term includes wildcard characters (for example, underscores and percent signs), they serve as normal characters if they are preceded by a backslash. For details, refer to Wildcard characters. The Filtered by bar displays all applied column filters. Click the X next to any filter to remove that filter or click Reset Filters to remove all filters. If no filter is applied, the Filtered by bar displays Unfiltered. The filter selection in the columns will not persist the next time the page is accessed as the table will return to the default view.
The table density is set to condensed theme by default. To change it to relaxed theme, click the density toggle icon. ![]() The selection will persist across all pages.
The selection will persist across all pages.
The number of results displayed can be specified by selecting the desired number from the pagination control. This selection will persist the next time the page is accessed.
Action buttons
To access the available action buttons, click the Row Actions icon. The action buttons are unavailable if no row is selected or if the action is not applicable to the selected rows. The check boxes allow you to select one or more rows. Select all rows shown on the page by selecting the check box in the table header.
The following table lists all available action buttons:
To access the All Devices page, navigate to Microsoft 365 > All Devices.
By default, the page displays all devices across all tenants. To populate a list of devices from specific tenants, select one or more tenants from the Select Tenant drop-down menu.

You can filter by one or more tenants using the filter icon ![]() in the Tenant Name column. Refer to Tenant Name.
in the Tenant Name column. Refer to Tenant Name.
You can also open this list from the All Tenants page. Click View Devices in the Devices column next to a tenant to view a list of all devices in that tenant. Refer to Devices in List of tenants.
The badge in the table header shows the number of devices in the currently displayed list, whether filtered or unfiltered.
The Column Chooser icon ![]() allows you to select which columns should be visible in the list. The following columns are available:
allows you to select which columns should be visible in the list. The following columns are available:
| Field | Sortable? | Description |
|---|---|---|
| Hostname (default, always visible) |
|
The display name of the device as it exists in Microsoft. To narrow the list, click the filter icon |
| Tenant (default) |
|
The name of the client tenant, which the devices belongs to, as it exists in Microsoft Entra ID. To narrow the list, click the filter icon NOTE You can change the selected tenant from the Select Tenant drop-down menu at the top of the page. |
| User Principal Name (default) |
|
The username/user principal name (user email address) as it exists in Microsoft. |
| Compliant (default) |
|
Displays whether or not the device is compliant, as follows:
Click the filter icon |
| Operating System (default) | The version of the operating system on the device. To narrow the list, click the filter icon |
|
| Join Type (default) |
|
The method used to enroll the device. To narrow the list, click the filter icon |
| Enrollment Date (default) |
|
Displays the date the device was enrolled in Microsoft 365 |
| Last Sign In (default) |
|
Displays how long ago the device was last signed into. Time stamps reflect the user time zone and preferred date format configured on the Setup > My Settings page. Hovering over any time stamp will show its date in the alternative format. Refer to User Time Zone and Date Format. |
| Android Security Patch Level |
|
Displays the security patch level for any Microsoft 365 managed Android devices. |
| Device Category |
|
Displays the device's assigned category in Microsoft 365, if assigned. |
| Device Registration State |
|
Displays the device's registration state. |
| Email Address |
|
Displays the email or emails for the user associated with the device. |
| Enrollment Profile Name |
|
Displays the name of the device's enrollment profile, if one is assigned. |
| Ethernet MAC Address | Displays the device's Ethernet MAC address. | |
| Free Storage Space |
|
Displays the device's free storage space. |
| IMEI | Displays the IMEI number for mobile devices. | |
| Is Encrypted |
|
Displays the device's encryption status. |
| Is Supervised |
|
Displays the device's supervision status. |
| Jail Broken |
|
Displays if the device has been identified as jail broken. |
| Last Sync Date Time |
|
Displays the last time the device's data was synced with Microsoft. |
| Managed Device Name |
|
Displays the devices Management name. This is in the format of User_OS_JoinedDate_JoinedTime. EXAMPLE A Windows device that joined with user Andy Thomas at 10:44AM on February 2, 2026 would show as andy.thomas_Windows_2/2/2026_10:44 AM. |
| Managed Device Owner Type |
|
Displays the ownership of the device. This can be Company, Personal, or Unknown. |
| Management Agent |
|
Displays the management channel of the device. EXAMPLE This field has several possible values, which include EAS, MDM, intuneClient, etc. The default value for this field is Unknown. |
| Management Certificate Expiration Date |
|
Displays the device management certificate expiration date. |
| Partner Reported Threat State |
|
Indicates the threat state of a device when a Mobile Threat Defense partner is in use by the account and device. |
| Physical Memory |
|
Displays the total memory of the device. |
| Registration Date | Displays the device's registration date. | |
| Require User Enrollment Approval |
|
Displays if a managed iOS device is configured for user approval enrollment. |
| Serial Number | Displays the device's serial number. | |
| Total Storage Space |
|
Displays the devices total storage. |
| WiFi MAC Address | Displays the device's WiFI MAC address. |
The columns can be reordered and resized. The order and size of the columns will persist the next time the page is accessed.
