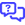Best practices for Patch Management
Introduction
Datto RMM provides two different policy types to configure device patching: Windows Update and Patch Management.
This guide explains how to use these policies to control how your Windows PCs download, install, and report back data on Windows updates. It is intended for users who are new to Datto RMM, but the information may be relevant to users looking to refine their existing setups.
IMPORTANT It is recommended to follow this guide as closely as possible.
Once you are familiar with how Patch Management works in Datto RMM, you can then introduce customizations by adjusting policies or by using overrides to configure behaviors for device subsets requiring more precise care (for example, SQL Servers).
Applicable operating systems
- Windows 10 and Windows 11: This guide focuses on the current Windows-as-a-Service operating systems, which are still receiving standard updates.
- Windows Server 2016 and newer: Because these operating systems are built on the Windows 10 (or newer) codebase, significant portions of this guide apply to them.
NOTE This guide will indicate where server and workstation operating systems demand separate configurations.
Not applicable
- Pre-Windows 10 desktop versions (discontinued).
NOTE In a case where an older Windows OS receives an out-of-band update (for example, to patch a high-severity issue being actively exploited), consult the Windows Update Catalog for a download link to the relevant MSU file, which you will use alongside the Download and Apply Windows Update File components available from the ComStore.
- This guide has not been tested for relevance with devices receiving Extended Security Updates (ESUs). Some or all of the information may not be pertinent to such devices.
Outline
As follows is an outline of what this guide will instruct you to do. If you are already experienced or on a tight deadline, this outline will prove sufficient.
- (Optional) Run the Windows Update Toolkit component to ensure devices are patching properly and have expected WSUS options set. Refer to Step 0: Health check (optional).
- Using a Windows Update policy:
- Disable automatic updates. Refer to Disable automatic updates.
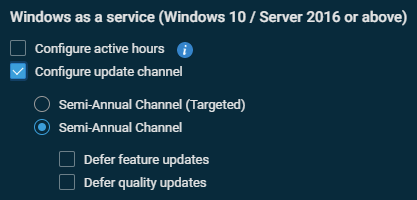
- Configure the update channel to Semi-Annual Channel (or Use Windows Update for Business) and enable quality and feature update deferrals for one or two weeks. Refer to Configure update channels and deferrals.
- Configure active hours in line with devices' typical working hours. Refer to Configure active hours.
- Using a Patch Management policy:
- Schedule Patch Management policies to run at noon on weekdays for workstations and under your own configuration for servers.
- Configure reboots to happen outside of working hours, with a reminder for the user if the device is not available during reboot time.
- Approve updates older than X days (where X is the deferment period you configured in your Windows Update policy).
- (Optional) Alternatively, approve updates with the Security Update or Critical Update category.
- Approve updates that do not contain the word Driver in the title except for on Microsoft Surface devices.
- Do not approve updates with a type or category containing the word Driver except on Microsoft Surface devices.
- Do not approve updates with a description or title containing the word Preview.
Refer to Step 2: Configuring Patch Management policies for servers and workstations.
- Also discussed:
- How to use and not to use the Manual approval section of a Patch Management policy. Refer to Manual update approval.
- Specific use cases for devices like Hyper-V servers. Refer to Other considerations.
- Feature updates and enablement packages. Refer to Step 3: Handling feature updates.
Step 0: Health check (optional)
If you are newly onboarding devices into Datto RMM, we recommend running the Windows Update Toolkit component from the ComStore on them. Refer to ComStore.
In addition to providing a complete update and OS history of each device, which may be useful for bookkeeping, the component provides insight into the following:
- How devices are configured today (WSUS, deferrals, and so forth)
- If you are running Datto RMM with a Patch Management policy already configured, is it producing errors?
- Or, did a previous Datto RMM installation leave remnant files that are interfering with the configuration?
- Can the device connect successfully to the Windows Update service to download the updates it needs?
- Is the Windows Update Agent installed on the OS causing patch audit failures? Refer to Patch status "No Data" on Windows 10 and 11 devices due to "0x8002802B" error. .
Run the Windows Update Toolkit component
Running the component against a device will place data into a user-defined field (UDF), if configured, which can then be filtered against to catch devices with specific configurations. Refer to User-defined fields and Device filters.
To run Windows Update Toolkit on a device or devices, complete the following steps:
- From the ComStore, download the Windows Update Toolkit component. Refer to Component Library.
- Select a device to run the component against. Depending on your use case, you may select multiple, an entire site, or the output of a filter. Refer to Device filters.
- Instruct the devices to run a quick job or scheduled job with the Windows Update Toolkit component as its payload. Refer to Scheduled jobs and Quick jobs.
