Create a Patch Management policy - Legacy UI
PERMISSIONS Refer to Permissions.
NAVIGATION Legacy UI > Account > Policies
NAVIGATION Legacy UI > Sites > select a site > Policies
Refer to Patch Management policy in Policies.
About Patch Management
For general information about Patch Management for Windows devices in Datto RMM, including security level permissions, determining a device's patch status, patch reporting, and more, refer to Patch Management - Legacy UI.
What is a Patch Management policy?
With a Patch Management policy, you are pre-approving patches to be installed on your Windows devices on an ongoing basis as per the conditions you define. A Patch Management policy can not only manage the patches made available in Windows Update, but it also gives you more control, lowers your workload, and increases the security of your devices.
You can set up a global or site-level policy that can target multiple devices. You can define conditions such as the patch window and patch approval rules. You can also create a Patch Management policy for audit purposes only, and apply site-level overriding of global policy options.
IMPORTANT Only Windows Managed Agents support Patch Management. Refer to Managed and OnDemand Agents.
TIP We recommend that you create at least two Patch Management policies: one for workstations and one for servers.
NOTE Patch Management support for macOS devices is available via the ComStore component Install Updates with SUPER [MAC]. For more information, refer to macOS Patch Management.
All new accounts are provisioned with a default Patch Management policy that can be found in Account > Policies. It is configured the following way: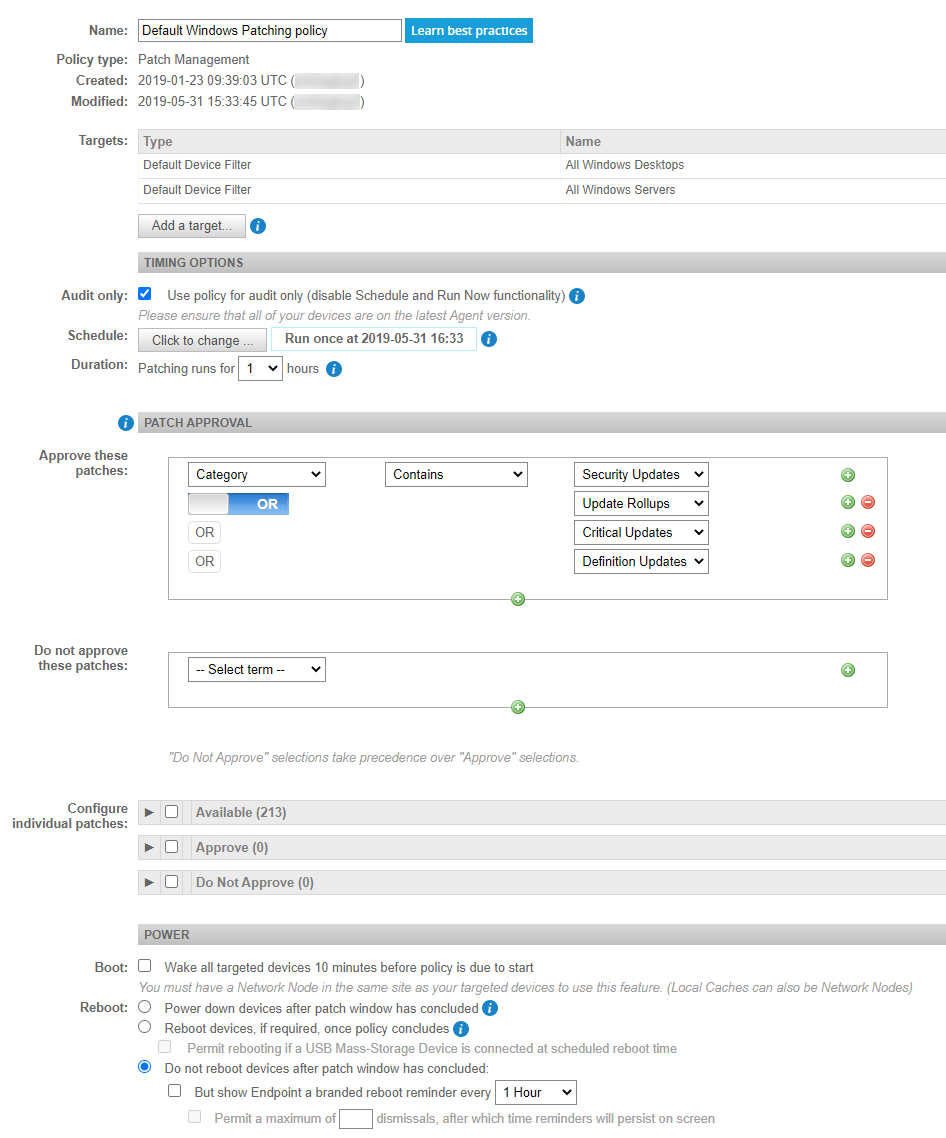
| Field | Definition |
|---|---|
| Name | Default Windows Patching policy |
| Policy Type | Patch Management |
| Targets | • Default Device Filter: All Windows Desktops • Default Device Filter: All Windows Servers |
| Timing Options | Audit only |
| Patch Approval | Approve these patches: • Category > Contains > Security Updates OR Update Rollups OR Critical Updates OR Definition Updates |
| Power | Reboot: • Do not reboot devices after patch window has concluded |
You can create another Patch Management policy or modify the default one. For more information, refer to Specify the policy details for a Patch Management policy.
How to...