You can filter any columns with the filter icon ![]() . The Filtered by bar displays all applied column filters.If a filter search term includes wildcard characters (for example, underscores and percent signs), they serve as normal characters if they are preceded by a backslash. For details, refer to Wildcard characters.Click the X next to any filter to remove that filter or click Reset Filters to remove all filters.If no filter is applied, the Filtered by bar displays Unfiltered.The filter selection in the columns will persist the next time the page is accessed.
. The Filtered by bar displays all applied column filters.If a filter search term includes wildcard characters (for example, underscores and percent signs), they serve as normal characters if they are preceded by a backslash. For details, refer to Wildcard characters.Click the X next to any filter to remove that filter or click Reset Filters to remove all filters.If no filter is applied, the Filtered by bar displays Unfiltered.The filter selection in the columns will persist the next time the page is accessed.
The table density is set to condensed theme by default. To change it to relaxed theme, click the density toggle icon. ![]() The selection will persist across all pages.
The selection will persist across all pages.
The number of results displayed can be specified by selecting the desired number from the pagination control. This selection will persist the next time the page is accessed.
Action buttons
To access all action buttons, click the Row Actions icon.
The action buttons are unavailable or become unavailable if no row is selected in the table or if the action button is not applicable to the selected rows. The check boxes allow you to select one or more rows. Select all rows shown on a page by selecting the check box in the table header.
Intune Quick Actions can be performed within the Microsoft 365 Integration for Intune-enrolled devices. This feature is supported for Windows, Android, and iOS devices, with macOS and additional functionality to follow in a future release.
Intune Quick Actions will allow you to perform the following actions:
- Remote Lock: Lock a device remotely, requiring the user to enter a PIN or password.
- Wipe Device: Restore a device to factory default settings, ready to be enrolled with the same or different M365 user. When initated, choose from the following options:
- Keep enrollment data: Resets the device to factory settings while keeping its Intune and Entra ID enrollment. All user data and apps are removed, and the device is automatically re-provisioned without requiring re-enrollment
- Keep user data: Removes Intune management and corporate policies while keeping the user’s personal data. The device is unenrolled from Intune and Entra ID, but user files and profiles remain on the device.
- Retire Device: Completely wipe and remove a device from Intune management.
- Sync Device: Request a immediate device sync to retrieve Intune policies and configurations.
- Reboot Now: Restarts the device immediately by closing all applications and reloading the system.
