Best practices for Windows Event Log monitoring
PERMISSIONS Refer to Sites > Monitor in Permissions.
NAVIGATION Device summary page > Monitors card > Create a Monitor. To learn how to access the device summary page, refer to Device summary.
Using Datto RMM to monitor the Windows Event Log is a convenient and useful way to monitor an endpoint. Refer to Event Log monitor.
Two popular types of software that often make use of the Windows Event Log are backup and antivirus software. Raising alerts for a failed backup or detected malware is an effective starting point, but what if a subsequent backup is successful or the installed antivirus application quarantines the malware? What happens with the open alert? Employing the best practice explained in the following scenario will allow you to automatically monitor for resolutions and help keep open alerts in your Datto RMM account active, relevant, and to a minimum.
Event Log monitor auto-resolution
The following Event Log monitor example depicts the use of the Windows Defender Monitoring policy to raise an alert if event 1116 is found in the Windows Defender event log. Event 1116 indicates that malware has been detected. Refer to Monitoring policy.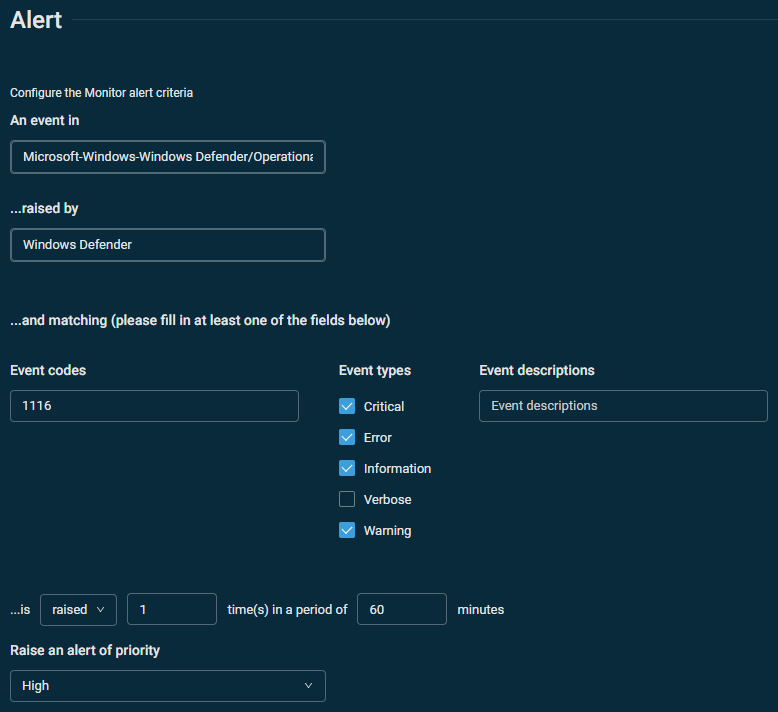
You can configure an automatic response within the Event Log monitor that will close the alert once Windows Defender successfully quarantines the malware. Refer to Auto-resolution. In the following example, if event 1117 is logged after event 1116, then Windows Defender has successfully quarantined the malware. The auto-resolution serves as an indication that the previous alert can be closed.
You can use this technique to resolve a number of Windows Event Log monitoring alerts (for example, if a previously failed backup succeeds within one hour of the failure, if detected malware is quarantined within one hour of detection, and so forth).