- This component writes a summarized output to a UDF so it can be used to filter against.
Ensure you select a UDF from 1-30 to write this data to and remember which one you selected. - You shouldn’t need to enable any of the other options (Clear WSUS, Reset WUA, and so forth) yet.
- This component writes a summarized output to a UDF so it can be used to filter against.
- Leave some time for the job to complete.
- Once your devices have run the component, you will be able to filter on the summary UDF.
Identify devices requiring attention
The aim of this exercise is to round up devices with specific configurations that will require closer attention. To do this, you will need to know how the toolkit responds to what it finds.
Review the following table to learn how to craft your filters to catch the devices warranting closer inspection.
NOTE Only some of these flags indicate an issue with the device. Most are provided as a point of reference.
| Situation | Explanation | Denoted as |
|---|---|---|
| WSUS configuration found | Device is using WSUS to download updates. | [WSUS] |
| Long-term servicing channel | Device is running an LTSC version of Windows. | [LTSC] |
| Quality update deferrals active | Device is deferring acceptance of quality updates. | [DefQuality] |
| Feature update deferrals active | Device is deferring acceptance of feature updates. | [DefFeature] |
| Target release version set | Device has been instructed not to update past a certain Windows version. | [TargetSet] |
| Delivery Optimization in use | Device is downloading updates from other devices on the network. | [DOptimis] |
| Bad WUA version found | Device's WUA version is faulty and must be repaired. Refer to Patch status "No Data" on Windows 10 and 11 devices due to "0x8002802B" error. . | [BadWUA] |
| Patch auditing failures in log | Device requires attention: patch audits have failed recently. | [AuditFail] |
| Patching failures in log | Device requires attention: patching failures have failed recently. | [PatchFail] |
| Patch policy present on device | A patch policy is present on the device and is being used by the Agent. | [Policy] |
| No patch policy present on device | No patch policy is present on the device and is being used by the Agent. | [NoPolicy] |
Once you have produced a filter looking for devices outside of your accepted margins (for example, WSUS or Bad WUA or Patch Policy present), run the filter to find the devices that match its criteria.
If you find no devices, or if the devices found are known to you, you can proceed knowing that Datto RMM Patch Management should be adequate to use for your devices.
Step 1: Configuring a Windows Update policy
Windows Update policies determine how devices detect which patches are relevant for it and how they are handled. Refer to Windows Update policy.
Expand this section to learn how to disable automatic updates, configure the Semi-Annual update channel (or Windows Update for Business), enable week-long deferrals for feature and quality updates, configure active hours, and learn about other settings and options.
Disable automatic updates
Patch Management operates as a lift-in replacement to Windows’s own handling of updates. To prevent Windows from updating itself out of schedule and confusing matters, we suggest disabling automatic updates by selecting Turn off automatic updates from the Update Options drop-down menu.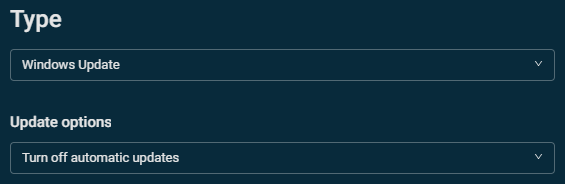
Disabling automatic updates does not stop Windows from updating itself like it did for Windows XP-8.1 but rather introduces a long delay before the system updates by force. By introducing updates via a separate stream during this delay, Datto RMM keeps the system up to date and mitigates the need for the OS to update itself out of schedule.
Configure active hours
Active hours denote the hours of the day when you expect the device to be in use and it should not be forcibly rebooted, even when an important update requires a reboot to be applied. Configure active hours only applies if using any update option besides Turn off automatic updates, so you can leave this unchecked.
Configure update channels and deferrals
To configure update deferral, the device must have Windows Update for Business enabled. To do this, select the Configure update channel check box (or Use Windows Update for Business) option.
NOTE Semi-Annual Channel (Targeted) and Semi-Annual Channel serve the same purpose. The parent option may read Configure update channel or Use Windows Update for Business.
Defer feature updates: Feature updates (which update Windows to a year scheme, for example 22H2) can be deferred to the user’s preference, especially if Windows Update components are preferred for this task.
Defer quality updates: Datto recommends setting a deferral period of between one and two weeks for quality updates. This option causes updates that have been available for less than the stated time to not appear in patch scans, which allows the community at large to test them before they filter down to mission-critical systems.
Other options
- Receive updates for other Microsoft products when Windows is updated should be enabled to ensure all updates are delivered.
- Configure Windows Server Update Services (WSUS) settings should be configured only if you need your devices to use a WSUS server.
- Allow devices to share updates within(/outside) the local network can be configured to save some internal bandwidth and allow devices to share update data between each other.