- If you would like to use a Patch Management policy to install only the patches you have approved, you need to disable Automatic Windows Update on your devices. We recommend that you create a Windows Update Policy in Datto RMM to achieve this. For more information, refer to the Disable automatic Windows Updates section in Create a Windows Update policy - Legacy UI.
- You can then create a Patch Management policy at the account or site level. Refer to Specify the policy details for a Patch Management policy.
Account-level policies can be overridden at the site level to alter only the most necessary elements for a smaller subset of devices. For more information, refer to Override account-level patch policy options at the site level.
NOTE While multiple Patch Management policies can target the same device or group of devices to support different scheduling needs, it is important that the patch approval criteria remain consistent across all policies, otherwise it can lead to undesirable behavior regarding approved patch statuses and installation on individual devices.
NOTE A Default Patch Management policy is available in all new accounts. To modify the policy details or create a new policy, refer to the steps below.
- On the Policy page, click New account policy... or New site policy...
- Give the policy a Name.
- Select the type Patch Management.
-
To copy an already existing policy to use it as a template, choose it from the Based on drop-down list. To create a new policy, select New Policy.
NOTE You can only use an account-level or site-level policy as a template, that is, you cannot base your policy on a site-level override of an account-level policy. For information of site-level overrides, refer to Override account-level patch policy options at the site level.
- Click Next.
-
Click Add a target... to target your devices through a specific filter or group.
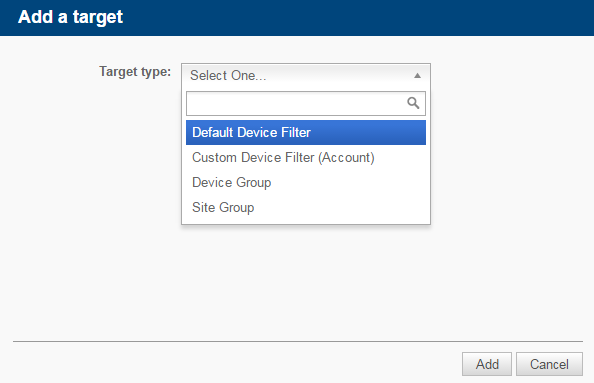
If you want to target more than one filter or group, add another target to the policy. Multiple targets will apply the "OR" logic, that is, the policy will be run on a device if it is included in any of the targets. For more information about target types, refer to Filters - Legacy UI and Groups - Legacy UI.NOTE Device filters contain all Default Device Filters and Custom Device Filters. Devices of Unknown device type will not be targeted by the policy.