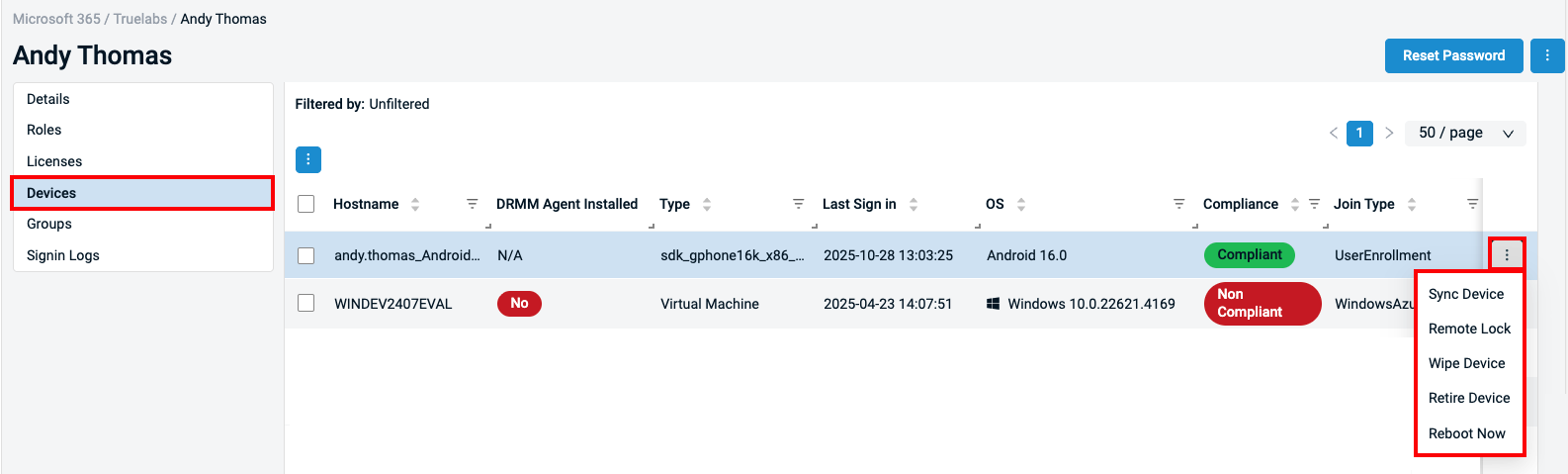
After selecting any Intune Quick Action, you will be required to confirm your intended action, and will receive a confirmation message when the action has completed.
Prerequisites and additional notes:
- You need to reconfigure your existing Microsoft 365 integration before use, as it requires consent for new Intune permissions.
NOTE Reconfiguration is only needed if the Microsoft 365 integration was enabled before Datto RMM version 14.7.0.
- To perform Intune Quick Actions on Intune enrolled Windows devices, a Datto RMM agent needs to be installed.
- You can perform Intune Quick Actions on Intune and EntraID user-enrolled Android and iOS devices without an additional license.
- MacOS Intune Quick Actions will be available in Q1 2026.
How to...
Complete the following steps in Datto RMM to enable the integration:
- Navigate to Setup > Integrations > Microsoft 365.
- In the Authenticate tab, which is selected by default, click Turn On.
- In the Tenant ID field that appears, enter your tenant ID for the CSP tenant you wish to integrate. This tenant ID must match the CSP tenant of the account you authenticate with in step 6.
- Click Save.
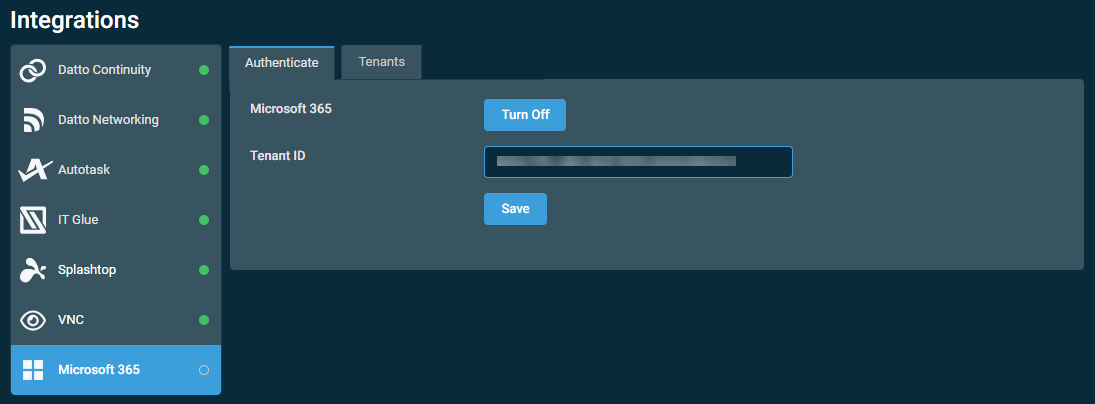
- The button will change in appearance and show that Datto RMM is in the process of integrating.