- Disable Windows Fast Startup to allow update installation on shutdown as well as reboot should be enabled, as it permits devices to install updates when shutting down.
NOTE Leaving this blank will not remove an existing WSUS configuration. You will need to use the Windows Update Toolkit component to do that.
IMPORTANT Save your policy and then create a new one for the next step of this guide. Switching policy types from the Type drop-down menu will overwrite any configured settings.
Step 2: Configuring Patch Management policies for servers and workstations
IMPORTANT A device should have only one Patch Management policy targeting it at any given time. Datto recommends using separate policies for servers and workstations. This guide provides scheduling recommendations for both.
Patch Management policies determine which patches are selected for installation and when they are processed by the device. Refer to Patch Management policy.
Expand the following sections to learn how to configure Patch Management policies and why you should exclude Preview-type updates and Driver updates while permitting important updates.
A Patch Management policy can be configured as Scheduled or Audit only. The latter type will only perform patch scans to provide a summary of a device’s patching status.
Scheduling a policy allows it to not only perform patch scans but to download and install those updates on a schedule predefined by the administrator.
Datto recommends using separate policies for workstations and servers with the same approval criteria but different scheduling options:
- For servers, it is recommended to run the policy at a time when the device can be taken offline and to configure the policy to reboot the device immediately after it is finished to minimize downtime. Ideally, this cadence would be weekly; it should not be any longer than monthly.
- For workstations, our team often recommends partners schedule patch runs daily at noon, as this roughly corresponds to lunchtime. Employees will leave their computers for a break, during which time the device can download and process updates. Instead of rebooting workstations when patching is complete, the Power setting should be set to Do not restart, with Display a restart reminder to users checked. Setting reboot reminders to show up every 4-6 hours gives users a frequent but not annoying reminder to reboot their device to finish applying windows updates when needed.
The daily cadence allows devices to receive updates very quickly after their release (or their cleared release if you are using deferrals); it is also easier to formalize a schedule around.
Of course, you will need to arrive at a schedule which best accommodates both your and your customers' schedules. These recommended times are proposed as a best-fit only.
A common use case is to install typical updates on a schedule but to formalize separate approval behaviors for Critical and Security updates. Historically, this was a sensible solution, but its effectiveness is severely reduced in the Windows-as-a-Service era.
Microsoft is generally unreliable at properly tagging updates with a valid criticality metric, rendering any policy leaning on this as a deciding factor fragile. As updates are no longer divided separately but rather delivered cumulatively, it is no longer possible to segregate updates by criticality and install them earlier unless they are released out of band, in which case they may not appear as part of a patch scan at all.
An additional optional step is included in the following template for users who wish to allow properly tagged updates to leapfrog the time-release process.
NOTE There is no guarantee that an update will be properly tagged in order to trigger this additional criterion.
To install a critical or out-of-band update outside of a policy, Datto recommends using the Download and Apply Windows Update File components from the ComStore. By running the relevant component with a download link for the desired update sourced from the Windows Update Catalog, updates can be pushed proactively to devices en masse without using or adjusting a Patch Management policy.
This can be used for out-of-band updates that do not show in patch scans or would normally be blocked because they have not been available long enough.
Automatic approval is the first approval phase of a Patch Management policy. We recommend using the later Manual approval section to block individual updates. Refer to Manual update approval.
Datto recommends automatically approving the bulk of updates a system indicates it requires, provided that many updates are cumulative, and only filtering out drivers and previews.
Installation of drivers via Windows Update is generally not recommended. Tools such as Dell Command | Update and HP Support Assistant will generally do a much better job of keeping drivers updated.
NOTE Microsoft Surface devices are treated separately, as they receive all their drivers from the same source creating them, making them generally more accurate. Refer to Device filters to learn how to set up a filter to catch Microsoft Surface devices.
Preview updates should be avoided, as they amount to beta software.
Non-Microsoft Surface devices
Approve patches that match the following criteria:
Release date / older than 7 days (or older than 14 days, depending on how you configured your Windows Update policy)
(Optional) [OR] Category / contains / Security Update OR Critical Update
Do not approve patches that match the following criteria:
Type / equal to / Driver
[OR] Category / contains / Drivers
[OR] Title / contains / Preview
[OR] Description / contains / Preview
Microsoft Surface devices
Approve patches that match the following criteria:
Release date / older than 7 days (or older than 14 days, depending on how you configured your Windows Update policy)
(Optional) [OR] Category / contains / Security Update OR Critical Update
Do not approve patches that match the following criteria:
Title / contains / Preview
[OR] Description / contains / Preview
NOTE As noted, there is no guarantee that an update deserving of Critical status will receive it.