- Choose one or more of the following options:
| TIMING OPTIONS | |
|---|---|
| Field | Description |
| Audit only | Select this option to use the policy for audit purposes only. This will allow you to see missing patches on your devices without the ability to (unintentionally) run the policy on them. Once this option is selected, it will disable the Schedule and Duration options below, and the Run Now functionality. For more information on Run Now, refer to Patch Management at the account and site level and Patch Management at the device level. |
| Schedule |
IMPORTANT Ensure that all of your devices are on the latest Agent version. NOTE This option will be grayed out if the Audit only option has been selected. Click the Click to change... button to set the schedule when you want the policy to run. Select one of the following:• At selected date and time - Defaults to the current date and time, but can be changed in the Start field. The policy will run once at the selected date and time. • Daily - The policy will run every day at the time indicated in the Start field. • Weekly - The policy will run every week on all selected days at the time indicated in the Start field. • Monthly - The policy will run in the selected months on the selected days. • Monthly day of week - The policy will run in the selected months on the specified occurrence of the selected days of the week. • Yearly - The job will run on the selected day (1 - 366) each year. Once you click OK, the selected schedule will be displayed next to the Click to change... button. NOTE Time zones will be taken into account at run times. For example, if the policy is set to run at midnight and it is applied to two devices in different time zones, one UTC and one PST, then the policy will run at midnight UTC on the UTC device and at midnight PST on the PST device. The policy cannot be scheduled to run at a time that has already passed in all time zones. |
| Duration |
NOTE This option will be grayed out if the Audit only option has been selected. Allows you to put a time limit (1-24 hours) on running the policy. If this time window is overrun, the targeted device will stop installing patches once the ongoing operation has completed.EXAMPLE If patches 1-10 should be installed on a device but the set time limit is reached while the installation of patch 6 is still in progress, patch 6 will be installed on the device but patch 7 will not. Patch 7 will resume during the next scheduled policy run. TIP You can run Patch Management policies outside of schedule on individual devices. For more information, refer to Patch Management at the device level. |
| PATCH APPROVAL | |
| Field | Description |
| Approve these patches | Allows you to configure approval filters. Refer to Filter patches. |
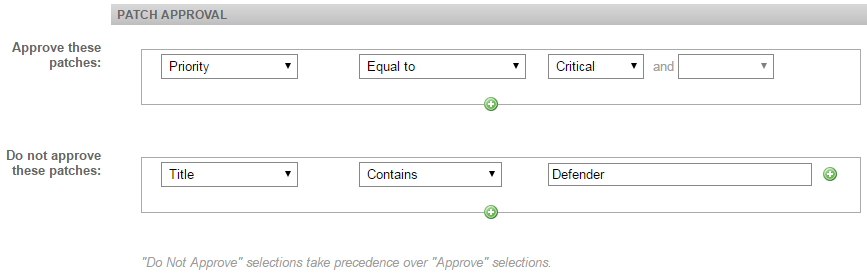
| Do not approve these patches | Allows you to configure disapproval filters, that is, you can set conditions that override your approval above. These filters take precedence over approval filters. Refer to Filter patches. For example, configurations such as “Approve critical security patches but do not approve critical security patches with ‘Defender’ in the title” are entirely possible. |
| Configure individual patches | You can use this section to manually override the patches that were approved or denied in the Approve these patches and Do not approve these patches sections above. The Configure individual patches section has three drop-down lists: Available, Approve, and Do Not Approve. The following options are available in each list: • Filter - You can filter by Microsoft Security Response Center Priorities (Critical, Important, Moderate, Low, Unspecified), May Require Reboot, and May Require User Input. For more information on Priority, refer to Filter patches. • Search - The search results are narrowed as you type. Use quotation marks to search for a whole string. For example, ".net framework 4.7" searches for patch titles containing .net framework 4.7, while searching for .net framework 4.7 without quotation marks searches for patch titles containing .net OR framework OR 4.7. Searches are not case sensitive. • Sort - You can sort the patches by clicking on any of the following columns: Title, Release date, Microsoft Security Response Center Priority, Download Size, Reboot behavior, User input. • Patch title - Click the hyperlink to open a page showing all devices across the entire account that are missing this patch / for which this patch has been approved / for which this patch has been denied (when clicking from the Available / Approve / Do Not Approve list, respectively). • • Select - You can select your patches individually by selecting the check box in front of them. You can also select all of the patches listed by checking the Select All check box just in front of the Available / Approve / Do Not Approve drop-down. • TIP If you have just moved patches from the Available list to the Approve or Do Not Approve list and want to export the updated list to a .CSV file, make sure to save the changes first and then click on the Export all patches to CSV button. This will allow you to see the updated number of patches in each list's export. Other configuration options specific to each list are discussed below. |