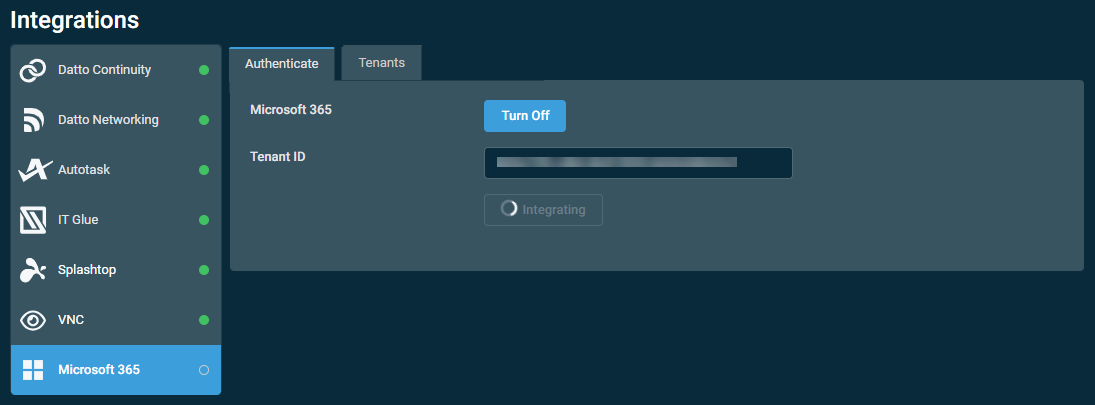
- Datto RMM will redirect to the Microsoft login page. Select or add the account that corresponds with the tenant ID entered in step 3.
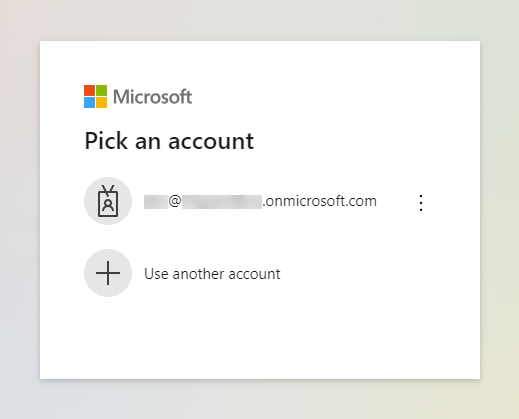
- If not already signed in, sign in to the account.
- Once successfully signed in, Microsoft will display a list of requested permissions. For more information, refer to API permissions in Prerequisites. Click Accept.
- The page will redirect to Datto RMM, where you will see a list of client tenants in the Tenants tab of the Microsoft 365 card. You must manually sync tenants to begin using the integration. For instructions, refer to Sync Microsoft 365 client tenants to Datto RMM.
NOTE To learn how to find your tenant ID, refer to this Microsoft article.
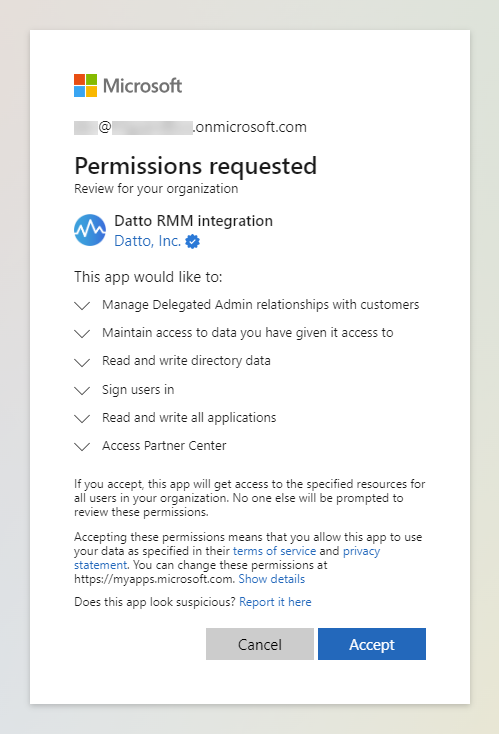
The Microsoft 365 Integration is now successfully enabled.