The best practice when configuring automatic approval is to assume no update will be tagged for severity and to treat all updates the same.
The above optional condition will permit properly tagged updates to leapfrog the minimum-age limit for updates, provided it has been given the correct metadata.
Localization of update titles
Windows update titles are often, but not consistently, localized against the device’s OS language. To aid users who may receive updates with titles in languages besides English, the following table will help you craft more accurate policy configurations. When using these phrases, we recommend including them in addition to their English-language analogues (as opposed to in place of them), as Microsoft does not reliably localize the titles of every update released and because certain terms (like Driver) are recognized internationally.
| English | French | German | Spanish |
|---|---|---|---|
| Update | mise à jour | Aktualisieren | actualización |
| Servicing Stack (Update) | pile de maintenance | Servicing-Stack-Update | pila de servicios |
| Feature Update | Mise à jour des fonctionnalités | Featureupdate, Funktionsupdate | Actualización de características |
| Preview | préversion | Vorschau | vista previa |
| Driver | pilote | Treiber | controlador |
| Firmware | micrologiciel |
The Manual approval section lists all updates that have been discovered from patch scans and gives users the opportunity to manually cherry-pick updates and handle them outside of how the automatic filters defined in the preceding section would have. The list is neither dynamic nor filtered.
This section should be used to ensure patches that would otherwise pass through the automatic filter do not get through to your devices. It is populated by the patch scans performed by devices with active Patch Management policies; it does not accept textual input. In the instance where a bad update is released, wait for devices to register it in their patch scans and then use this section to move it to Do not approve to ensure it is not pushed through.
Datto recommends keeping abreast of updates from sites like BleepingComputer or AskWoody to find out about issues with recent Windows Updates, the news from which can be translated as required to this section to work alongside patch deferral.
Datto does not recommend attempting to remove Windows Updates once they have been installed. In most cases, this option is not supported and can cause system instability.
Generally speaking, using Patch Management properly can ensure no update that has not been properly vetted gets installed on a system.
More information: Best practices for uninstallation of Windows updates
Step 3: Handling feature updates
Feature updates are what Microsoft once referred to as service packs. They update the entire OS’s release version (for example, 24H2) while keeping the base OS (for example, Windows 11) the same. While they appear within patch scans, they should generally be handled separately.
Installing via Patch Management
Feature updates have historically used a different schema and therefore require special treatment, which Datto RMM is only partially able to provide.
If the update comes as an enablement package, it is generally suitable for installation via Datto RMM. These typically small-sized packages simply enable functionality which had been drip-fed in as part of prior quality updates but not yet enabled. The last few updates to Windows 10, before it was discontinued, came in the enablement package form.
Larger non-enablement package updates are generally not recommended for installation via Datto RMM. Instead, we recommend installation via a ComStore component. In addition to providing more visibility over the update process than via a policy, this allows users to schedule the exact time at which they want their devices to process a large, system-changing update.
Installing via a component
Refer to Windows 11 and feature updates.
NOTE Windows 10 is no longer receiving feature updates.
Configuring a targeted release version
Using the Configure Windows Targeted Release Version ComStore component, administrators can configure a targeted release version on Windows devices. This ensures a device will never update beyond a specific release version (for example, Windows 10 23H2) until the blocker, a series of registry values, is subsequently removed.
The component can be used to set or revert a release target. The Windows Update Toolkit component will note in a UDF if a targeted release version is set.
Other considerations
- It is recommended to patch servers and workstations separately as part of different Patch Management policies running at different times.
Some users prefer to put servers on an Audit only schedule and manually perform updates (using Save and deploy now) as opposed to using a scheduler. This allows servers with specific requirements to be catered to individually (for example, Hyper-V servers must have all guest OSs suspended before the system is rebooted).
- If you have a sufficiently large fleet of devices, you may consider putting some on seven-day deferral and more mission-critical devices on 14-day deferral. This will allow you to treat less crucial devices as test candidates before more mission-critical devices receive the same patches.
-
IMPORTANT Clustered servers should be excluded from Patch Management policies. They need to use cluster-aware update services.
Supplementary reading
- Best practices for treating workstations as servers: A guide for instances where a workstation needs to be treated as a server for the purposes of patching (that is, the device in question runs mission-critical software and cannot be rebooted outside of schedule).
- Best practices for advanced patching with site tags and UDF values: A guide for advanced users on how to delineate devices using tags and UDFs to guarantee precision in patching operations.
- Best practices controlling post-patch reboots: A guide for advanced users on how to control rebooting after patching for important devices.
- Best practices for uninstallation of Windows updates: Explains in detail why Datto RMM does not offer functionality to uninstall Windows updates and how best to work around this limitation.