| Available | |
| This drop-down lists all patches that have been submitted to the platform. The number of patches is displayed in brackets next to the list name. The patches are collected from the audit data of all of the devices in the entire account/site, that is, they are not filtered by the criteria defined in the approval and disapproval sections above. This section allows you to configure individual patches regardless of any previous filters. EXAMPLE For example, you can approve a patch here that would have been excluded through a disapproval filter above. Once you have selected the required patches, you can perform the following actions that will override the approval and disapproval filters defined above:• • |
|
| Approve | |
| This drop-down lists all patches that have been approved through the Available list. The number of patches is displayed in brackets next to the list name. The patches listed are not filtered by the criteria defined in the approval and disapproval sections above. This section allows you to configure individual patches regardless of any previous filters. You can perform the following action in this list: • |
|
| Do Not Approve | |
| This drop-down lists all patches that have been denied through the Available list. The number of patches is displayed in brackets next to the list name. The patches listed are not filtered by the criteria defined in the approval and disapproval sections above. This section allows you to configure individual patches regardless of any previous filters. You can perform the following action in this list: • |
|
| POWER | |
| Field | Description |
| Boot | The following option is available: • Wake all targeted devices 10 minutes before policy is due to start - You must have a Network Node device in the same site as your targeted devices to use this feature. (Local Caches can also be nominated as Network Nodes.) If multiple Network Nodes are nominated, all will send requests. Be aware that Wake-on-LAN must be enabled in BIOS/EFI and it typically only works for laptops when they have an active mains connection. For more information, refer to Wake-on-LAN and Nominate a device as a Network Node in the legacy UI and the Network Node field in the Summary card in the New UI. NOTE Network Nodes will receive Patch Management policy definitions which have the option enabled to wake devices before patching if the devices targeted by the policy are in the same site as the Network Node. This will not be shown in the web interface but will be evident in log files. |
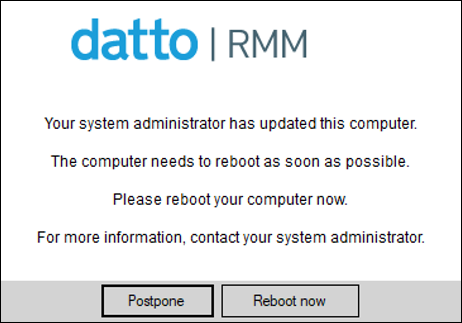
| Reboot | The following options are available: • Power down devices after patch window has concluded - It will shut down the targeted devices after the patch schedule window. • Reboot devices, if required, once policy concludes - If necessary, it will reboot the targeted devices after the policy has run. Please note that the devices will reboot once all updates have been installed and not necessarily at the end of the policy window. • Permit rebooting if a USB Mass-Storage Device is connected at scheduled reboot time - This option becomes available if the "Reboot devices..." option has been selected. Do not select this option if you want to cancel reboots when USB sticks are inserted. This will stop servers from rebooting into a LiveUSB. TIP You can always search for devices requiring a reboot using a Default Device Filter. Refer to Default Device Filter definitions. • Do not reboot devices after patch window has concluded - This option is selected by default. It will stop the targeted devices from rebooting after the patch schedule window. NOTE The reboot logo can be customized in both the legacy UI and New UI, but the reboot text and reboot buttons can be customized only in the New UI. Refer to Patch Reboot Window (legacy UI), Patch Reboot Window Logo (New UI), Reboot Text (New UI), Restart Now Button (New UI), and Postpone Button (New UI). • Permit a maximum of X dismissals, after which time reminders will persist on screen - This option becomes available if the "But show Endpoint..." option has been selected. It lets you configure how many times (maximum two-digit integer) the end user is allowed to dismiss the reboot reminder, after which they will no longer be able to dismiss it. If this option is enabled but no value is set, then the default value of 1 will be used, that is, the end user will be able to dismiss the reminder only once, and the second reminder will persist on the screen with the Postpone button becoming inactive. |
-
Click Save and Push Changes.