NOTE You can check the status of the integration any time from the Authenticate tab in the Microsoft 365 card. If enabled, the button in the card displays Saved and authenticated.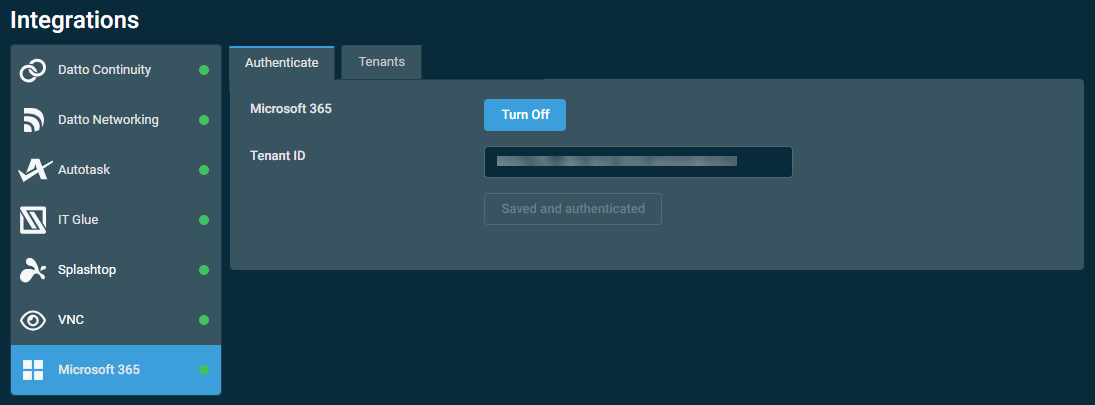
BEFORE YOU BEGIN Refer to Enable the Microsoft 365 Integration.
Once the Microsoft 365 Integration is enabled, Datto RMM automatically fetches all of your Microsoft 365 client tenants. The status of all tenants remains Deactivated in the tenant sync table until manually synced.
NOTE Your own tenant (the primary tenant) can be synced but cannot be unsynced.
For details about the full functionality available in the tenant sync table, refer to Client tenant syncing.
Steps
To sync tenants, complete the following steps:
- Navigate to Setup > Integrations > Microsoft 365 > Tenants.
- Select the tenants you wish to sync. For details about check box selection functionality, refer to Action buttons.
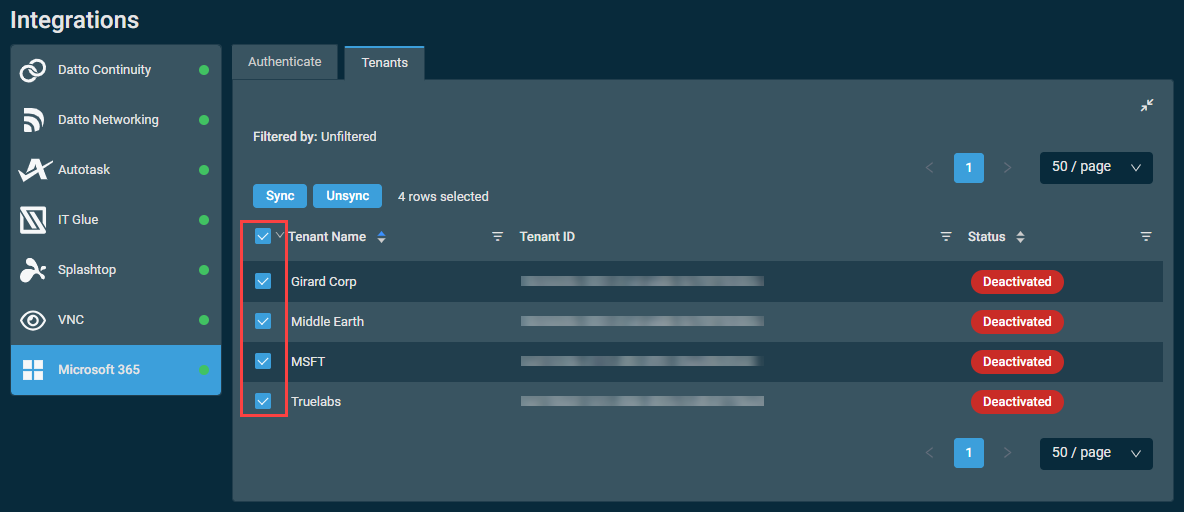
- Click Sync.