If you click Save Only, you'll be directed to your list of policies where you can click Push changes... next to the policy in question.
NOTE If you click Save Only (legacy UI) or Save and Deploy Later (New UI) instead of Save and Push Changes (legacy UI) or Save and Deploy Now (New UI) when creating or updating a policy, the changes will still be deployed at midnight in your time zone because policies are automatically deployed every 24 hours.
Account-level patch policies can be overridden at the site level. This allows you to change settings at the site level without modifying the master (account-level) policy.
- Navigate to any of your sites and click on the Policies tab. You will be presented with both account and site policies.
- Locate your account-level Patch Management policy and click on the Override button, or on the Edit Override button if the patch policy in question already has an active override. An active override is also indicated by the Override active
 button in front of the policy.
button in front of the policy.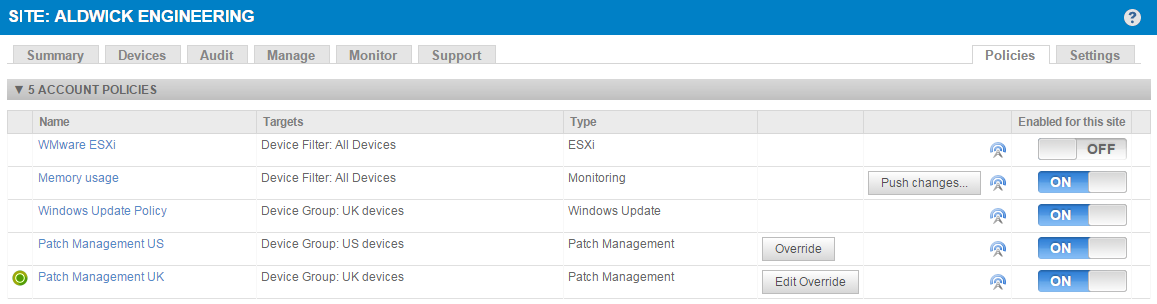
NOTE A Patch Management policy that is only active at the site level will not have an Override button (and any Override sections within the policy).
- This will open the Patch Management policy as configured at the account level, and you will have the following options:
| Field | Description |
|---|---|
| Name | These fields cannot be edited. NOTE The targets of the policy are inherited from the account-level policy. |
| Policy type | |
| Created | |
| Modified | |
| Targets | |
| TIMING OPTIONS | |
| Override | Turn it ON to be able to edit the settings below. If you turn it OFF again, the settings will revert. |
| Audit only | These sections become available as soon as the Override button is turned ON. For information on the configuration options, refer to TIMING OPTIONS. |
| Schedule | |
| Duration | |
| PATCH APPROVAL | |
| Add Rule | Turn it ON to be able to edit the settings below. If you turn it OFF again, the settings will revert. |
| Approve these patches | These sections become available as soon as the Add Rule button is turned ON. For information on the configuration options, refer to PATCH APPROVAL. |
| Do not approve these patches | |
| Configure individual patches | |
| POWER | |
| Override | Turn it ON to be able to edit the settings below. If you turn it OFF again, the settings will revert. |
| Boot | These sections become available as soon as the Override button is turned ON. For information on the configuration options, refer to POWER. |
| Reboot | |
-
Click Save and Push Changes.
If you click Save Only, you'll be directed to your list of policies where you can click Push changes... next to the policy in question.
NOTE If you click Save Only (legacy UI) or Save and Deploy Later (New UI) instead of Save and Push Changes (legacy UI) or Save and Deploy Now (New UI) when creating or updating a policy, the changes will still be deployed at midnight in your time zone because policies are automatically deployed every 24 hours.
NOTE You can also configure individual patch installations at the device level, permitting exclusions or tolerances for individual patches. Refer to Patch Management at the device level.
Your Patch Management policy can use filtering criteria to determine the patches that should be installed on the targeted devices.
You can filter by the following criteria:
| Field | Description |
|---|---|
| All | Selecting the All criterion will include all patches. |
| Category | Select any of the following categories
|
| Description | Allows you to filter by the description of the patch. Use any of the following qualifiers: Contains, Does not contain, Is empty, Is not empty, Begins with, Does not begin with, Ends with, Does not end with, Equals, Does not equal. |
| Download size | You can limit the download size of the patch to a certain number of gigabytes, megabytes, kilobytes, or exact number of bytes. Use any of the following qualifiers: Less than, Less or equal, Equal to, Greater or equal, Greater than, Between. For the between option, enter a minimum and a maximum value. NOTE You can enter whole and decimal numbers and the byte unit can be lower or upper case (for example, 4G or 3.5g). Decimal numbers without any byte unit will be rounded down to the nearest whole number and treated as bytes (for example, 1.5 will be treated as 1 byte). |
| KB number | Allows you to search for a specific Microsoft Knowledge Base article number the patch is associated with. Use any of the following qualifiers: Contains, Does not contain, Is empty, Is not empty, Begins with, Does not begin with, Ends with, Does not end with, Equals, Does not equal. |
| Priority (Microsoft Security Response Center Priority) | Allows you to filter by Microsoft Security Response Center Priority. Select any one of Critical, Important, Moderate, Low, Unspecified. Use any of the following qualifiers: Less than, Less or equal, Equal to, Greater or equal, Greater than, Between. NOTE Priority refers to Microsoft Security Response Center (MSRC) severity as specified in Microsoft Security Bulletins. Datto RMM Patch Management policies reference Security Bulletin classifications, not the severity specified by Windows Update. Refer to About Microsoft Update classifications. |
| Reboot behavior | Select from Never reboots (0), Always requires reboot (1), and Can request reboot (2). It allows you to avoid pushing changes that require a reboot during business hours. Use any of the following qualifiers: Less than, Less or equal, Equal to, Greater or equal, Greater than, Between. |
| Release date | Allows you to filter for patches released before or after a certain date, or older than 7, 14, 30, 60, or 90 days. |
| Request user input | Select either May require, or Does not require. NOTE If you filter for patches that require user input, schedule them to install during business hours. |
| Title | Allows you to filter by the name of the patch. Use any of the following qualifiers: Contains, Does not contain, Is empty, Is not empty, Begins with, Does not begin with, Ends with, Does not end with, Equals, Does not equal. |
| Type | Allows you to filter by patch type. Select either Software or Driver. |
To filter by multiple criteria:
- Click the plus sign
 below a criterion.
below a criterion. - Select the OR or AND operator.
NOTE If both conditions must be true for the patch to be included in the search results, select AND. If either one must be true, select OR.
NOTE When you add additional criteria, you cannot combine AND and OR. The selection you made first is repeated for any subsequent criterion.
- Select the next criterion.
- Click the minus sign
 to remove any of the criteria.
to remove any of the criteria.
To group queries within a criterion:
- Click the plus sign
 next to a criterion.
next to a criterion. - Select the OR or AND operator.
NOTE Standard SQL dictates that grouped queries on a positive criterion (for example, "Title contains 1", "Title contains 2", "Title contains 3") need to be grouped with OR. For example, "Title contains 1 OR 2 OR 3" will return patches whose title contains either 1 or 2 or 3.
Negative queries (for example, "Title does not contain 1", "Title does not contain 2", "Title does not contain 3") need to be grouped with AND. For example, "Title does not contain 1 AND 2 AND 3" will only return patches whose title contains neither 1 nor 2 or 3.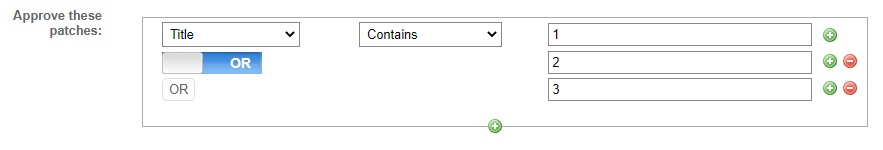
NOTE When you add additional queries, you cannot combine AND and OR. The selection you made first is repeated for the subsequent queries.
- Select the next criterion.
- Click the minus sign
 to remove any of the criteria.
to remove any of the criteria.