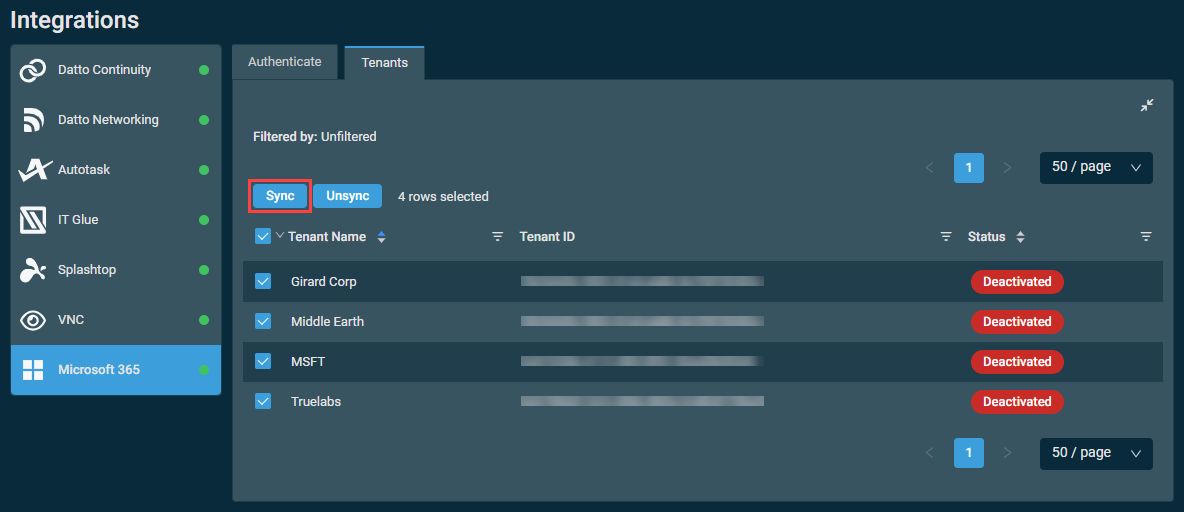
- In the confirmation dialog box that appears, click Confirm to complete the action or Cancel to close out of the dialog box. A pop-up notification will indicate if the tenant sync operation has initiated.
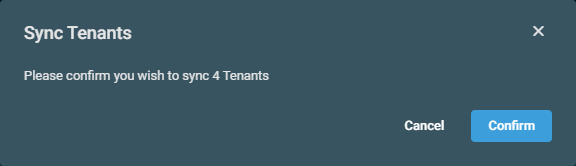
- The sync process may take some time. You will notice the status of syncing tenants changes to Pending.
- The status Synced indicates a tenant has been successfully synced.

Datto RMM automatically creates an enterprise application in Microsoft Entra ID for each of the client tenants you have GDAP access to. Learn about GDAP. Application creation requires a couple seconds per tenant.
Synced tenant data and user data are now accessible from the Microsoft 365 menu in the left navigation menu.
NOTE If a synced tenant does not show on the All Tenants page, verify your Microsoft configuration meets the prerequisites of this integration. Refer to Prerequisites.
NOTE Specific tenants can be unsynced at any time. Refer to Unsync Microsoft 365 client tenants from Datto RMM.
The status Synced in the tenant sync table indicates a tenant is currently synced to Datto RMM, but specific tenants can be unsynced at any time.
For details about the full functionality available in the tenant sync table, refer to Client tenant syncing.
Steps
To unsync tenants, complete the following steps:
- Navigate to Setup > Integrations > Microsoft 365 > Tenants.
- Select the tenants you wish to unsync. For details about check box selection functionality, refer to Action buttons.
- Click Unsync.
- In the confirmation dialog box that appears, click Confirm to complete the action or Cancel to close out of the dialog box. A pop-up notification will indicate if the tenant unsync operation has initiated.
- The unsync process may take some time.
- The status Deactivated indicates a tenant has been successfully unsynced.
Data for any unsynced tenants are no longer accessible from the Microsoft 365 menu in the left navigation menu.
NOTE Specific tenants can be resynced at any time. Refer to Sync Microsoft 365 client tenants to Datto RMM.
If you disable the integration, all of the integration and authentication settings will be deleted. Any enterprise applications that had been created for previously synced client tenants will be automatically deleted from Microsoft Entra ID. You can re-enable the integration at any time.
- In Datto RMM, navigate to Setup > Integrations.
- The Datto Continuity tab is selected by default. Click the Microsoft 365 tab.
- Click Turn Off.
- Click Confirm to execute the action or Cancel to close out of the dialog box.